Storyline
Jasmine owns a famous New York coffee shop
Coffely
which is famous city-wide for its unique taste. Only Jasmine keeps the original copy of the recipe, and she only keeps it on her work laptop. Last week, James from the IT department was consulted to fix Jasmine’s laptop. But it is suspected he may have copied the secret recipes from Jasmine’s machine and is keeping them on his machine.

His machine has been confiscated and examined, but no traces could be found. The security department has pulled some important registry artifacts from his device and has tasked you to examine these artifacts and determine the presence of secret files on his machine.
Room Machine
Before moving forward, let’s deploy the machine. The machine will start in a split-screen view. In case the VM is not visible, use the blue Show Split View button at the top-right of the page. You may also access it via the AttackBox or RDP using the credentials below. It will take up to 3-5 minutes to start.
On the Desktop, there is a folder named Artifacts, which contains the registry Hives to examine and another folder named EZ tools, which includes all the required tools to analyze the artifacts.
Credentials
Username: Administrator
Password: thm_4n6
Note: If you are using Registry Explorer to parse the hives, expect some delay in loading as it takes time to parse the hives.
Registry Recap
Windows Registry is like a database that contains a lot of juicy information about the system, user, user activities, processes executed, the files accessed or deleted, etc.

Following Registry Hives have been pulled from the suspect Host and placed in the C:UsersAdministratorDesktopArtifacts folder. All required tools are also placed on the path. C:UsersAdministratorDesktopEZ Tools.
Your challenge is to examine the registry hives using the tools provided, observe the user’s activities and answer the questions.
Registry Hives
- SYSTEM
- SECURITY
- SOFTWARE
- SAM
- NTUSER.DAT
- UsrClass.dat
Note:
The
Download Task Files
button has a cheat sheet, which can be used as a reference to answer the questions.
Let’s load our Hives
Head to SYSTEM to find the name of the machine
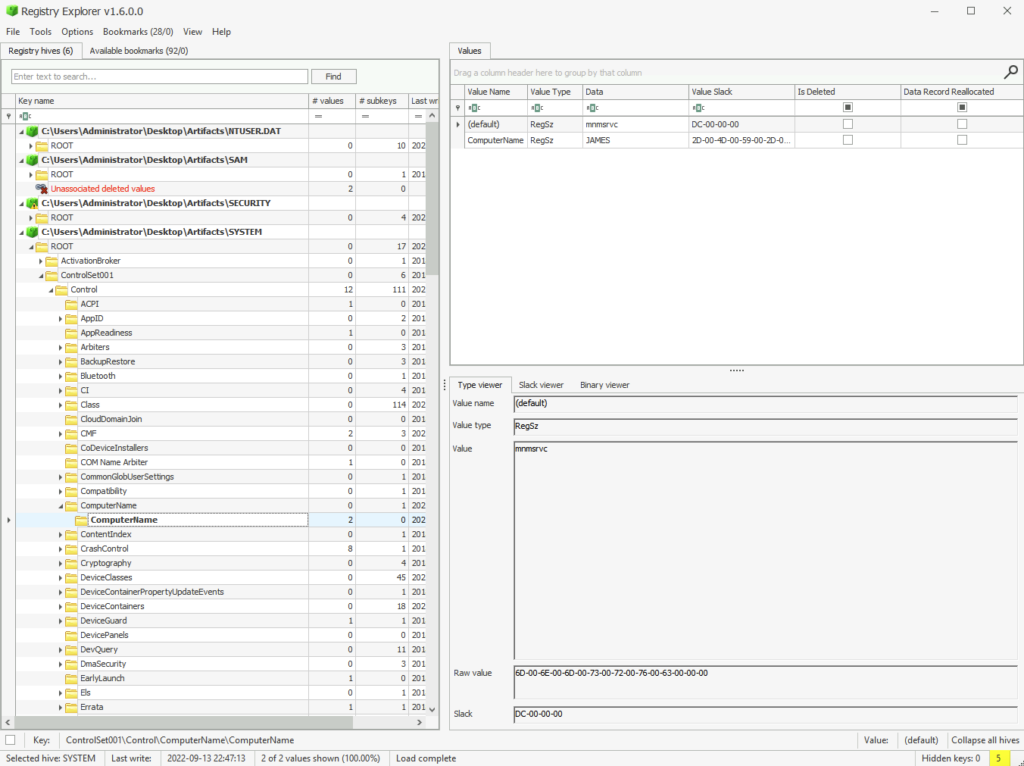
What is the Computer Name of the Machine found in the registry?
ANSWER: James
Next over to SAM for user info
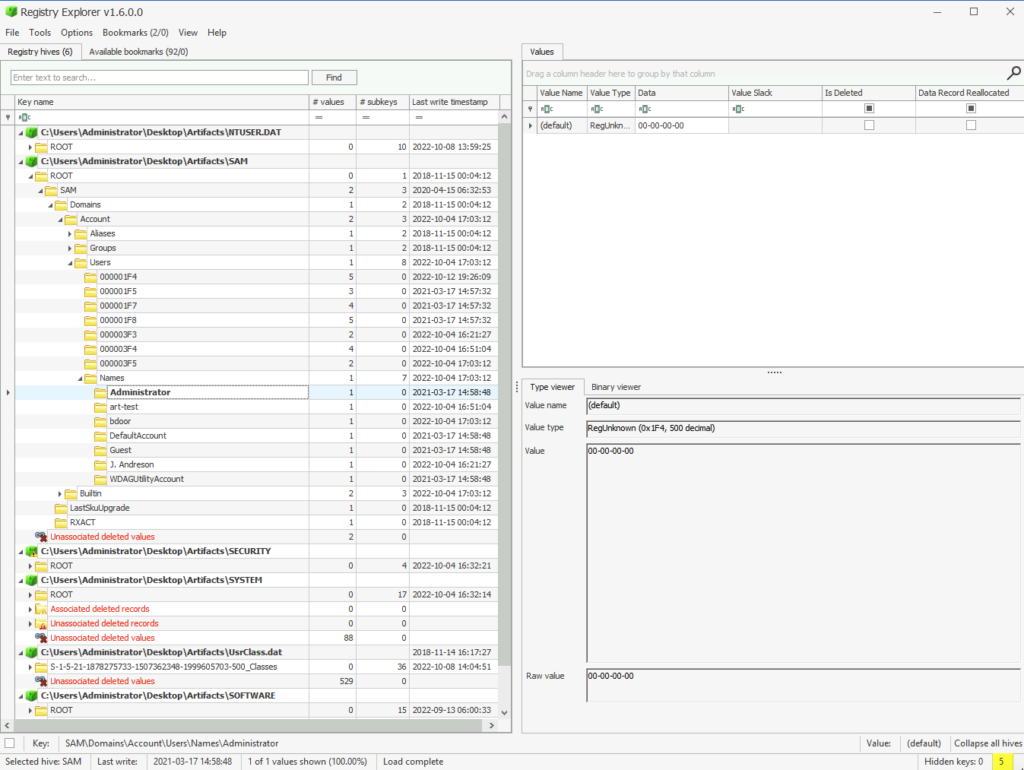
When was the Administrator account created on this machine? (Format: yyyy-mm-dd hh:mm:ss)
ANSWER: 2021-03-17 14:58:48
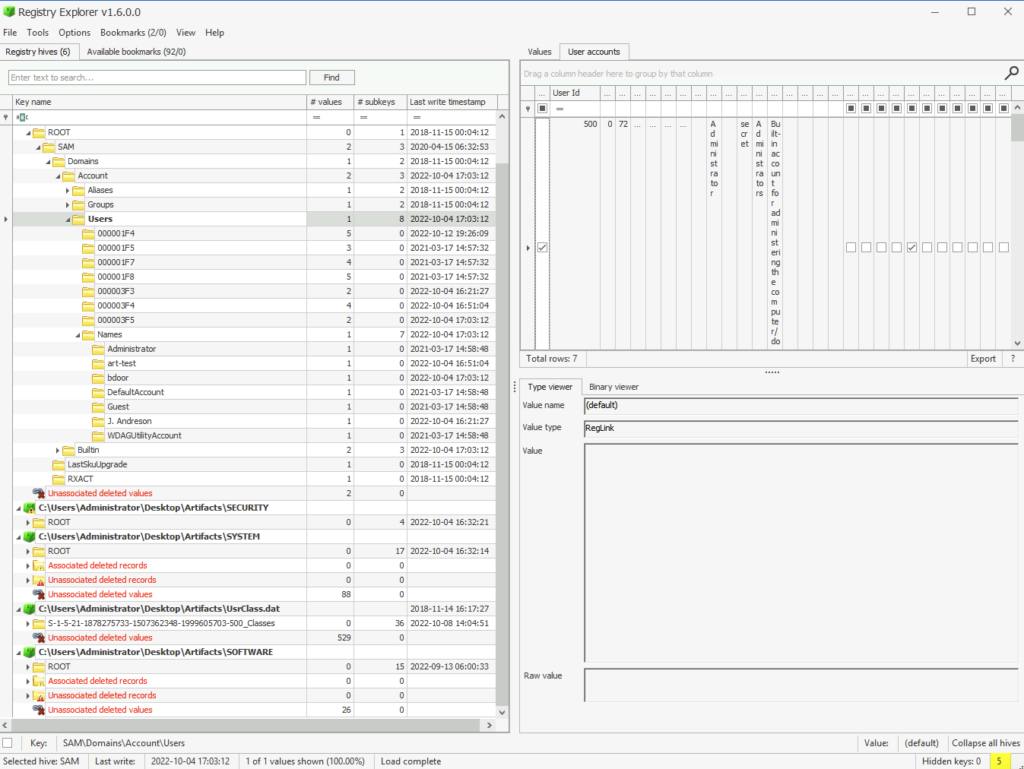
What is the RID associated with the Administrator account?
ANSWER: 500
How many User accounts were observed on this machine?
ANSWER: 7
(from same output)
There seems to be a suspicious account created as a backdoor with RID 1013. What is the Account Name?
ANSWER: bdoor
(from same output)
Over to SOFTWARE to find VPN info
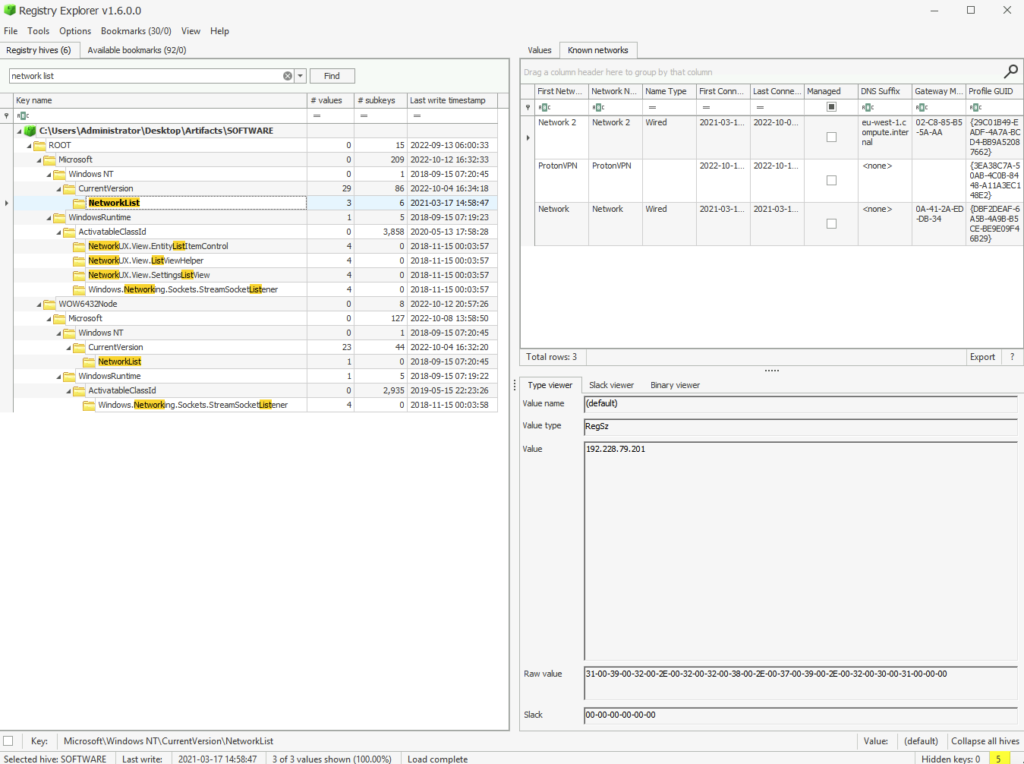
Hot tip use the searchbar, I spent a good while browsing before remembering this feature
What is the VPN connection this host connected to?
ANSWER: ProtonVPN
When was the first VPN connection observed? (Format: YYYY-MM-DD HH:MM:SS)
ANSWER: 2022-10-12 19:52:36
(from same output)
Back to SYSTEM to find shared folders
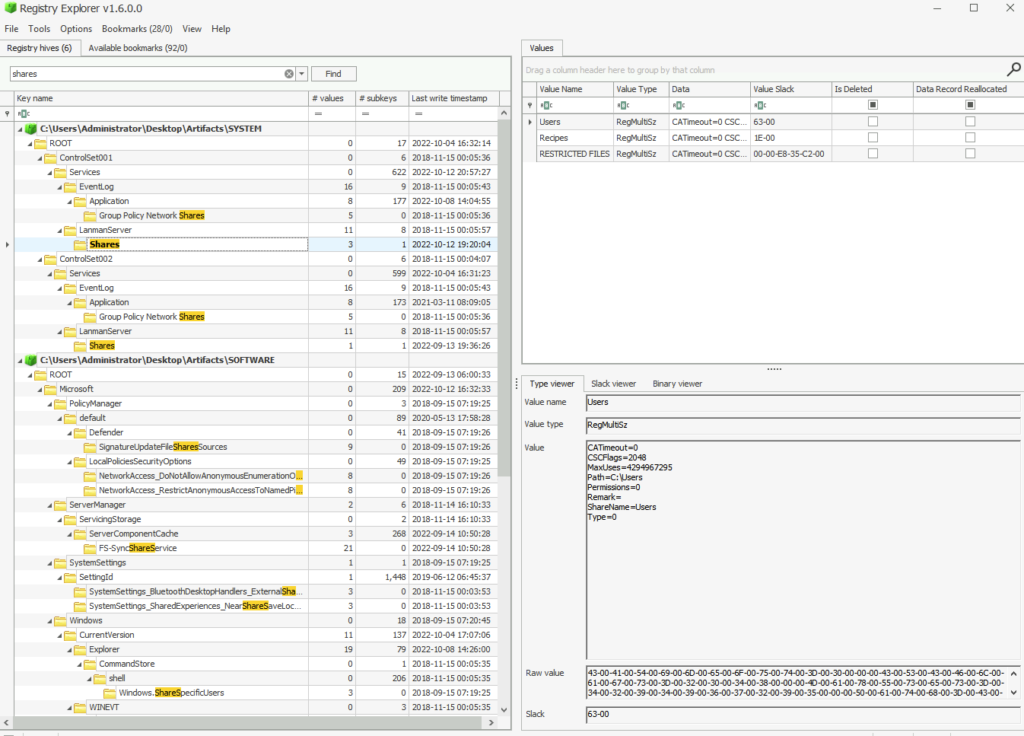
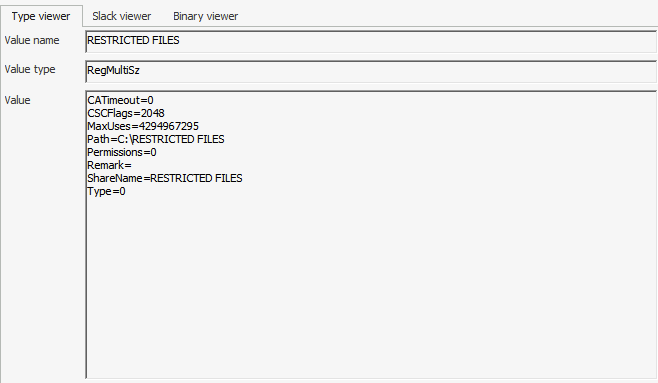
There were three shared folders observed on his machine. What is the path of the third share?
ANSWER: C:RESTRICTED FILES
Looking for TCPIP. Still within SYSTEM. Browse Interface Values
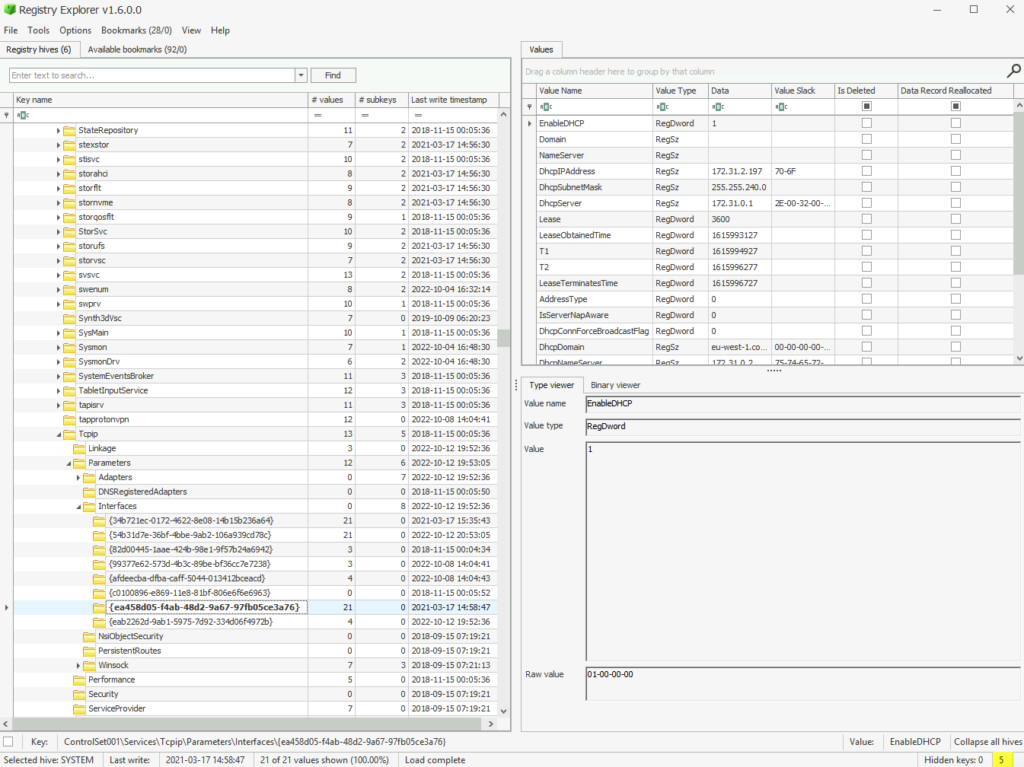
Searchbar did me dirty so I found it by browsing. SYSTEMControlSet001ServicesTcpipParametersInterfaces
What is the Last DHCP IP assigned to this host?
ANSWER: 172.31.2.197
NTUSER.DAT has recentdocs which should tell us what’s been happening.
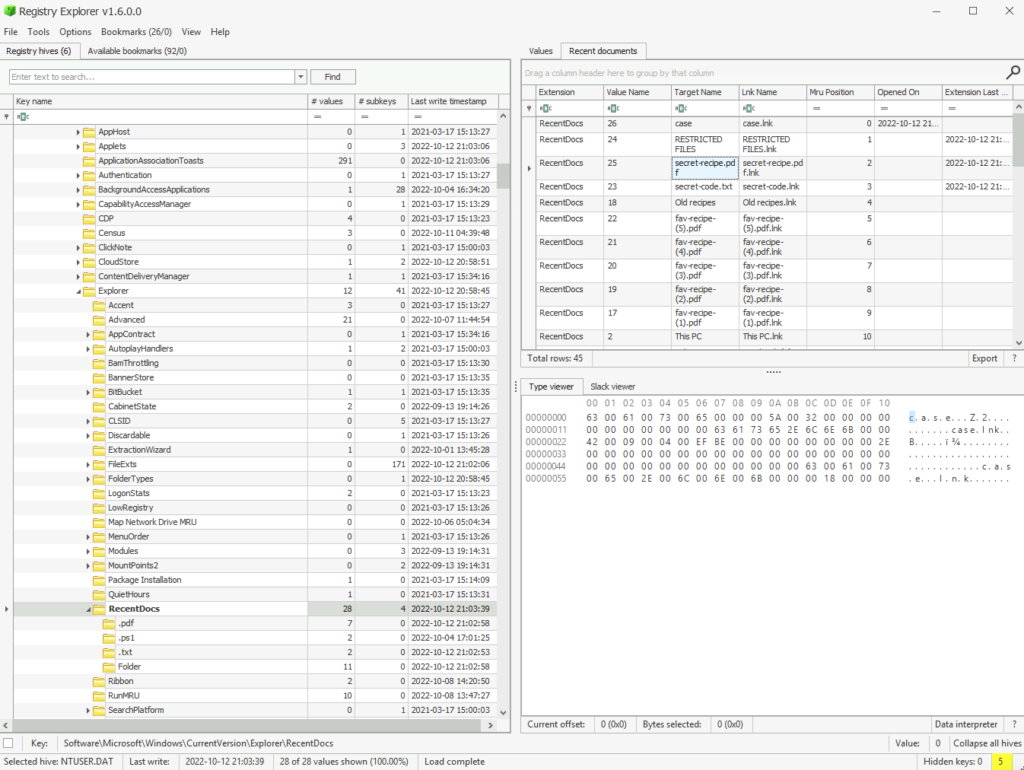
The suspect seems to have accessed a file containing the secret coffee recipe. What is the name of the file?
ANSWER: secret-recipe.pdf
Not far to go to get to the next info, close recentdocs and you will see RunMRU
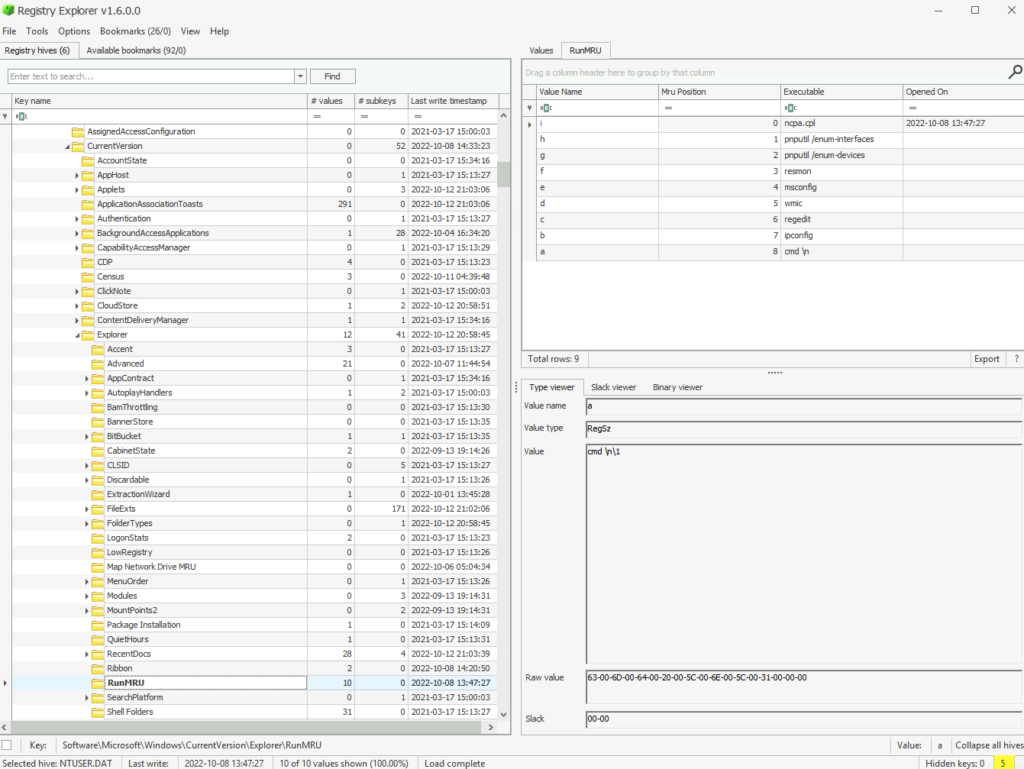
The suspect ran multiple commands in the run windows. What command was run to enumerate the network interfaces?
ANSWER: pnputil /enum-interfaces
Jump over to WordWheelQuery to see what the user has been searching for
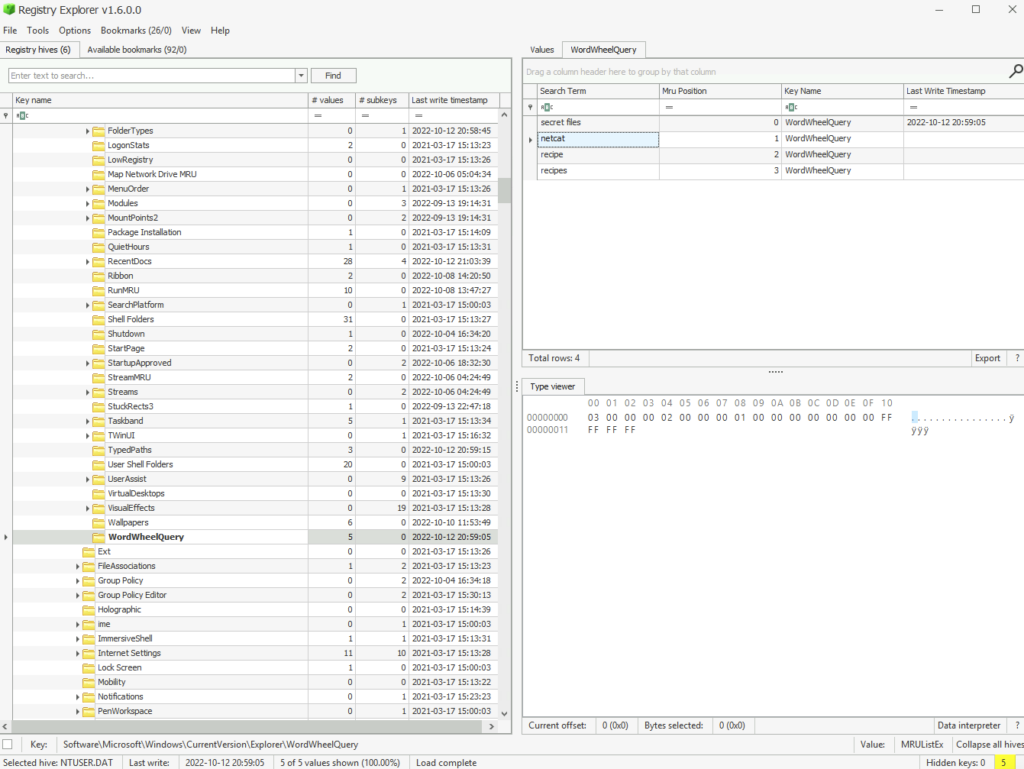
In the file explorer, the user searched for a network utility to transfer files. What is the name of that tool?
ANSWER: netcat
Back to RecentDocs
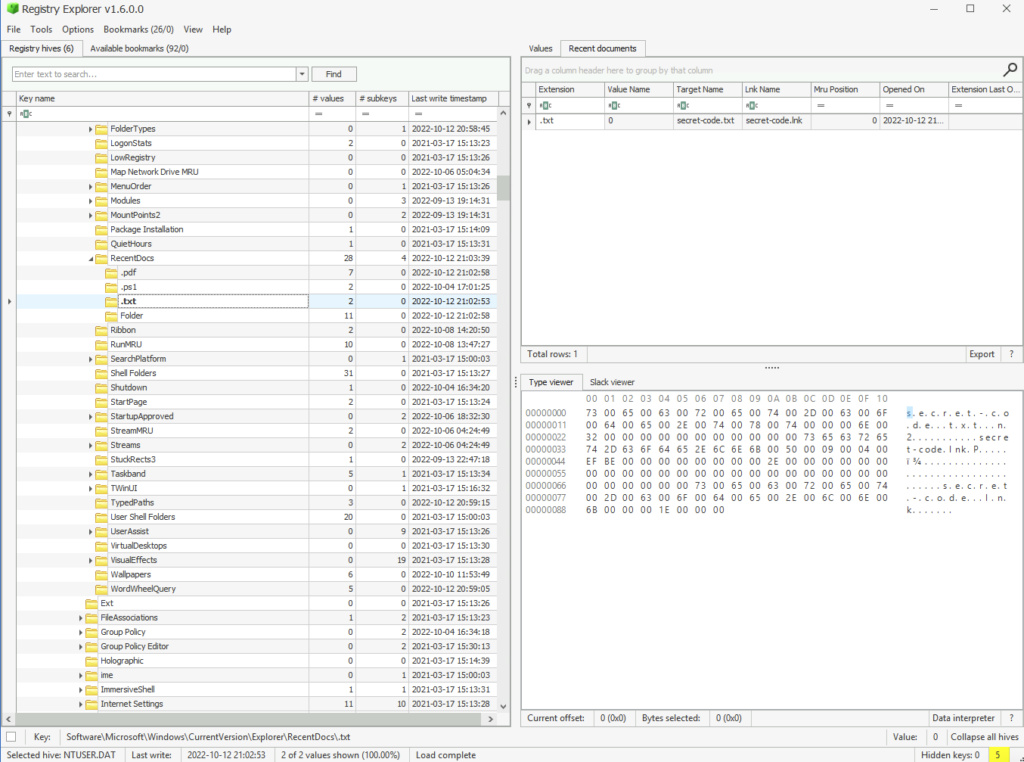
What is the recent text file opened by the suspect?
ANSWER: secret-code.txt
Head to UserAssist, you will need to dig through keys to find one with a count
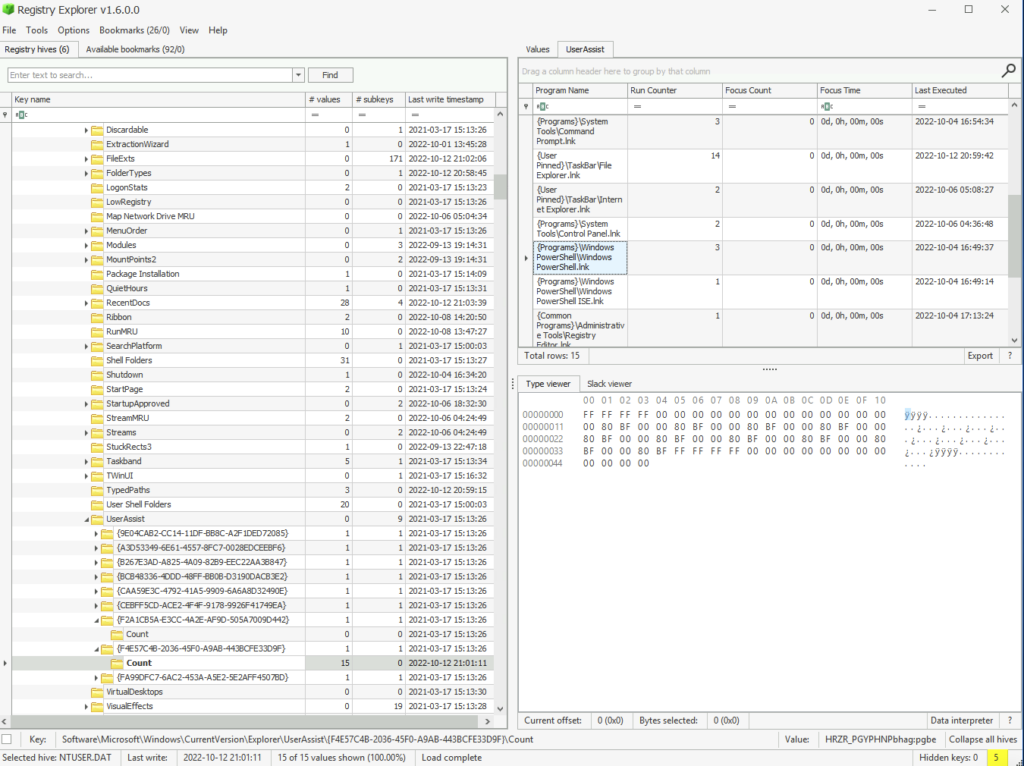
How many times was Powershell executed on this host?
ANSWER: 3
Jumped over to a key with a higher count (more activity) as I couldn’t see anything in the current one. Took some scrolling then something jumped out
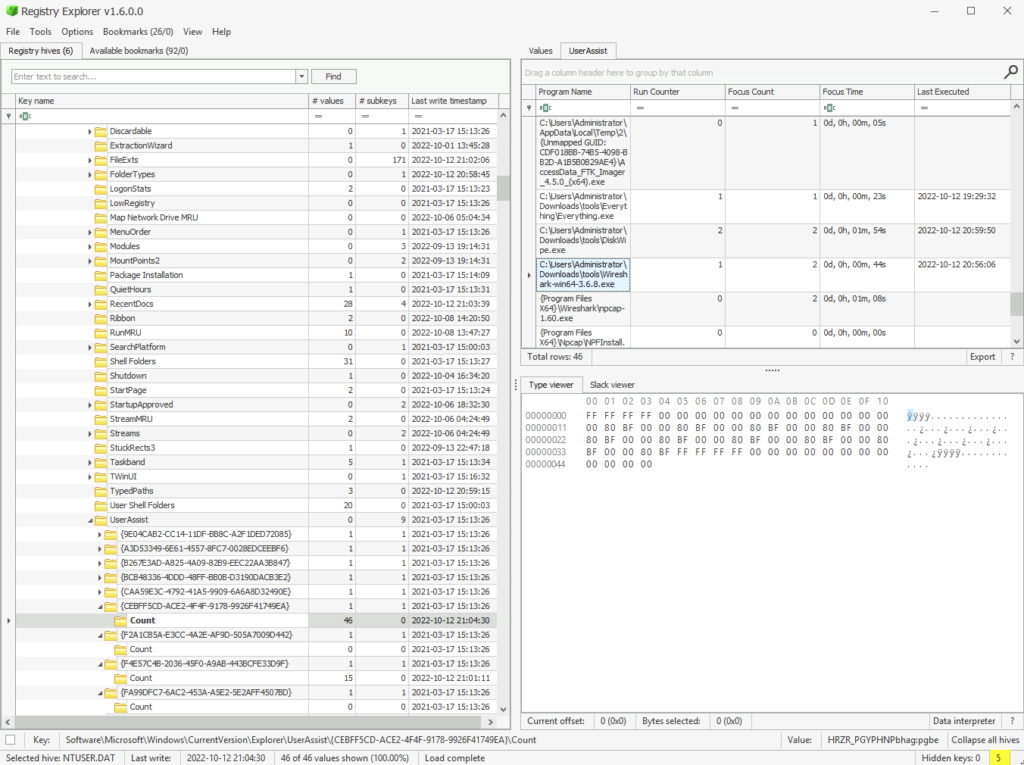
The suspect also executed a network monitoring tool. What is the name of the tool?
ANSWER: wireshark
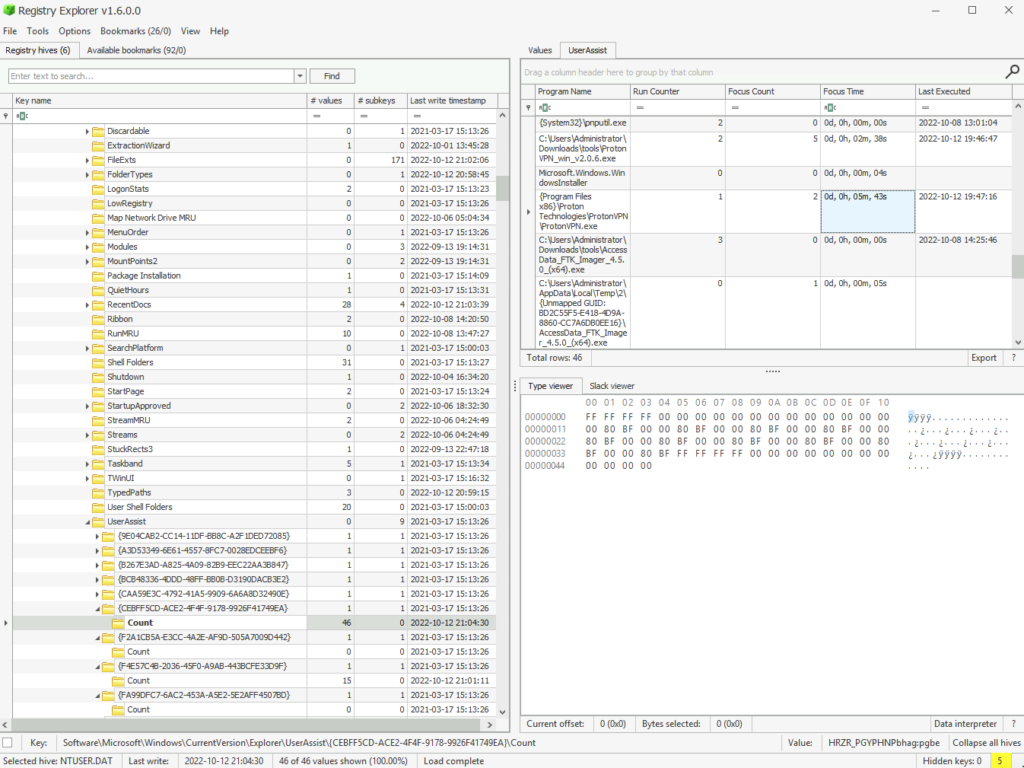
Registry Hives also notes the amount of time a process is in focus. Examine the Hives. For how many seconds was ProtonVPN executed?
ANSWER: 343
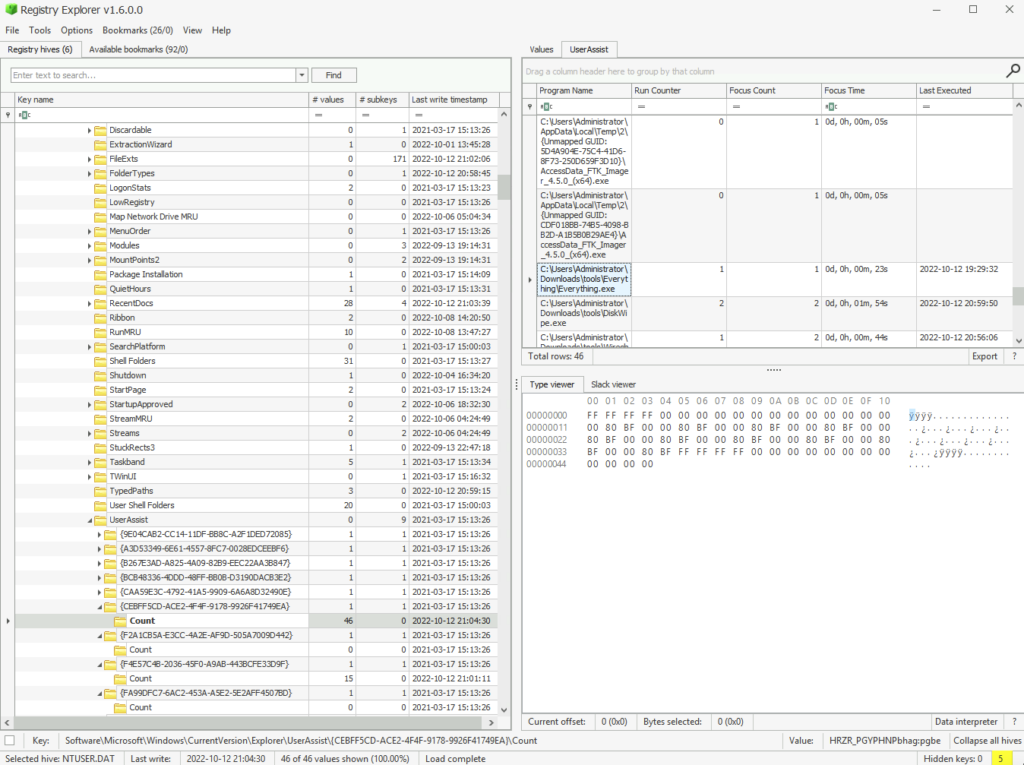
Everything.exe is a utility used to search for files in a Windows machine. What is the full path from which everything.exe was executed?
ANSWER: C:UsersAdministratorDownloadstoolsEverythingEverything.exe
Nice that the last 3 questions were all in the same spot. A lot of browsing, could go for night mode when looking that closely. Thanks for reading






Leave a Reply