In this challenge room, we will take a simple challenge to investigate an alert by IDS regarding a potential C2 communication.
Room Machine
Before moving forward, deploy the machine. When you deploy the machine, it will be assigned an IP Machine IP: MACHINE_IP. The machine will take up to 3-5 minutes to start. Use the following credentials to log in and access the logs in the Discover tab.
Username: Admin
Password: elastic123
Scenario
During normal SOC monitoring, Analyst John observed an alert on an IDS solution indicating a potential C2 communication from a user Browne from the HR department. A suspicious file was accessed containing a malicious pattern THM:{ ________ }. A week-long HTTP connection logs have been pulled to investigate. Due to limited resources, only the connection logs could be pulled out and are ingested into the connection_logs index in Kibana.
Our task in this room will be to examine the network connection logs of this user, find the link and the content of the file, and answer the questions.
How many events were returned for the month of March 2022? ANSWER: 1482
Navigate to the discover page and set the date range for the month of March
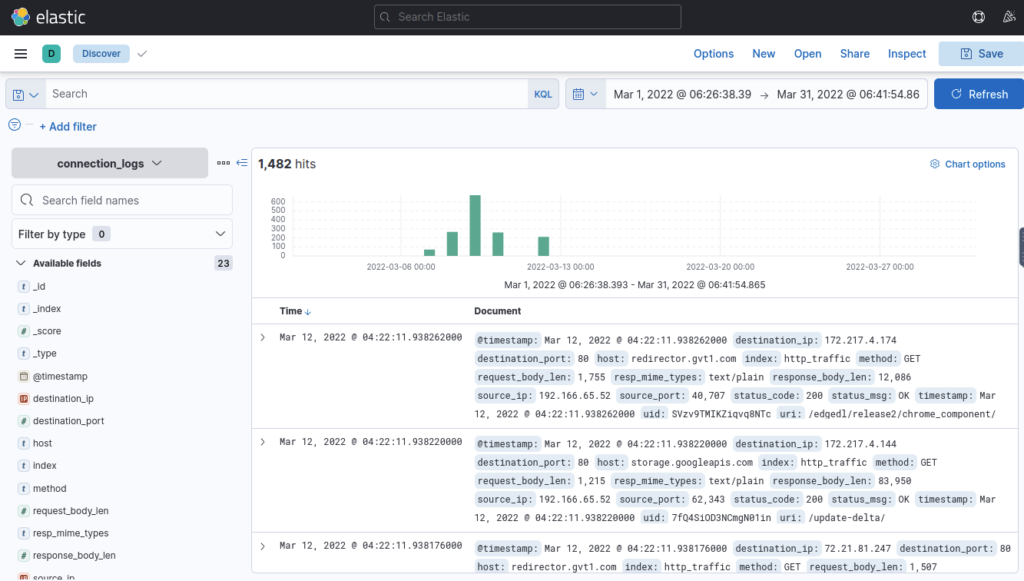
What is the IP associated with the suspected user in the logs? ANSWER: 192.166.65.54
I looked at source_ip and tried the one that is the anomaly
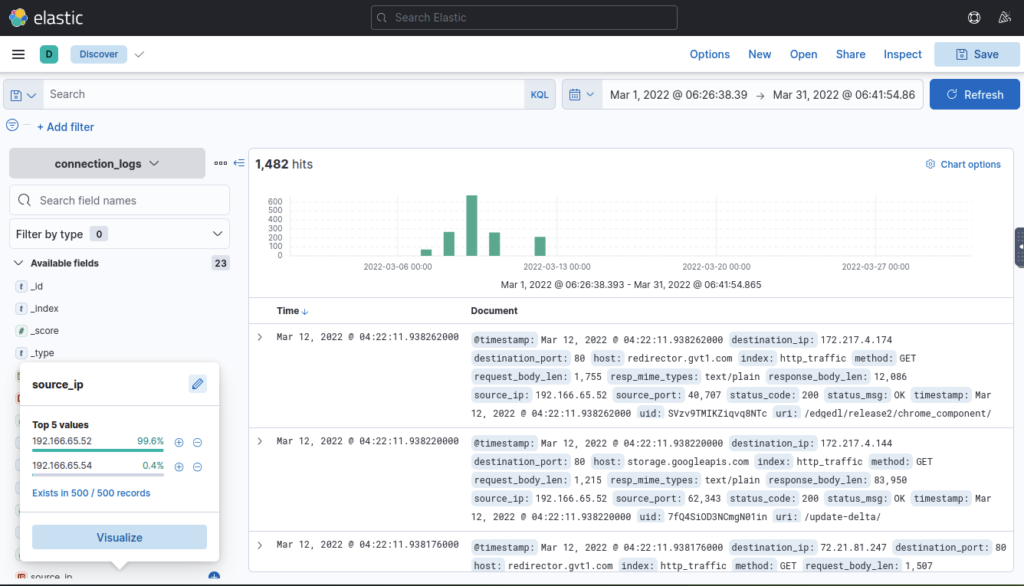
The user’s machine used a legit windows binary to download a file from the C2 server. What is the name of the binary? ANSWER: bitsadmin
I browsed the hits associated with the suspected IP to find it
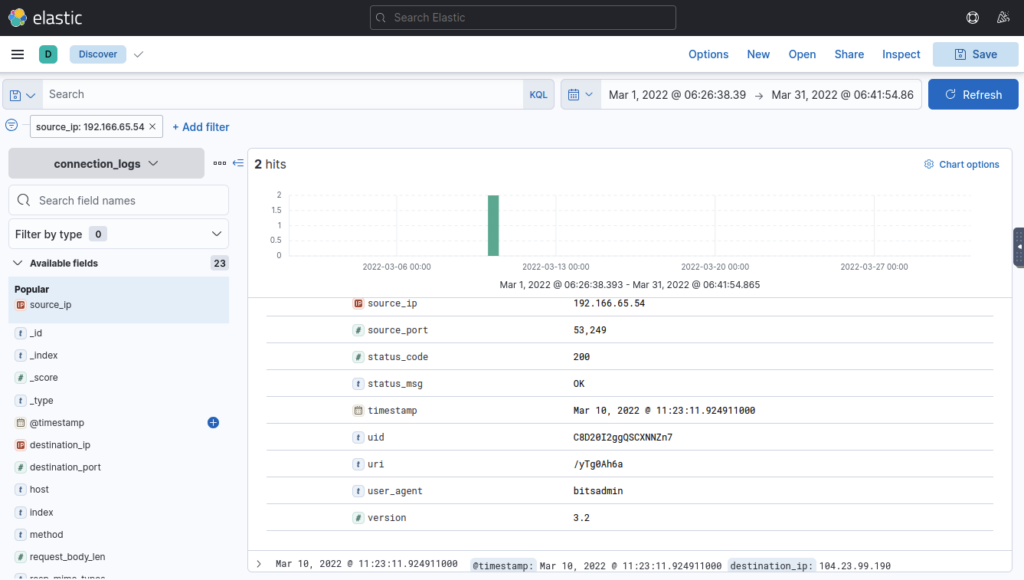
The infected machine connected with a famous filesharing site in this period, which also acts as a C2 server used by the malware authors to communicate. What is the name of the filesharing site? ANSWER: pastebin.com
At this point my attackbox froze, after a painful restart found answer slightly above the last
A file was accessed on the filesharing site. What is the name of the file accessed? ANSWER: secret.txt
I headed to the url [Within attackbox]
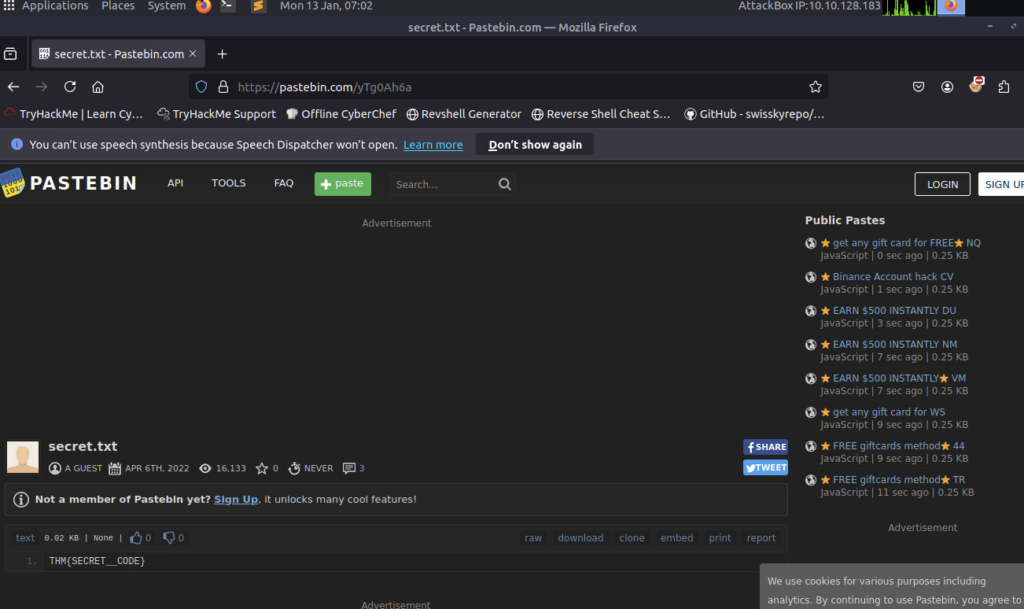
The file contains a secret code with the format THM{_____}. ANSWER: THM{SECRET_CODE}
Other than losing my connection was a pretty smooth ride. Thanks for reading.






Leave a Reply